Example for Accessing Files on Other Devices Using SFTP
Overview
SFTP is an SSH-based secure file transfer protocol, which uses secure connections for data transmission. After a switch is configured as an SFTP client, the remote SFTP server can authenticate the client and encrypt data in bidirectional mode to ensure secure file transfer and directory management.
SFTP is applicable to accessing files on other devices when high network security is required, and is used for uploading and downloading logs.
Configuration Notes
- Before accessing files on the SSH server using SFTP, ensure that routes are reachable between the switch and SSH server.
- SFTP V1 is an insecure protocol. Using SFTP V2 or FTPS is recommended.
- This example applies to all versions of all S series switches.

The following uses the command lines and outputs of the S5720-EI running V200R008C00 as an example.
Networking Requirements
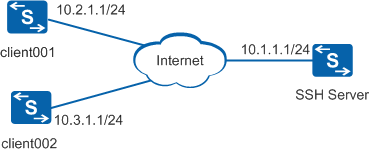
As shown in Figure 1, the routes between the SSH server and clients client001 and client002 are reachable. A Huawei switch is used as the SSH server in this example.
The clients client001 and client002 are required to connect to the SSH server in password and DSA authentication modes respectively to ensure secure access to files on the SSH server.
Configuration Roadmap
The configuration roadmap is as follows:
- Generate a local key pair on the SSH server and enable the SFTP server function to implement secure data exchange between the server and client.
- Configure the clients client001 and client002 on the SSH server to log in to the SSH server in password and DSA authentication modes, respectively.
- Generate a local key pair on client002 and configure the generated DSA public key on the SSH server, which implements authentication for the client when a user logs in to the server from the client.
- On the SSH server, enable client001 and client002 to log in to the SSH server using SFTP and access the files.
Procedure
- On the SSH server, generate a local key pair and enable
the SFTP server function.
<HUAWEI> system-view [HUAWEI] sysname SSH Server [SSH Server] dsa local-key-pair create //Generate a local DSA key pair. Info: The key name will be: SSH Server_Host_DSA. Info: The key modulus can be any one of the following : 1024, 2048. Info: If the key modulus is greater than 512, it may take a few minutes. Please input the modulus [default=2048]: //Press Enter. The default key length (2048 bits) is used. Info: Generating keys........ Info: Succeeded in creating the DSA host keys. [SSH Server] sftp server enable //Enable the SFTP server function. Info: Succeeded in starting the SFTP server.
- Create SSH users on the SSH server.
# Configure VTY user interfaces on the SSH server.
[SSH Server] user-interface vty 0 4 //Enter the user interface views of VTY 0 to VTY 4. [SSH Server-ui-vty0-4] authentication-mode aaa //Set the authentication mode of users in VTY 0 to VTY 4 to AAA. [SSH Server-ui-vty0-4] protocol inbound ssh //Configure the user interface views of VTY 0 to VTY 4 to support SSH. [SSH Server-ui-vty0-4] user privilege level 3 //Set the user level to 3. [SSH Server-ui-vty0-4] quit
# Create an SSH user named client001 and configure the password authentication mode for the user.
[SSH Server] ssh user client001 //Create an SSH user. [SSH Server] ssh user client001 authentication-type password //Set the authentication mode to password authentication. [SSH Server] ssh user client001 service-type sftp //Set the user service type to SFTP. [SSH Server] ssh user client001 sftp-directory flash: //Set the SFTP service authorized directory to flash:. [SSH Server] aaa [SSH Server-aaa] local-user client001 password irreversible-cipher Helloworld@6789 //Set the login password to Helloworld@6789. [SSH Server-aaa] local-user client001 service-type ssh //Set the user service type to SSH. [SSH Server-aaa] local-user client001 privilege level 3 //Set the user level to 3. [SSH Server-aaa] quit
# Create an SSH user named client002 and configure the DSA authentication mode for the user.
[SSH Server] ssh user client002 //Create an SSH user. [SSH Server] ssh user client002 authentication-type dsa //Set the authentication mode to DSA authentication. [SSH Server] ssh user client002 service-type sftp //Set the user service type to SFTP. [SSH Server] ssh user client002 sftp-directory flash: //Set the SFTP service authorized directory to flash:.
- Generate a local key pair on client002 and configure
the generated DSA public key on the SSH server.
