Example for Configuring the Device as the STelnet Client to Log In to Another Device
Networking Requirements
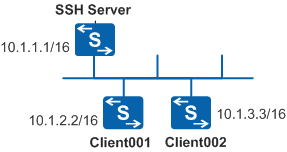
The enterprise requires that secure data exchange should be performed between the server and client. As shown in Figure 1, two login users client001 and client002 are configured and they use the password and DSA authentication modes respectively to log in to the SSH server.

The STelnet V1 protocol poses a security risk, and therefore the STelnet V2 mode is recommended.
Configuration Roadmap
The configuration roadmap is as follows:
Generate a local key pair on the SSH server to implement secure data exchange between the server and client.
Configure different authentication modes for the SSH users client001 and client002 on the SSH server.
Enable the STelnet service on the SSH server.
Configure the STelnet server type for the SSH users client001 and client002 on the SSH server.
Log in to the SSH server as the client001 and client002 users through STelnet.
Procedure
- Generate a local key pair on the server.
<HUAWEI> system-view [HUAWEI] sysname SSH Server [SSH Server] dsa local-key-pair create Info: The key name will be: SSH Server_Host_DSA. Info: The DSA host key named SSH Server_Host_DSA already exists. Info: The key modulus can be any one of the following : 1024, 2048. Info: If the key modulus is greater than 512, it may take a few minutes. Please input the modulus [default=2048]: Info: Generating keys........ Info: Succeeded in creating the DSA host keys.
- Create an SSH user on the server.
# Configure the VTY user interface.
[SSH Server] user-interface vty 0 4 [SSH Server-ui-vty0-4] authentication-mode aaa [SSH Server-ui-vty0-4] protocol inbound ssh [SSH Server-ui-vty0-4] quit
Create an SSH user named client001.
# Create an SSH user named client001 and configure the password authentication mode for the user.
[SSH Server] aaa [SSH Server-aaa] local-user client001 password irreversible-cipher Huawei@123 [SSH Server-aaa] local-user client001 privilege level 3 [SSH Server-aaa] local-user client001 service-type ssh [SSH Server-aaa] quit [SSH Server] ssh user client001 [SSH Server] ssh user client001 authentication-type password
Create an SSH user named client002.
# Create an SSH user named client002 and configure the DSA authentication mode for the user.
[SSH Server] ssh user client002 [SSH Server] ssh user client002 authentication-type dsa
# Generate a local key pair for Client002.
<HUAWEI> system-view [HUAWEI] sysname client002 [client002] dsa local-key-pair create Info: The key name will be: SSH Server_Host_DSA. Info: The DSA host key named SSH Server_Host_DSA already exists. Info: The key modulus can be any one of the following : 1024, 2048. Info: If the key modulus is greater than 512, it may take a few minutes. Please input the modulus [default=2048]: Info: Generating keys........ Info: Succeeded in creating the DSA host keys.
