Example for Configuring Traffic Policies to Implement Policy-based Routing (Redirection to Different Next Hops)
Policy-based Routing Overview
Traditionally, a device searches its routing table for routes based on destination addresses of received packets and then forwards the packets according to the routes. Currently, more users require packet routing based on user-defined policies. Policy-based routing (PBR) is a data forwarding mechanism implemented based on user-defined policies.
On S series switches, PBR is implemented by redirecting incoming Layer 3 packets that match traffic classification rules on an interface to a specified next-hop IP address.
When a specific data flow needs to be transmitted to a specified next hop, PBR can be configured to meet this requirement. For example, different data flows can be transmitted on different links to improve link efficiency. Data flows can be directed to security devices such as firewalls for security filtering. Service data can be transmitted on a low-cost link to reduce enterprises' data service costs without compromising service quality.
Configuration Notes
- If a device does not have the ARP entry that matches the specified next-hop IP address, the device triggers ARP learning. If the device cannot learn the ARP entry, packets are forwarded along the previous forwarding path without being redirected.
- If multiple next-hop IP addresses are configured using the redirect ip-nexthop or redirect ipv6-nexthop command, the device redirects packets in active/standby link mode. That is, the device determines active and standby links according to the sequence in which next-hop IP addresses were configured. The first configured next-hop IP address has the highest priority and its link functions as the active link, while links of other next-hop IP addresses function as standby links. When the active link is Down, the standby link of the second-highest-priority next-hop IP address is selected as the new active link.
- If multiple next-hop IP addresses are configured using the redirect ip-multihop or redirect ipv6-multihop command, the device redirects packets in equal-cost route load balancing mode.
- For the fixed switch models and versions that support this example, see Applicable Products and Versions.
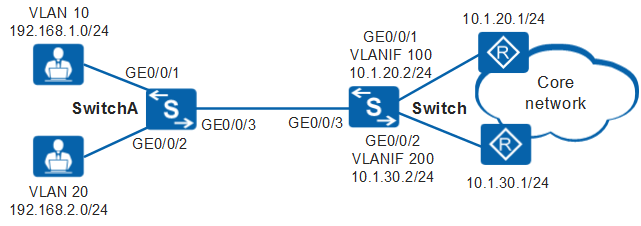
Networking Requirements
As shown in Figure 1, an enterprise network is dual-homed to two external network devices through the Switch. One uplink is a high-speed link with the gateway at 10.1.20.1/24, and the other is a low-speed link with the gateway at 10.1.30.1/24.
The enterprise intranet has two network segments: 192.168.1.0/24 and 192.168.2.0/24. Network segment 192.168.1.0/24 belongs to the server zone and requires high link bandwidth. Therefore, traffic of this network segment needs to be transmitted on the high-speed link. Network segment 192.168.2.0/24 is used for Internet access and traffic of this network segment is transmitted on the low-speed link.
Configuration Roadmap
- Create VLANs, configure interfaces, and configure routes to connect enterprise users to the external network.
- Configure ACLs to match data flows of network segments 192.168.1.0 and 192.168.2.0.
- Create traffic classifiers and reference the ACLs to differentiate packets.
- Configure traffic behaviors to transmit data traffic matching different ACLs on different links and allow traffic transmitted between the intranet users to pass through first.
- Configure a traffic policy, bind the traffic classifiers and traffic behaviors to it, and apply it to the inbound direction of GE0/0/3 on the Switch to implement PBR.
Procedure
- Create VLANs, configure interfaces, and configure routes for interworking.
# Create VLANs 10 and 20 on SwitchA.
<HUAWEI> system-view [HUAWEI] sysname SwitchA [SwitchA] vlan batch 10 20
# On Switch, set the link types of the interfaces connected to PCs to access and interface connected to the Switch to trunk, and add the interfaces to VLANs.