# Generate a local key pair on client002.
<HUAWEI> system-view [HUAWEI] sysname client002 [client002] dsa local-key-pair create //Generate a local DSA key pair. Info: The key name will be: SSH Server_Host_DSA. Info: The key modulus can be any one of the following : 1024, 2048. Info: If the key modulus is greater than 512, it may take a few minutes. Please input the modulus [default=2048]: //Press Enter. The default key length (2048 bits) is used. Info: Generating keys........ Info: Succeeded in creating the DSA host keys.
# Check the DSA public key generated on client002.
[client002] display dsa local-key-pair public ===================================================== Time of Key pair created:2014-08-27 06:35:16+08:00 Key name : client002_Host_DSA Key modulus : 2048 Key type : DSA encryption Key Key fingerprint: b7:68:86:90:d8:19:f3:e6:4a:f2:e9:fd:e4:24:ef:a5 ===================================================== Key code: 30820322 02820100 DEDEBA5C 8244DCB8 E696917C EFEBC0B3 E6FB60BE 8B9E36D3 E4EB9CD6 EB7FD210 219AC0F4 1AD47BF1 EACD435D 39AFA8FA CB6A7819 305EE147 E428912E 60452B37 CA17D611 C2EE4C46 B4BC7726 54C26856 A99ECFA5 D800367B 31A90522 F139496F 4182DBFD AAB59973 9AB02185 856A881F 9197368B 92DBF684 9D1C746B A27E12F9 8A28E4B6 D0587D65 5979A750 5413E91E FC961C3F 79209625 CFA8D7D4 69FA35A3 9E37B614 047D535D CD63AF30 58B3A25B 79C714B6 326B7DB6 067EBF15 3CC1A720 B0E1A7E3 9C13FEB3 BA26E6B0 52DC5BFF EE7C5C52 148FE6C2 40738FBB 8F05D416 B2B5DD72 E3629BB5 9244BF9F A29C4FCD 4EA0EE50 1FC6695D 03D68D51 9324E493 0214 C6C484E1 F0076B8A FCAD302B 98B50A3A 542ABEBB 02820100 3AC11746 EE959CBD 30F669C5 7E290BC4 7CB5BBFD 96AE9215 7A29C723 72FE8A02 EBED3B76 BE810B42 21AD8D32 F7723F83 59F46B66 FF7805CC 3F86D5D6 5BD424BD 70677EFF 1ACF9B3C CE02CD40 46560DA4 2036205C 6EFAB148 66E6A106 0DF6258B EE31CFE7 4B6C59B4 6FE59A9F BE64F982 EC36A669 FF597FB7 9A56E32E C15A0659 3D17C407 29F587C7 74959017 62B08070 24564B2E E79C6E1D 86793548 76CC662A 1D3DE1D1 2C79E102 C0B10E5C 9C4428B3 AEB93278 26D4CDE5 189A93EA 531E0FF8 2199EF35 DF038976 4538434F F39924F0 5BF17AC8 8E340991 B5EA0A62 A915EE63 F660C092 360C5D2D 796AF230 DB7461F7 C15B6DBA 65C9EFAB 247DB13D 4942E2FF 02820100 D7C6399A 86F7B38C 85168EF8 692BD9B4 01AA7BCD 98559075 98039259 0C54818C 650A95C7 0A5250EB 12124E5B C4123350 C190CC8B 4FFFD418 7E8F113F 6C36AB4B A56D2D1D 2C874C75 8400DAFE 4BABF957 4EDC8E7C DF5934DB 3AD717E5 50B1096B C0B46DE5 3FB508FA CB76FF1C 42CF7082 7DDEEB47 5C5C4F64 B1C8815C 496AC1E0 04C10EDD FE849B76 6DA15B48 0C9CF0B1 10BDDC08 41A65C28 8E21ADC6 48A93DF6 14552C1F 76A401AE E06E482D 6582052E 5B11A678 A467B38A B77C1C55 