Example for Configuring Kerberos Snooping
Networking Requirements
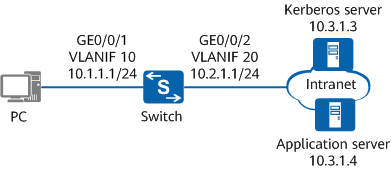
On the network shown in Figure 1, PCs in an enterprise's office area are connected to the enterprise's intranet through the switch. GE0/0/1 on the switch is directly connected to a PC in the office area, and GE0/0/2 on the switch is connected to a Kerberos server and an application server through the intranet.
To meet the high security requirements of the enterprise, PCs in the office area need to be authenticated by the Kerberos server to obtain the permission to access the application server. In addition, the switch needs to control network access rights of users, so that only authenticated users can access network resources.
Configuration Precautions
Ensure that there are reachable routes between devices. The configurations of interfaces, VLANs, and routes are not provided here.
Procedure
- Set parameters in a Kerberos snooping profile.
<HUAWEI> system-view [HUAWEI] sysname Switch [Switch] kerberos-snooping-profile name profile1 [Switch-krb-snooping-profile-profile1] server-ip 10.3.1.3 [Switch-krb-snooping-profile-profile1] port 88 [Switch-krb-snooping-profile-profile1] quit
- Bind the Kerberos snooping profile to an authentication profile.
[Switch] authentication-profile name authen1 [Switch-authen-profile-authen1] kerberos-snooping-profile profile1 [Switch-authen-profile-authen1] quit
- Apply the authentication profile to GE0/0/1.
[Switch] interface gigabitethernet 0/0/1 [Switch-GigabitEthernet0/0/1] authentication-profile authen1 [Switch-GigabitEthernet0/0/1] quit
- Verify the configuration.
- Run the display kerberos-snooping-profile command to check whether the configuration of the Kerberos snooping profile is correct.
- After a user is authenticated, run the display access-user access-type kerberos-snooping command to view information about the Kerberos user.