[SwitchA] interface gigabitethernet 0/0/1 [SwitchA-GigabitEthernet0/0/1] port link-type access [SwitchA-GigabitEthernet0/0/1] port default vlan 10 [SwitchA-GigabitEthernet0/0/1] quit [SwitchA] interface gigabitethernet 0/0/2 [SwitchA-GigabitEthernet0/0/2] port link-type access [SwitchA-GigabitEthernet0/0/2] port default vlan 20 [SwitchA-GigabitEthernet0/0/2] quit [SwitchA] interface gigabitethernet 0/0/3 [SwitchA-GigabitEthernet0/0/3] port link-type trunk [SwitchA-GigabitEthernet0/0/3] port trunk allow-pass vlan 10 20 [SwitchA-GigabitEthernet0/0/3] quit
# Create VLANs 10, 20, 100, and 200 on the Switch.
<HUAWEI> system-view [HUAWEI] sysname Switch [Switch] vlan batch 10 20 100 200
# On the Switch, set the link types of the interfaces connected to SwitchA to trunk and interface connected to the external network to access, and add the interfaces to VLANs.
[Switch] interface gigabitethernet 0/0/1 [Switch-GigabitEthernet0/0/1] port link-type access [Switch-GigabitEthernet0/0/1] port default vlan 100 [Switch-GigabitEthernet0/0/1] quit [Switch] interface gigabitethernet 0/0/2 [Switch-GigabitEthernet0/0/2] port link-type access [Switch-GigabitEthernet0/0/2] port default vlan 200 [Switch-GigabitEthernet0/0/2] quit [Switch] interface gigabitethernet 0/0/3 [Switch-GigabitEthernet0/0/3] port link-type trunk [Switch-GigabitEthernet0/0/3] port trunk allow-pass vlan 10 20 [Switch-GigabitEthernet0/0/3] quit
# On the Switch, configure VLANIF10 and VLANIF20 as user gateways and assign IP addresses 192.168.1.1/24 and 192.168.2.1/24 to them.
[Switch] interface vlanif 10 [Switch-Vlanif10] ip address 192.168.1.1 24 [Switch-Vlanif10] quit [Switch] interface vlanif 20 [Switch-Vlanif20] ip address 192.168.2.1 24 [Switch-Vlanif20] quit
# On the Switch, configure VLANIF 100 and VLANIF 200 to connect to external network devices and assign IP addresses to 10.1.20.2/24 and 10.1.30.2/24 to them, respectively.
[Switch] interface vlanif 100 [Switch-Vlanif100] ip address 10.1.20.2 24 [Switch-Vlanif100] quit [Switch] interface vlanif 200 [Switch-Vlanif200] ip address 10.1.30.2 24 [Switch-Vlanif200] quit
# On the Switch, configure two default routes and set their next-hop IP addresses to IP addresses of the two external network devices.
[Switch] ip route-static 0.0.0.0 0 10.1.20.1 [Switch] ip route-static 0.0.0.0 0 10.1.30.1
After the preceding configuration is complete, intranet users can access the external network. To ensure that data flows of network segments 192.168.1.0/24 and 192.168.2.0/24 are transmitted on the high-speed link and low-speed link respectively, perform the following configurations.
- Configure ACLs.
# On the Switch, create advanced ACLs 3000, 3001, and 3002.
[Switch] acl 3000 //This ACL is used to match data traffic between two network segments of the intranet. The data traffic does not need to be redirected. If this configuration is not performed, traffic between the network segments will be redirected. As a result, communication between the network segments will fail. [Switch-acl-adv-3000] rule permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255 [Switch-acl-adv-3000] rule permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255 Switch-acl-adv-3000] quit [Switch] acl 3001 //Match data traffic of the intranet network segment 192.168.1.0/24. [Switch-acl-adv-3001] rule permit ip source 192.168.1.0 0.0.0.255 [Switch-acl-adv-3001] quit [Switch] acl 3002 //Match data traffic of the intranet network segment 192.168.2.0/24. [Switch-acl-adv-3002] rule permit ip source 192.168.2.0 0.0.0.255 [Switch-acl-adv-3002] quit
- Configure traffic classifiers.