D367E253 FFA44841 FC38A462 B9AC24E6 DAD01628 F09ED629 58F666C1 1DEF7BD0 634C3D13 D75F2614 8CB49AFC 498A5195 F443CA4D C02FF228 A90D7593 AE46C5D0 4B224FEE Host public key for PEM format code: ---- BEGIN SSH2 PUBLIC KEY ---- AAAAB3NzaC1kc3MAAAEBAN7eulyCRNy45paRfO/rwLPm+2C+i5420+TrnNbrf9IQ IZrA9BrUe/HqzUNdOa+o+stqeBkwXuFH5CiRLmBFKzfKF9YRwu5MRrS8dyZUwmhW qZ7PpdgANnsxqQUi8TlJb0GC2/2qtZlzmrAhhYVqiB+RlzaLktv2hJ0cdGuifhL5 iijkttBYfWVZeadQVBPpHvyWHD95IJYlz6jX1Gn6NaOeN7YUBH1TXc1jrzBYs6Jb eccUtjJrfbYGfr8VPMGnILDhp+OcE/6zuibmsFLcW//ufFxSFI/mwkBzj7uPBdQW srXdcuNim7WSRL+fopxPzU6g7lAfxmldA9aNUZMk5JMAAAAVAMbEhOHwB2uK/K0w K5i1CjpUKr67AAABADrBF0bulZy9MPZpxX4pC8R8tbv9lq6SFXopxyNy/ooC6+07 dr6BC0IhrY0y93I/g1n0a2b/eAXMP4bV1lvUJL1wZ37/Gs+bPM4CzUBGVg2kIDYg XG76sUhm5qEGDfYli+4xz+dLbFm0b+Wan75k+YLsNqZp/1l/t5pW4y7BWgZZPRfE Byn1h8d0lZAXYrCAcCRWSy7nnG4dhnk1SHbMZiodPeHRLHnhAsCxDlycRCizrrky eCbUzeUYmpPqUx4P+CGZ7zXfA4l2RThDT/OZJPBb8XrIjjQJkbXqCmKpFe5j9mDA kjYMXS15avIw23Rh98Fbbbplye+rJH2xPUlC4v8AAAEAVkz2m0fokxPL5DekN8U4 2SkvxBhh7W+pMLesuDOBY9PIqfwcZqY23Oi7/eJGojmX0wYTOWi8t09Qn/LmeFNt AEaxHc4nLmvjxDuyjoTSA/AAYJDYJ6HWZoScy3mzDCUtEMGuaL/6SRUuH5wf9hMf LZzmb6ETrf8S5RZWVyZv3TKm3/FEAH7PNQYe8BYYG3SCfvgtqYQzRTZrDL6wLbCo otdHydlhfz9CtIYH3gfhnjXoq/X6HLQAFTexhBuoJ7nCtjC9c1HhJFicadQK2iY/ AOOu8jCp0l6vOUH4cniOONh6Mts9UiJNYnvZsjVJFzdkRsNpvcMBhK4/NneGPPMN +A== ---- END SSH2 PUBLIC KEY ---- Public key code for pasting into OpenSSH authorized_keys file : ssh-dss AAAAB3NzaC1kc3MAAAEBAN7eulyCRNy45paRfO/rwLPm+2C+i5420+TrnNbrf9IQIZrA9BrUe/HqzUNdOa+o+stqeBkwXuFH5CiRLmBFKzfKF9YRwu5MRrS8dyZU wmhWqZ7PpdgANnsxqQUi8TlJb0GC2/2qtZlzmrAhhYVqiB+RlzaLktv2hJ0cdGuifhL5iijkttBYfWVZeadQVBPpHvyWHD95IJYlz6jX1Gn6NaOeN7YUBH1TXc1jrzBYs6Jb eccUtjJrfbYGfr8VPMGnILDhp+OcE/6zuibmsFLcW//ufFxSFI/mwkBzj7uPBdQWsrXdcuNim7WSRL+fopxPzU6g7lAfxmldA9aNUZMk5JMAAAAVAMbEhOHwB2uK/K0wK5i1 CjpUKr67AAABADrBF0bulZy9MPZpxX4pC8R8tbv9lq6SFXopxyNy/ooC6+07dr6BC0IhrY0y93I/g1n0a2b/eAXMP4bV1lvUJL1wZ37/Gs+bPM4CzUBGVg2kIDYgXG76sUhm 5qEGDfYli+4xz+dLbFm0b+Wan75k+YLsNqZp/1l/t5pW4y7BWgZZPRfEByn1h8d0lZAXYrCAcCRWSy7nnG4dhnk1SHbMZiodPeHRLHnhAsCxDlycRCizrrkyeCbUzeUYmpPq Ux4P+CGZ7zXfA4l2RThDT/OZJPBb8XrIjjQJkbXqCmKpFe5j9mDAkjYMXS15avIw23Rh98Fbbbplye+rJH2xPUlC4v8AAAEAVkz2m0fokxPL5DekN8U42SkvxBhh7W+pMLes uDOBY9PIqfwcZqY23Oi7/eJGojmX0wYTOWi8t09Qn/LmeFNtAEaxHc4nLmvjxDuyjoTSA/AAYJDYJ6HWZoScy3mzDCUtEMGuaL/6SRUuH5wf9hMfLZzmb6ETrf8S5RZWVyZv 3TKm3/FEAH7PNQYe8BYYG3SCfvgtqYQzRTZrDL6wLbCootdHydlhfz9CtIYH3gfhnjXoq/X6HLQAFTexhBuoJ7nCtjC9c1HhJFicadQK2iY/AOOu8jCp0l6vOUH4cniOONh6 Mts9UiJNYnvZsjVJFzdkRsNpvcMBhK4/NneGPPMN+A== dsa-key# Configure the generated DSA public key on the SSH server. The bold part in the display command output indicates the generated DSA public key. Copy the key to the SSH server.