Example for Managing Files Using SFTP
Overview
After a switch is configured as an SFTP server, users can communicate with the switch using SFTP. The SSH protocol can be used to ensure connection security. SFTP implements data encryption and protects data integrity, ensuring high security. Both SFTP and FTP configured for the switch.
SFTP is applicable to file management when high network security is required, and is often used for downloading logs and backing up the configuration file.
Configuration Notes
- Before managing files using SFTP, complete the following tasks:
- Ensure that routes are reachable between the terminal and the switch.
- Ensure that SSH client software is installed on the terminal.
- SFTP V1 is an insecure protocol. Using SFTP V2 or FTPS is recommended.
- This example applies to all versions of all S series switches.

The following uses the command lines and outputs of the S5720-EI running V200R008C00 as an example.
Networking Requirements
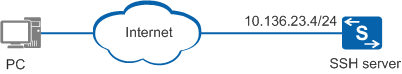
As shown in Figure 1, the PC connects to the switch, and the IP address of the management network interface on the switch is 10.136.23.4. Files need to be securely transferred between the PC and switch to prevent man-in-the-middle attacks and some network attacks (such as DNS spoofing and IP spoofing). Configure the switch as the SSH server to provide the SFTP service so that the SSH server can authenticate the client and encrypt data in bidirectional mode to ensure secure file transfer.
Configuration Roadmap
The configuration roadmap is as follows:
Generate a local key pair on the SSH server and enable the SFTP server function to implement secure data exchange between the server and client.
Configure VTY user interfaces on the SSH server.
Configure an SSH user, including the authentication mode, service type, SFTP authorized directory, user name, and password.
Use the third-party software OpenSSH to access the SSH server.
Procedure
- Generate a local key pair on the SSH server and enable
the SFTP server function.
<HUAWEI> system-view [HUAWEI] sysname SSH_Server [SSH_Server] dsa local-key-pair create //Generate a local DSA key pair. Info: The key name will be: SSH_Server_Host_DSA. Info: The key modulus can be any one of the following : 1024, 2048. Info: If the key modulus is greater than 512, it may take a few minutes. Please input the modulus [default=2048]: //Press Enter. The default key length (2048 bits) is used. Info: Generating keys... Info: Succeeded in creating the DSA host keys. [SSH_Server] sftp server enable //Enable the SFTP server function.
- # Configure VTY user interfaces on the SSH_Server.
[SSH_Server] user-interface vty 0 14 //Enter the user interface views of VTY 0 to VTY 14. [SSH_Server-ui-vty0-14] authentication-mode aaa //Set the authentication mode of users in VTY 0 to VTY 14 to AAA. [SSH_Server-ui-vty0-14] protocol inbound ssh //Configure the user interface views of VTY 0 to VTY 14 to support SSH. [SSH_Server-ui-vty0-14] quit
- Configure an SSH user, including the authentication mode,
service type, SFTP authorized directory, user name, and password.
[SSH_Server] ssh user client001 authentication-type password //Set the authentication mode to password authentication. [SSH_Server] ssh user client001 service-type sftp //Set the user service type to SFTP. [SSH_Server] ssh user client001 sftp-directory flash: //Set the SFTP service authorized directory to flash:. [SSH_Server] aaa [SSH_Server-aaa] local-user client001 password irreversible-cipher Helloworld@6789 //Set the login password to Helloworld@6789. [SSH_Server-aaa] local-user client001 privilege level 15 //Set the user level to 15. [SSH_Server-aaa] local-user client001 service-type SSH //Set the user service type to SSH. [SSH_Server-aaa] quit
- Access the SFTP server using OpenSSH.
OpenSSH commands can be used in the Windows Command Prompt window only after the OpenSSH software is installed.
 Ensure that the OpenSSH version matches the operating system of the PC. Otherwise, you may fail to access the switch using SFTP.Figure 2 Windows Command Prompt window
Ensure that the OpenSSH version matches the operating system of the PC. Otherwise, you may fail to access the switch using SFTP.Figure 2 Windows Command Prompt window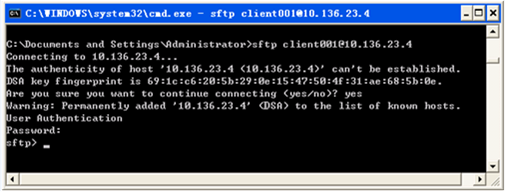
After the PC connects to the switch using the third-party software, enter the SFTP view to perform file operations.
Configuration Files
SSH_Server configuration file
# sysname SSH_Server # aaa local-user client001 password irreversible-cipher %^%#-=9Z)M,-aL$_U%#$W^1T-\}Fqpe$E<#H$J<6@KTSL/J'\}I-%^%# local-user client001 privilege level 15 local-user client001 service-type ssh # sftp server enable ssh user client001 ssh user client001 authentication-type password ssh user client001 service-type sftp ssh user client001 sftp-directory flash: # user-interface vty 0 14 authentication-mode aaa # return