# Check the public key in the DSA key pair generated on the client.[client002] display dsa local-key-pair public ===================================================== Time of Key pair created: 2014-03-03 16:51:28-05:13 Key name: client002_Host Key modulus : 2048 Key type: DSA encryption Key Key fingerprint: c0:52:b0:37:4c:b2:64:d1:8f:ff:a1:42:87:09:8c:6f ===================================================== Key code: 30820109 02820100 CA97BCDE 697CEDE9 D9AB9475 9E004D15 C8B95116 87B79B0C 5698C582 69A9F4D0 45ED0E53 AF2EDEC1 A09DF4BE 459E34B6 6697B85D 2191A00E 92F3A5E7 FB0E73E7 F0212432 E898D979 8EAA491E E2B69727 4B51A2BE CD86A144 16748D1E 4847A814 3FE50862 6EB1AD81 EB49A05E 64F6D186 C4E94CDB 04C53074 B839305A 7F7BCE2C 606F6C91 EA958B6D AC46C12B 8C2B1E03 98F1C09D 3AF2A69D 6867F930 DF992692 9A921682 916273FC 4DD875D4 44BC371E DDBB8F6A C0A4CDB3 ADDAE853 DB86B9FA DB13CCA9 D8CF6EC1 530CC2F5 697C4707 90829982 4339507F F354FAF9 0F9CD2C2 F7D6FF3D 901D700F F0588104 856B9592 71D773E2 E76E8EEB 431FB60D 60ABC20B 0203 010001 Host public key for PEM format code: ---- BEGIN SSH2 PUBLIC KEY ---- AAAAB3NzaC1yc2EAAAADAQABAAABAQDKl7zeaXzt6dmrlHWeAE0VyLlRFoe3mwxW mMWCaan00EXtDlOvLt7BoJ30vkWeNLZml7hdIZGgDpLzpef7DnPn8CEkMuiY2XmO qkke4raXJ0tRor7NhqFEFnSNHkhHqBQ/5QhibrGtgetJoF5k9tGGxOlM2wTFMHS4 OTBaf3vOLGBvbJHqlYttrEbBK4wrHgOY8cCdOvKmnWhn+TDfmSaSmpIWgpFic/xN 2HXURLw3Ht27j2rApM2zrdroU9uGufrbE8yp2M9uwVMMwvVpfEcHkIKZgkM5UH/z VPr5D5zSwvfW/z2QHXAP8FiBBIVrlZJx13Pi526O60Mftg1gq8IL ---- END SSH2 PUBLIC KEY ---- Public key code for pasting into OpenSSH authorized_keys file : ssh-dsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDKl7zeaXzt6dmrlHWeAE0VyLlRFoe3mwxWmMWCaan00EXtDlOvLt7BoJ30vkWeNLZml7hdIZGgDpLzpef7DnPn8CEkMuiY2XmOqkke4raXJ0tRor7NhqFEFnSNHkhHqBQ/5QhibrGtgetJoF5k9tGGxOlM2wTFMHS4OTBaf3vOLGBvbJHqlYttrEbBK4wrHgOY8cCdOvKmnWhn+TDfmSaSmpIWgpFic/xN2HXURLw3Ht27j2rApM2zrdroU9uGufrbE8yp2M9uwVMMwvVpfEcHkIKZgkM5UH/zVPr5D5zSwvfW/z2QHXAP8FiBBIVrlZJx13Pi526O60Mftg1gq8IL dsa-key[SSH Server] dsa peer-public-key dsakey001 encoding-type der [SSH Server-dsa-public-key] public-key-code begin Info: Enter "DSA key code" view, return the last view with "public-key-code end". [SSH Server-dsa-key-code] 30820109 [SSH Server-dsa-key-code] 2820100 [SSH Server-dsa-key-code] CA97BCDE 697CEDE9 D9AB9475 9E004D15 C8B95116 [SSH Server-dsa-key-code] 87B79B0C 5698C582 69A9F4D0 45ED0E53 AF2EDEC1 [SSH Server-dsa-key-code] A09DF4BE 459E34B6 6697B85D 2191A00E 92F3A5E7 [SSH Server-dsa-key-code] FB0E73E7 F0212432 E898D979 8EAA491E E2B69727 [SSH Server-dsa-key-code] 4B51A2BE CD86A144 16748D1E 4847A814 3FE50862 [SSH Server-dsa-key-code] 6EB1AD81 EB49A05E 64F6D186 C4E94CDB 04C53074 [SSH Server-dsa-key-code] B839305A 7F7BCE2C 606F6C91 EA958B6D AC46C12B [SSH Server-dsa-key-code] 8C2B1E03 98F1C09D 3AF2A69D 6867F930 DF992692 [SSH Server-dsa-key-code] 9A921682 916273FC 4DD875D4 44BC371E DDBB8F6A [SSH Server-dsa-key-code] C0A4CDB3 ADDAE853 DB86B9FA DB13CCA9 D8CF6EC1 [SSH Server-dsa-key-code] 530CC2F5 697C4707 90829982 4339507F F354FAF9 [SSH Server-dsa-key-code] 0F9CD2C2 F7D6FF3D 901D700F F0588104 856B9592 [SSH Server-dsa-key-code] 71D773E2 E76E8EEB 431FB60D 60ABC20B [SSH Server-dsa-key-code] 203 [SSH Server-dsa-key-code] 10001 [SSH Server-dsa-key-code] public-key-code end [SSH Server-dsa-public-key] peer-public-key end
# Bind the DSA public key of the STelnet client to the SSH user client002 on the SSH server.
[SSH Server] ssh user client002 assign dsa-key dsakey001
- Enable the STelnet service on the SSH server.
# Enable the STelnet service.
[SSH Server] stelnet server enable
- Configure the STelnet service type for
the client001 and client002 users.
[SSH Server] ssh user client001 service-type stelnet [SSH Server] ssh user client002 service-type stelnet
- Connect the STelnet client to the SSH server.