[SSH Server] dsa peer-public-key dsakey001 encoding-type der [SSH Server-dsa-public-key] public-key-code begin [SSH Server-dsa-key-code]30820322 [SSH Server-dsa-key-code]02820100 [SSH Server-dsa-key-code]DEDEBA5C 8244DCB8 E696917C EFEBC0B3 E6FB60BE [SSH Server-dsa-key-code]8B9E36D3 E4EB9CD6 EB7FD210 219AC0F4 1AD47BF1 [SSH Server-dsa-key-code]EACD435D 39AFA8FA CB6A7819 305EE147 E428912E [SSH Server-dsa-key-code]60452B37 CA17D611 C2EE4C46 B4BC7726 54C26856 [SSH Server-dsa-key-code]A99ECFA5 D800367B 31A90522 F139496F 4182DBFD [SSH Server-dsa-key-code]AAB59973 9AB02185 856A881F 9197368B 92DBF684 [SSH Server-dsa-key-code]9D1C746B A27E12F9 8A28E4B6 D0587D65 5979A750 [SSH Server-dsa-key-code]5413E91E FC961C3F 79209625 CFA8D7D4 69FA35A3 [SSH Server-dsa-key-code]9E37B614 047D535D CD63AF30 58B3A25B 79C714B6 [SSH Server-dsa-key-code]326B7DB6 067EBF15 3CC1A720 B0E1A7E3 9C13FEB3 [SSH Server-dsa-key-code]BA26E6B0 52DC5BFF EE7C5C52 148FE6C2 40738FBB [SSH Server-dsa-key-code]8F05D416 B2B5DD72 E3629BB5 9244BF9F A29C4FCD [SSH Server-dsa-key-code]4EA0EE50 1FC6695D 03D68D51 9324E493 [SSH Server-dsa-key-code]0214 [SSH Server-dsa-key-code]C6C484E1 F0076B8A FCAD302B 98B50A3A 542ABEBB [SSH Server-dsa-key-code]02820100 [SSH Server-dsa-key-code]3AC11746 EE959CBD 30F669C5 7E290BC4 7CB5BBFD [SSH Server-dsa-key-code]96AE9215 7A29C723 72FE8A02 EBED3B76 BE810B42 [SSH Server-dsa-key-code]21AD8D32 F7723F83 59F46B66 FF7805CC 3F86D5D6 [SSH Server-dsa-key-code]5BD424BD 70677EFF 1ACF9B3C CE02CD40 46560DA4 [SSH Server-dsa-key-code]2036205C 6EFAB148 66E6A106 0DF6258B EE31CFE7 [SSH Server-dsa-key-code]4B6C59B4 6FE59A9F BE64F982 EC36A669 FF597FB7 [SSH Server-dsa-key-code]9A56E32E C15A0659 3D17C407 29F587C7 74959017 [SSH Server-dsa-key-code]62B08070 24564B2E E79C6E1D 86793548 76CC662A [SSH Server-dsa-key-code]1D3DE1D1 2C79E102 C0B10E5C 9C4428B3 AEB93278 [SSH Server-dsa-key-code]26D4CDE5 189A93EA 531E0FF8 2199EF35 DF038976 [SSH Server-dsa-key-code]4538434F F39924F0 5BF17AC8 8E340991 B5EA0A62 [SSH Server-dsa-key-code]A915EE63 F660C092 360C5D2D 796AF230 DB7461F7 [SSH Server-dsa-key-code]C15B6DBA 65C9EFAB 247DB13D 4942E2FF [SSH Server-dsa-key-code]02820100 [SSH Server-dsa-key-code]D7C6399A 86F7B38C 85168EF8 692BD9B4 01AA7BCD [SSH Server-dsa-key-code]98559075 98039259 0C54818C 650A95C7 0A5250EB [SSH Server-dsa-key-code]12124E5B C4123350 C190CC8B 4FFFD418 7E8F113F [SSH Server-dsa-key-code]6C36AB4B A56D2D1D 2C874C75 8400DAFE 4BABF957 [SSH Server-dsa-key-code]4EDC8E7C DF5934DB 3AD717E5 