Understanding Kerberos Snooping
Kerberos is a computer-network authentication protocol that allows entities communicating over a non-secure network to prove their identity to one another in a secure manner. Kerberos is a third-party authentication mechanism that uses a third party Kerberos server to authenticate users.
Kerberos snooping uses the Kerberos authentication technology to control network access rights of users on access devices. If an access device receives a specific Kerberos packet, it considers that the user passes the authentication and allows the user to access network resources. For details, see Kerberos Authentication Process.
Typical Networking of Kerberos Snooping
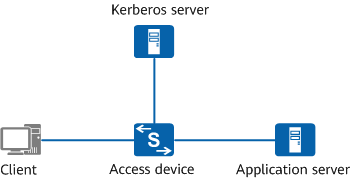
On the network shown in Figure 1, the Kerberos authentication system uses the typical client/server model and consists of four entities: client, access device, Kerberos server, and application server.
- Client: a user terminal that supports the Kerberos protocol.
- Access device: a network device that controls user access to the network.
The access device allows only DHCP, DNS, ARP, and Kerberos protocol packets to pass through before user authentication is successful.
The access device allows a user to access network resources only after the user is authenticated.
- Kerberos server: also called a key distribution center (KDC) or an authentication server, which receives authentication requests from clients.
- Application server: a device that stores network resources.
Kerberos Authentication Process
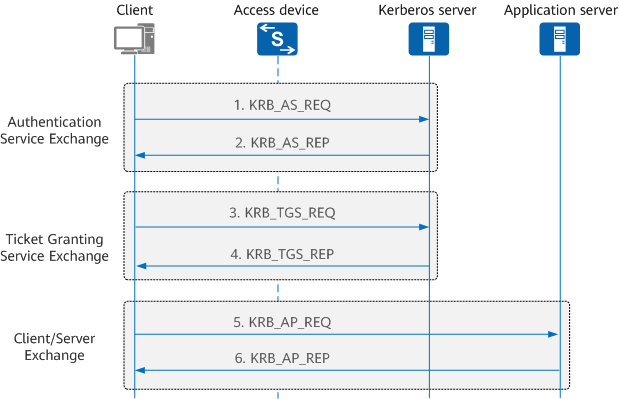
To access an application server, a client needs to obtain the ticket of the application server. As shown in Figure 2, the Kerberos authentication process consists of the following phases:
- Authentication Service Exchange: The client applies for a Ticket Granting Ticket (TGT) from the Kerberos server.
The client sends a KRB_AS_REQ packet carrying the client identity information to the Kerberos server. The Kerberos server verifies the identity of the client, and returns a KRB_AS_REP packet carrying a TGT to the client.
- Ticket Granting Service Exchange: Using the obtained TGT, the client applies to the Kerberos server for a ticket for accessing the application server.
The client sends a KRB_TGS_REQ packet to the Kerberos server to apply for a ticket for accessing the application server. The Kerberos server verifies the identity of the client, and returns a KRB_TGS_REP packet carrying the requested ticket to the client.
- Client/Server Exchange: The client submits the obtained ticket to the application server.
The client sends a KRB_AP_REQ packet containing the obtained ticket to the application server. The application server verifies the received ticket, and returns a KRB_AP_REP packet to the client to allow the client to access network resources.
The access device functions as an access control point in the entire process. It does not allow service packets of a user to pass through before the user is authenticated. The access device identifies the packets sent from a Kerberos server based on the pre-configured IP address and port number of the Kerberos server. If the access device receives a KRB_AS_REP, KRB_TGS_REP, or KRB_AP_REP packet from the Kerberos server, it considers that the user has been authenticated and allows the user to access network resources.