Example for Configuring IPSG to Prevent Hosts with Static IP Addresses from Changing Their Own IP Addresses
IPSG Overview
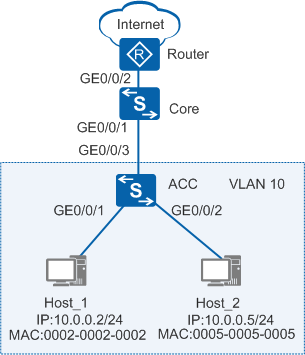
As shown in Figure 1, a hacker (Host_2) uses the IP and MAC addresses of Host_1, which belongs to an R&D engineer, to construct IP packets to attack the intranet. The network administrator thinks the R&D engineer is the attacker. Such attacks can be prevented by configuring IPSG. On the access switch, after a static binding table is configured and IP packet check is enabled on the interfaces connected to terminals, only the packets matching the static binding entries can access the intranet and the Internet, and the packets not matching the entries are discarded.
Configuration Notes
- S2700-SI of V100R006C05 does not support IPSG.
- After hardware-based Layer 3 forwarding for
IPv4 packets is enabled in the following versions, the switches do
not support IPSG:
- V200R007C00, V200R008C00, V200R011 and later versions: S2750-EI, S5700-10P-LI-AC, and S5700-10P-PWR-LI-AC
- V200R009C00 and V200R010C00: S2720-EI, S2750-EI, S5700-10P-LI-AC, and S5700-10P-PWR-LI-AC
Networking Requirements
As shown in Figure 1, the user gateway is configured on the core switch (Core). An ACL is configured on the Core to allow fixed hosts to access the Internet. The hosts connected to the access switch (ACC) use statically configured IP addresses. The administrator requires that the hosts can only use fixed IP addresses to access the Internet. Users are not allowed to change their own IP addresses to access the Internet.
Data Plan
To perform the configuration, you need to the following data.
Item |
Data |
Description |
|---|---|---|
VLAN |
|
None |
Gateway IP address of hosts |
VLANIF10: 10.0.0.1/24 |
None |
IP addresses of the hosts allowed to access the network. |
10.0.0.2, 10.0.0.3 |
None |
Configuration Roadmap
The configuration roadmap is as follows:
- Configure an ACL on the user gateway (Core) to allow the hosts with IP addresses 10.0.0.2 and 10.0.0.3 to access the Internet.
- Create static binding entries for the hosts on the ACC to fix the mappings between IP addresses and MAC addresses.
- Enable IPSG on the ACC's interfaces connected to user hosts so that the hosts can only use the fixed IP addresses to access the network. Host_1 can access the Internet, and Host_2 cannot access the Internet, even if it changes its IP address.
Procedure
- Configure an ACL.
<HUAWEI> system-view [HUAWEI] sysname Core [Core] vlan batch 10 [Core] interface gigabitethernet 0/0/1 [Core-GigabitEthernet0/0/1] port link-type trunk [Core-GigabitEthernet0/0/1] port trunk allow-pass vlan 10 [Core-GigabitEthernet0/0/1] quit [Core] interface vlanif 10 //Configure the gateway address. [Core-Vlanif10] ip address 10.0.0.1 255.255.255.0 [Core-Vlanif10] quit [Core] acl number 3001 //Configure an ACL. [Core-acl-adv-3001] rule permit ip source 10.0.0.2 0 [Core-acl-adv-3001] rule permit ip source 10.0.0.3 0 [Core-acl-adv-3001] rule deny ip source 10.0.0.0 0.0.0.255 [Core-acl-adv-3001] quit [Core] traffic classifier c1 //Configure an ACL-based traffic classifier. [Core-classifier-c1] if-match acl 3001 [Core-classifier-c1] quit [Core] traffic behavior b1 //Configure a traffic behavior. [Core-behavior-b1] permit [Core-behavior-b1] quit [Core] traffic policy p1 //Configure a traffic policy. [Core-trafficpolicy-p1] classifier c1 behavior b1 [Core-trafficpolicy-p1] quit [Core] interface gigabitethernet 0/0/2 [Core-GigabitEthernet0/0/2] traffic-policy p1 outbound //Apply the traffic policy. [Core-GigabitEthernet0/0/2] quit
- Create static binding entries for the hosts.