50B1096B C0B46DE5 [SSH Server-dsa-key-code]3FB508FA CB76FF1C 42CF7082 7DDEEB47 5C5C4F64 [SSH Server-dsa-key-code]B1C8815C 496AC1E0 04C10EDD FE849B76 6DA15B48 [SSH Server-dsa-key-code]0C9CF0B1 10BDDC08 41A65C28 8E21ADC6 48A93DF6 [SSH Server-dsa-key-code]14552C1F 76A401AE E06E482D 6582052E 5B11A678 [SSH Server-dsa-key-code]A467B38A B77C1C55 D367E253 FFA44841 FC38A462 [SSH Server-dsa-key-code]B9AC24E6 DAD01628 F09ED629 58F666C1 1DEF7BD0 [SSH Server-dsa-key-code]634C3D13 D75F2614 8CB49AFC 498A5195 F443CA4D [SSH Server-dsa-key-code]C02FF228 A90D7593 AE46C5D0 4B224FEE [SSH Server-dsa-key-code] public-key-code end [SSH Server-dsa-public-key] peer-public-key end
# On the SSH server, bind the DSA public key to client002.
[SSH Server] ssh user client002 assign dsa-key dsakey001
- Connect SFTP clients to the SSH server.
# Enable the first authentication function on the SSH clients upon the first login.
<HUAWEI> system-view [HUAWEI] sysname client001 [client001] ssh client first-time enable //Enable the first authentication function on client001.
[client002] ssh client first-time enable //Enable the first authentication function on client002.# Log in to the SSH server from client001 in password authentication mode.
[client001] sftp 10.1.1.1 Please input the username:client001 Trying 10.1.1.1 ... Press CTRL+K to abort Connected to 10.1.1.1 ... password:SSH_SERVER_CODE Please select public key type for user authentication [R for RSA; D for DSA; Enter for Skip publickey authentication; Ctrl_C for Cancel], Please select [R, D, Enter or Ctrl_C]:D Enter password: sftp-client>
# Log in to the SSH server from client002 in DSA authentication mode.
[client002] sftp 10.1.1.1 Please input the username:client002 Trying 10.1.1.1 ... Press CTRL+K to abort Connected to 10.1.1.1 ... password:SSH_SERVER_CODE Please select public key type for user authentication [R for RSA; D for DSA; Enter for Skip publickey authentication; Ctrl_C for Cancel], Please select [R, D, Enter or Ctrl_C]:D sftp-client>
- Verify the configuration.
Run the display ssh server status command on the SSH server to check whether the SFTP service is enabled. Run the display ssh user-information command to check information about SSH users on the server.
# Check the status of the SSH server.
[SSH Server] display ssh server status SSH version :1.99 SSH connection timeout :60 seconds SSH server key generating interval :0 hours SSH authentication retries :3 times SFTP server :Enable Stelnet server :Disable Scp server :Disable SSH server source :0.0.0.0 ACL4 number :0 ACL6 number :0# Check information about SSH users.
