Example for Configuring DHCP Snooping to Prevent Bogus DHCP Server Attacks
DHCP Snooping Overview
During a process in which a DHCP client dynamically obtains an IP address, DHCP snooping analyzes and filters the DHCP packets between the client and server. Proper configuration of DHCP snooping implements filtering of unauthorized servers, preventing clients from obtaining addresses provided by the unauthorized DHCP server and failing to access the network.
- Some terminals on the network use the Windows Server 2003 or 2008 and is enabled to allocate IP addresses using DHCP by default.
- Some interfaces at the access layer are connected to the wireless router that is enabled to allocate IP addresses using DHCP.
You are advised to deploy DHCP snooping at an access switch. The interface control is accurate if you deploy DHCP snooping on a switch closer to the PC. Each switch interface should be connected to only one PC. If a certain interface is connected to multiple PCs through a hub, DHCP snooping attacks occurring on the hub cannot be prevented because the snooping packets are directly forwarded between the hub interfaces and cannot be controlled through DHCP snooping deployed on the access switch.
Configuration Notes
In V100R006C05, the S2700-SI does not support DHCP snooping. All models in other versions are applicable to this example.
Networking Requirements
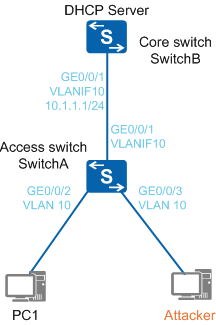
As shown in Figure 1, SwitchA is an access switch and its connected PC obtains an IP address through DHCP. SwitchB as a core switch is deployed with the DHCP server function. DHCP snooping needs to be configured to prevent unauthorized DHCP servers such as built-in wireless routers from accessing the network. If an unauthorized DHCP server is connected to the network, common users obtain incorrect addresses and cannot access the network or they obtain conflicting addresses.
Configuration Roadmap
The configuration roadmap is as follows:
- Deploy the DHCP server function on SwitchB.
- Enable global DHCP snooping on SwitchA, enable DHCP snooping on the interface connected to the PC, and configure the interface connected to SwitchB as a trusted interface. (The trusted interface receives the DHCP response packets from the DHCP server. SwitchA sends the DHCP request packets from the PC to SwitchB only through the trusted interface.)
Procedure
- Configure the DHCP server function.
# Configure the DHCP server function on SwitchB.
<HUAWEI> system-view [HUAWEI] sysname SwitchB [SwitchB] vlan batch 10 [SwitchB] interface gigabitethernet 0/0/1 [SwitchB-GigabitEthernet0/0/1] port link-type trunk [SwitchB-GigabitEthernet0/0/1] port trunk allow-pass vlan 10 [SwitchB-GigabitEthernet0/0/1] quit [SwitchB] dhcp enable [SwitchB] interface vlanif 10 [SwitchB-Vlanif10] ip address 10.1.1.1 255.255.255.0 [SwitchB-Vlanif10] dhcp select interface //Enable the device to allocate IP addresses based on the interface address pool. [SwitchB-Vlanif10] quit
- Configure DHCP snooping.
# Configure DHCP snooping on SwitchA.
<HUAWEI> system-view [HUAWEI] sysname SwitchA [SwitchA] vlan batch 10 [SwitchA] interface gigabitethernet 0/0/1 [SwitchA-GigabitEthernet0/0/1] port link-type trunk [SwitchA-GigabitEthernet0/0/1] port trunk allow-pass vlan 10 [SwitchA-GigabitEthernet0/0/1] quit [SwitchA] interface gigabitethernet 0/0/2 [SwitchA-GigabitEthernet0/0/2] port link-type access [SwitchA-GigabitEthernet0/0/2] port default vlan 10 [SwitchA-GigabitEthernet0/0/2] quit [SwitchA] interface gigabitethernet 0/0/3 [SwitchA-GigabitEthernet0/0/3] port link-type access [SwitchA-GigabitEthernet0/0/3] port default vlan 10 [SwitchA-GigabitEthernet0/0/3] quit [SwitchA] dhcp enable [SwitchA] dhcp snooping enable ipv4 //Enable global DHCP snooping, and configure the device to process only DHCPv4 packets to save the CPU usage. [SwitchA] interface gigabitethernet 0/0/2 [SwitchA-GigabitEthernet0/0/2] dhcp snooping enable //Enable DHCP snooping on the user-side interface. [SwitchA-GigabitEthernet0/0/2] quit [SwitchA] interface gigabitethernet 0/0/3 [SwitchA-GigabitEthernet0/0/3] dhcp snooping enable [SwitchA-GigabitEthernet0/0/3] quit [SwitchA] interface gigabitethernet 0/0/1 [SwitchA-GigabitEthernet0/0/1] dhcp snooping trusted //Configure the interface as a trusted interface so that the access switch can process only the DHCP server Response packets received from the interface. [SwitchA-GigabitEthernet0/0/1] quit
- Verify the configuration.
# Run the display dhcp snooping configuration command on SwitchA to check the DHCP snooping configuration.
[SwitchA] display dhcp snooping configuration # dhcp snooping enable ipv4 # interface GigabitEthernet0/0/1 dhcp snooping trusted # interface GigabitEthernet0/0/2 dhcp snooping enable # interface GigabitEthernet0/0/3 dhcp snooping enable #
# Run the display ip pool interface vlanif10 used command on SwitchB to check the used IP addresses in the address pool.
[SwitchB] display ip pool interface vlanif10 used Pool-name : Vlanif10 Pool-No : 1 Lease : 1 Days 0 Hours 0 Minutes Domain-name : - DNS-server0 : - NBNS-server0 : - Netbios-type : - Position : Interface Status : Unlocked Gateway-0 : 10.1.1.1 Network : 10.1.1.0 Mask : 255.255.255.0 VPN instance : -- ----------------------------------------------------------------------------- Start End Total Used Idle(Expired) Conflict Disable ----------------------------------------------------------------------------- 10.1.1.1 10.1.1.254 253 1 252(0) 0 0 ----------------------------------------------------------------------------- Network section : ----------------------------------------------------------------------------- Index IP MAC Lease Status ----------------------------------------------------------------------------- 253 10.1.1.254 0021-cccf-b67f 46 Used -----------------------------------------------------------------------------# Run the display dhcp snooping user-bind all command on SwitchA to check the DHCP snooping binding table.
[SwitchA] display dhcp snooping user-bind all DHCP Dynamic Bind-table: Flags:O - outer vlan ,I - inner vlan ,P - Vlan-mapping IP Address MAC Address VSI/VLAN(O/I/P) Interface Lease -------------------------------------------------------------------------------- 10.1.1.254 0021-cccf-b67f 10 /-- /-- GE0/0/2 2014.09.21-09:33 -------------------------------------------------------------------------------- Print count: 1 Total count: 1The IP addresses obtained by all the subsequent PCs through DHCP can be allocated only by SwitchB.
Configuration Files
Configuration file of SwitchA
# sysname SwitchA # vlan batch 10 # dhcp enable # dhcp snooping enable ipv4 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 10 dhcp snooping trusted # interface GigabitEthernet0/0/2 port link-type access port default vlan 10 dhcp snooping enable # interface GigabitEthernet0/0/3 port link-type access port default vlan 10 dhcp snooping enable # return
Configuration file of SwitchB
# sysname SwitchB # vlan batch 10 # dhcp enable # interface Vlanif10 ip address 10.1.1.1 255.255.255.0 dhcp select interface # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 10 # return