<HUAWEI> system-view [HUAWEI] sysname ACC [ACC] vlan batch 10 //Configure a VLAN to connect to hosts. [ACC] interface gigabitethernet 0/0/1 [ACC-GigabitEthernet0/0/1] port link-type access [ACC-GigabitEthernet0/0/1] port default vlan 10 [ACC-GigabitEthernet0/0/1] quit [ACC] interface gigabitethernet 0/0/2 [ACC-GigabitEthernet0/0/2] port link-type access [ACC-GigabitEthernet0/0/2] port default vlan 10 [ACC-GigabitEthernet0/0/2] quit [ACC] interface gigabitethernet 0/0/3 [ACC-GigabitEthernet0/0/3] port link-type trunk [ACC-GigabitEthernet0/0/3] port trunk allow-pass vlan 10 [ACC-GigabitEthernet0/0/3] quit [ACC] user-bind static ip-address 10.0.0.2 mac-address 0002-0002-0002 interface gigabitethernet 0/0/1 //Create a static binding entry for Host_1. [ACC] user-bind static ip-address 10.0.0.5 mac-address 0005-0005-0005 interface gigabitethernet 0/0/2 //Create a static binding entry for Host_2.
- Enable IPSG.
# Enable IPSG on GE0/0/1 connected to Host_1.
[ACC] interface gigabitethernet 0/0/1 [ACC-GigabitEthernet0/0/1] ip source check user-bind enable [ACC-GigabitEthernet0/0/1] quit
# Enable IPSG on GE0/0/2 connected to Host_2.
[ACC] interface gigabitethernet 0/0/2 [ACC-GigabitEthernet0/0/2] ip source check user-bind enable [ACC-GigabitEthernet0/0/2] quit
- Verify the configuration.
Run the display dhcp static user-bind all command on the ACC to view static binding entries.
[ACC] display dhcp static user-bind all DHCP static Bind-table: Flags:O - outer vlan ,I - inner vlan ,P - Vlan-mapping IP Address MAC Address VSI/VLAN(O/I/P) Interface -------------------------------------------------------------------------------- 10.0.0.2 0002-0002-0002 -- /-- /-- GE0/0/1 10.0.0.5 0005-0005-0005 -- /-- /-- GE0/0/2 -------------------------------------------------------------------------------- Print count: 2 Total count: 2
Run the display dhcp static user-bind all verbose command on the ACC to view IPSG status. If the status is effective, the static entry has taken effect.
[ACC] display dhcp static user-bind all verbose DHCP static Bind-table: Flags:O - outer vlan ,I - inner vlan ,P - Vlan-mapping -------------------------------------------------------------------------------- IP Address : 10.0.0.2 MAC Address : 0002-0002-0002 VSI : -- VLAN(O/I/P) : -- /-- /-- Interface : GE0/0/1 IPSG Status : effective slot: <0> -------------------------------------------------------------------------------- IP Address : 10.0.0.5 MAC Address : 0005-0005-0005 VSI : -- VLAN(O/I/P) : -- /-- /-- Interface : GE0/0/2 IPSG Status : effective slot: <0> -------------------------------------------------------------------------------- Print count: 2 Total count: 2
Host_1 can access the Internet, and Host_2 cannot access the Internet. After the IP address of Host_2 is changed to 10.0.0.3, Host_2 cannot access the Internet and the intranet.
Configuration Files
Configuration file of the Core
# sysname Core # vlan batch 10 # acl number 3001 rule 5 permit ip source 10.0.0.2 0 rule 10 permit ip source 10.0.0.3 0 rule 15 deny ip source 10.0.0.0 0.0.0.255 # traffic classifier c1 operator or precedence 5 if-match acl 3001 # traffic behavior b1 permit # traffic policy p1 match-order config classifier c1 behavior b1 # interface Vlanif10 ip address 10.0.0.1 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 10 # interface GigabitEthernet0/0/2 traffic-policy p1 outbound # return
Configuration file of the ACC
# sysname ACC # vlan batch 10 # user-bind static ip-address 10.0.0.2 mac-address 0002-0002-0002 interface GigabitEthernet0/0/1 user-bind static ip-address 10.0.0.5 mac-address 0005-0005-0005 interface GigabitEthernet0/0/2 # interface GigabitEthernet0/0/1 port link-type access port default vlan 10 ip source check user-bind enable # interface GigabitEthernet0/0/2 port link-type access port default vlan 10 ip source check user-bind enable # interface GigabitEthernet0/0/3 port link-type trunk port trunk allow-pass vlan 10 # return