[SSH Server] display ssh user-information User 1: User Name : client001 Authentication-type : password User-public-key-name : - User-public-key-type : - Sftp-directory : flash: Service-type : sftp Authorization-cmd : No User 2: User Name : client002 Authentication-type : dsa User-public-key-name : dsakey001 User-public-key-type : dsa Sftp-directory : flash: Service-type : sftp Authorization-cmd : No
Configuration Files
SSH server configuration file
# sysname SSH Server # dsa peer-public-key dsakey001 encoding-type der public-key-code begin 30820322 02820100 DEDEBA5C 8244DCB8 E696917C EFEBC0B3 E6FB60BE 8B9E36D3 E4EB9CD6 EB7FD210 219AC0F4 1AD47BF1 EACD435D 39AFA8FA CB6A7819 305EE147 E428912E 60452B37 CA17D611 C2EE4C46 B4BC7726 54C26856 A99ECFA5 D800367B 31A90522 F139496F 4182DBFD AAB59973 9AB02185 856A881F 9197368B 92DBF684 9D1C746B A27E12F9 8A28E4B6 D0587D65 5979A750 5413E91E FC961C3F 79209625 CFA8D7D4 69FA35A3 9E37B614 047D535D CD63AF30 58B3A25B 79C714B6 326B7DB6 067EBF15 3CC1A720 B0E1A7E3 9C13FEB3 BA26E6B0 52DC5BFF EE7C5C52 148FE6C2 40738FBB 8F05D416 B2B5DD72 E3629BB5 9244BF9F A29C4FCD 4EA0EE50 1FC6695D 03D68D51 9324E493 0214 C6C484E1 F0076B8A FCAD302B 98B50A3A 542ABEBB 02820100 3AC11746 EE959CBD 30F669C5 7E290BC4 7CB5BBFD 96AE9215 7A29C723 72FE8A02 EBED3B76 BE810B42 21AD8D32 F7723F83 59F46B66 FF7805CC 3F86D5D6 5BD424BD 70677EFF 1ACF9B3C CE02CD40 46560DA4 2036205C 6EFAB148 66E6A106 0DF6258B EE31CFE7 4B6C59B4 6FE59A9F BE64F982 EC36A669 FF597FB7 9A56E32E C15A0659 3D17C407 29F587C7 74959017 62B08070 24564B2E E79C6E1D 86793548 76CC662A 1D3DE1D1 2C79E102 C0B10E5C 9C4428B3 AEB93278 26D4CDE5 189A93EA 531E0FF8 2199EF35 DF038976 4538434F F39924F0 5BF17AC8 8E340991 B5EA0A62 A915EE63 F660C092 360C5D2D 796AF230 DB7461F7 C15B6DBA 65C9EFAB 247DB13D 4942E2FF 02820100 D7C6399A 86F7B38C 85168EF8 692BD9B4 01AA7BCD 98559075 98039259 0C54818C 650A95C7 0A5250EB 12124E5B C4123350 C190CC8B 4FFFD418 7E8F113F 6C36AB4B A56D2D1D 2C874C75 8400DAFE 4BABF957 4EDC8E7C DF5934DB 3AD717E5 50B1096B C0B46DE5 3FB508FA CB76FF1C 42CF7082 7DDEEB47 5C5C4F64 B1C8815C 496AC1E0 04C10EDD FE849B76 6DA15B48 0C9CF0B1 10BDDC08 41A65C28 8E21ADC6 48A93DF6 14552C1F 76A401AE E06E482D 6582052E 5B11A678 A467B38A B77C1C55 D367E253 FFA44841 FC38A462 B9AC24E6 DAD01628 F09ED629 58F666C1 1DEF7BD0 634C3D13 D75F2614 8CB49AFC 498A5195 F443CA4D C02FF228 A90D7593 AE46C5D0 4B224FEE public-key-code end peer-public-key end # aaa local-user client001 password irreversible-cipher %^%#-=9Z)M,-aL$_U%#$W^1T-\}Fqpe$E<#H$J<6@KTSL/J'\}I-%^%# local-user client001 privilege level 3 local-user client001 service-type ssh # sftp server enable ssh user client001 ssh user client001 authentication-type password ssh user client001 service-type sftp ssh user client001 sftp-directory flash: ssh user client002 ssh user client002 authentication-type dsa ssh user client002 assign dsa-key dsakey001 ssh user client002 service-type sftp ssh user client002 sftp-directory flash: # user-interface vty 0 4 authentication-mode aaa user privilege level 3 # returnclient001 configuration file
# sysname client001 # ssh client first-time enable # return
client002 configuration file
# sysname client002 # ssh client first-time enable # return