Example for Configuring STelnet Login (Based on RADIUS Authentication)
Overview
The Secure Shell (SSH) protocol implements secure remote login on insecure networks, which ensures data integrity and reliability and guarantees secure data transmission. STelnet, based on the SSH protocol, ensures information security and provides powerful authentication function. STelnet protects a switch against attacks such as IP spoofing. By default, you cannot log in to a switch using STelnet. You need to log in to a switch using a console port or Telnet, and configure the STelnet function and user interface parameters first.
RADIUS uses the client/server model in distributed mode and protects a network against unauthorized access. It is often used on networks that require high security and remote user access control. After STelnet login based on RADIUS authentication is configured, a switch sends the user name and password of a login user to the RADIUS server. The RADIUS server then authenticates the user and records the user operations, ensuring network security.
Configuration Notes
- STelnet V1 is an insecure protocol. Using STelnet V2 is recommended.
- Ensure that the user terminal has SSH server login software installed before configuring STelnet login. In this example, the third-party software PuTTY is used as the SSH server login software.
- Ensure that the user terminal has reachable routes to the switch and RADIUS server.
- Ensure that the IP address, port number, and shared key of the RADIUS server are configured correctly on the switch and are the same as those on the RADIUS server.
- Ensure that a user has been configured on the RADIUS server. In this example, the user admin@huawei.com (in the format of user name@domain name) and password Huawei@1234 have been configured.
- This example applies to all versions of all S series switches.

The following uses the command lines and outputs of the S7700 running V200R006C00 as an example.
Networking Requirements
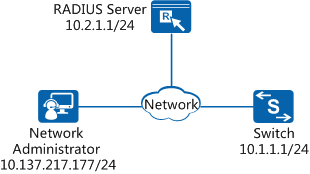
The network administrator requires remote login to a switch and high network security for protecting the network against unauthorized access. To meet the requirements, configure STelnet login based on RADIUS authentication.
As shown in Figure 1, the Switch functions as the SSH server and has a reachable route to the RADIUS server. The IP address and port number of the RADIUS server are 10.2.1.1/24 and 1812 respectively.
Configuration Roadmap
The configuration roadmap is as follows:
Generate a local key pair on the SSH server to implement secure data exchange between the server and client.
Configure the STelnet protocol so that users can log in to the Switch using STelnet.
Configure the RADIUS protocol to implement RADIUS authentication. After the configuration is complete, you can use the user name and password configured on the RADIUS server to log in to the Switch using STelnet, ensuring user login security.
Procedure
- Configure STelnet login.
# Generate a local key pair on the server.
<HUAWEI> system-view [HUAWEI] sysname Switch [HUAWEI] dsa local-key-pair create //Generate a local DSA key pair. Info: The key name will be: HUAWEI_Host_DSA. Info: The key modulus can be any one of the following : 1024, 2048. Info: If the key modulus is greater than 512, it may take a few minutes. Please input the modulus [default=2048]: Info: Generating keys... Info: Succeeded in creating the DSA host keys.
# Configure the VTY user interface.
[Switch] stelnet server enable //Enable the STelnet server function. [Switch] user-interface vty 0 14 //Enter the user interface views of VTY 0 to VTY 14. [Switch-ui-vty0-14] user privilege level 15 //Set the level of users in VTY 0 to VTY 14 to 15. [Switch-ui-vty0-14] authentication-mode aaa //Set the authentication mode of users in VTY 0 to VTY 14 to AAA. [Switch-ui-vty0-14] protocol inbound ssh //Configure the user interface views in VTY 0 to VTY 14 to support SSH. [Switch-ui-vty0-14] quit
# Set the authentication mode of the SSH user admin to password authentication, and service type to STelnet.
[Switch] ssh user admin authentication-type password //Set the authentication of the SSH user admin to password authentication. [Switch] ssh user admin service-type stelnet //Set the service type of the SSH user admin to STelnet.

To configure password authentication for multiple SSH users, run the ssh authentication-type default password command to specify password authentication as the default authentication mode of SSH users. After this configuration is complete, you do not need to configure the authentication mode and service type for each SSH user, simplifying configuration and improving efficiency.
- Configure RADIUS authentication.
# Configure a RADIUS server template on the Switch to implement communication with the RADIUS server.
[Switch] radius-server template 1 //Enter the RADIUS server template view. [Switch-radius-1] radius-server authentication 10.2.1.1 1812 //Configure the RADIUS server. [Switch-radius-1] radius-server shared-key cipher Huawei@6789 //Set the shared key of the RADIUS server to Huawei@6789. [Switch-radius-1] quit

If the RADIUS server does not support a user name containing the domain name, run the undo radius-server user-name domain-included command to configure the Switch to send packets carrying a user name without the domain name to the RADIUS server.
# Configure an AAA authentication scheme, with the authentication mode being RADIUS.[Switch] aaa [Switch-aaa] authentication-scheme sch1 //Create an authentication scheme named sch1. [Switch-aaa-authen-sch1] authentication-mode radius //Set the authentication mode to RADIUS. [Switch-aaa-authen-sch1] quit
# Create a domain, and apply the AAA authentication scheme and RADIUS server template in the domain.[Switch-aaa] domain huawei.com //Create a domain named huawei.com and enter the domain view. [Switch-aaa-domain-huawei.com] authentication-scheme sch1 //Configure the authentication scheme sch1 for the domain. [Switch-aaa-domain-huawei.com] radius-server 1 //Apply the RADIUS server template 1 to the domain. [Switch-aaa-domain-huawei.com] quit [Switch-aaa] quit
# Configure the domain huawei.com as the default global management domain so that an administrator does not need to enter the domain name for logging in to the Switch.[Switch] domain huawei.com admin
- Verify the configuration.
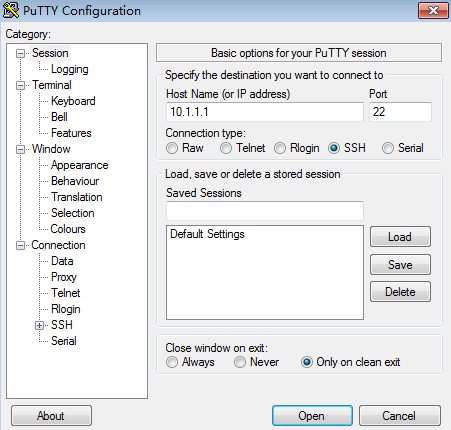
# Log in to the Switch using PuTTY on the PC. Enter the IP address of the Switch and set the protocol type to SSH, as shown in Figure 2.
# Click Open. In the login interface, type the user name admin and password Huawei@1234 as prompted and press Enter. Authentication succeeds, and you successfully log in to the Switch using STelnet. (The following information is only for reference.)
login as: admin password: Info: The max number of VTY users is 8, and the number of current VTY users online is 2. The current login time is 2014-07-30 09:54:02+08:00. <Switch>
Configuration Files
Switch configuration file
# sysname Switch # domain huawei.com admin # radius-server template 1 radius-server shared-key cipher %^%#}+ysUO*B&+p'NRQR0{ZW7[GA*Z*!X@o:Va15dxQAj+,$>NP>63de|G~ws,9G%^%# radius-server authentication 10.2.1.1 1812 weight 80 # aaa authentication-scheme sch1 authentication-mode radius domain huawei.com authentication-scheme sch1 radius-server 1 # user-interface vty 0 14 authentication-mode aaa user privilege level 15 # stelnet server enable ssh user admin ssh user admin authentication-type password ssh user admin service-type stelnet # return