# Enable the first authentication function on the SSH client upon the first login.
Enable the first authentication function for Client001.
<HUAWEI> system-view [HUAWEI] sysname client001 [client001] ssh client first-time enable
Enable the first authentication function for Client002.
[client002] ssh client first-time enable
# Log in to the SSH server from Client001 in password authentication mode by entering the user name and password.
[client001] stelnet 10.1.1.1 Please input the username:client001 Trying 10.1.1.1 ... Press CTRL+K to abort Connected to 10.1.1.1 ... The server is not authenticated. Continue to access it? [Y/N] :y Save the server's public key? [Y/N] :y The server's public key will be saved with the name 10.1.1.1. Please wait... Please select public key type for user authentication [R for RSA; D for DSA; Enter for Skip publickey authentication; Ctrl_C for Can cel], Please select [R, D, Enter or Ctrl_C]:d Enter password:
Enter the password. The following information indicates that you have logged in successfully:
<SSH Server>
# Log in to the SSH server from Client002 in DSA authentication mode.
[client002] stelnet 10.1.1.1 user-identity-key dsa Please input the username:client002 Trying 10.1.1.1 ... Press CTRL+K to abort Connected to 10.1.1.1 ... Please select public key type for user authentication [R for RSA; D for DSA; Enter for Skip publickey authentication; Ctrl_C for Can cel], Please select [R, D, Enter or Ctrl_C]:d <SSH Server>
If the user view is displayed, you have logged in successfully. If the message "Session is disconnected" is displayed, the login fails.
- Verify the configuration.
Run the display ssh server status command. You can see that the STelnet service has been enabled. Run the display ssh user-information command. Information about the configured SSH users is displayed.
# Check the status of the SSH server.
[SSH Server] display ssh server status SSH version :2.0 SSH connection timeout :60 seconds SSH server key generating interval :0 hours SSH authentication retries :3 times SFTP server :Disable Stelnet server :Enable Scp server :Disable SSH server source :0.0.0.0 ACL4 number :0 ACL6 number :0
# Check information about SSH users.
[SSH Server] display ssh user-information User 1: User Name : client001 Authentication-type : password User-public-key-name : - User-public-key-type : - Sftp-directory : - Service-type : stelnet Authorization-cmd : No User 2: User Name : client002 Authentication-type : dsa User-public-key-name : dsakey001 User-public-key-type : dsa Sftp-directory : - Service-type : stelnet Authorization-cmd : No
Configuration File
SSH server configuration file
# sysname SSH Server # dsa peer-public-key dsakey001 encoding-type der public-key-code begin 30820109 02820100 CA97BCDE 697CEDE9 D9AB9475 9E004D15 C8B95116 87B79B0C 5698C582 69A9F4D0 45ED0E53 AF2EDEC1 A09DF4BE 459E34B6 6697B85D 2191A00E 92F3A5E7 FB0E73E7 F0212432 E898D979 8EAA491E E2B69727 4B51A2BE CD86A144 16748D1E 4847A814 3FE50862 6EB1AD81 EB49A05E 64F6D186 C4E94CDB 04C53074 B839305A 7F7BCE2C 606F6C91 EA958B6D AC46C12B 8C2B1E03 98F1C09D 3AF2A69D 6867F930 DF992692 9A921682 916273FC 4DD875D4 44BC371E DDBB8F6A C0A4CDB3 ADDAE853 DB86B9FA DB13CCA9 D8CF6EC1 530CC2F5 697C4707 90829982 4339507F F354FAF9 0F9CD2C2 F7D6FF3D 901D700F F0588104 856B9592 71D773E2 E76E8EEB 431FB60D 60ABC20B 0203 010001 public-key-code end peer-public-key end # aaa local-user client001 password irreversible-cipher $1a$gRNl~ukoL~0.WU)C2]~2a}Cz/Y0-u8M{j@Ql6/xHryO-Y7m{=A>kWc.-q}>*$ local-user client001 privilege level 3 local-user client001 service-type ssh # stelnet server enable ssh user client001 ssh user client001 authentication-type password ssh user client001 service-type stelnet ssh user client002 ssh user client002 authentication-type dsa ssh user client002 assign dsa-key dsakey001 ssh user client002 service-type stelnet # user-interface vty 0 4 authentication-mode aaa # returnClient001 configuration file
# sysname client001 # ssh client first-time enable # return
Client002 configuration file
# sysname client002 # ssh client first-time enable # return