On the Switch, create traffic classifiers c0, c1, and c2, and bind c0 to ACL 3000, c1 to ACL 3001, and c2 to ACL 3002.
[Switch] traffic classifier c0 operator or [Switch-classifier-c0] if-match acl 3000 [Switch-classifier-c0] quit [Switch] traffic classifier c1 operator or [Switch-classifier-c1] if-match acl 3001 [Switch-classifier-c1] quit [Switch] traffic classifier c2 operator or [Switch-classifier-c2] if-match acl 3002 [Switch-classifier-c2] quit
- Configure traffic behaviors.
# On the Switch, create traffic behaviors b0, b1, and b2, configure the permit action in b0, and configure actions that redirect packets to IP addresses 10.1.20.1 and 10.1.30.1 in b1 and b2 respectively.
[Switch] traffic behavior b0 [Switch-behavior-b0] permit [Switch-behavior-b0] quit [Switch] traffic behavior b1 [Switch-behavior-b1] redirect ip-nexthop 10.1.20.1 [Switch-behavior-b1] quit [Switch] traffic behavior b2 [Switch-behavior-b2] redirect ip-nexthop 10.1.30.1 [Switch-behavior-b2] quit
- Configure a traffic policy and apply the traffic policy to an interface.
# On the Switch, create a traffic policy p1 and bind the traffic classifiers and traffic behaviors to this traffic policy.
[Switch] traffic policy p1 [Switch-trafficpolicy-p1] classifier c0 behavior b0 [Switch-trafficpolicy-p1] classifier c1 behavior b1 [Switch-trafficpolicy-p1] classifier c2 behavior b2 [Switch-trafficpolicy-p1] quit
# Apply the traffic policy p1 to the inbound direction of GE0/0/3 on the Switch.
[Switch] interface gigabitethernet 0/0/3 [Switch-GigabitEthernet0/0/3] traffic-policy p1 inbound [Switch-GigabitEthernet0/0/3] return
- Verify the configuration.
# Check the ACL configuration.
<Switch> display acl 3000 Advanced ACL 3000, 2 rules Acl's step is 5 rule 5 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255 rule 10 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255<Switch> display acl 3001 Advanced ACL 3001, 1 rule Acl's step is 5 rule 5 permit ip source 192.168.1.0 0.0.0.255<Switch> display acl 3002 Advanced ACL 3002, 1 rule Acl's step is 5 rule 5 permit ip source 192.168.2.0 0.0.0.255# Check the traffic classifier configuration.
<Switch> display traffic classifier user-defined User Defined Classifier Information: Classifier: c2 Operator: OR Rule(s) : if-match acl 3002 Classifier: c0 Operator: OR Rule(s) : if-match acl 3000 Classifier: c1 Operator: OR Rule(s) : if-match acl 3001 Total classifier number is 3# Check the traffic policy configuration.
<Switch> display traffic policy user-defined p1 User Defined Traffic Policy Information: Policy: p1 Classifier: c0 Operator: OR Behavior: b0 Permit Classifier: c1 Operator: OR Behavior: b1 Permit Redirect: no forced Redirect ip-nexthop 10.1.20.1 Classifier: c2 Operator: OR Behavior: b2 Permit Redirect: no forced Redirect ip-nexthop 10.1.30.1
Configuration Files
SwitchA configuration file
# sysname SwitchA # vlan batch 10 20 # interface GigabitEthernet0/0/1 port link-type access port default vlan 10 # interface GigabitEthernet0/0/2 port link-type access port default vlan 20 # interface GigabitEthernet0/0/3 port link-type trunk port trunk allow-pass vlan 10 20 # return
Switch configuration file
# sysname Switch # vlan batch 10 20 100 200 # acl number 3000 rule 5 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255 rule 10 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255 acl number 3001 rule 5 permit ip source 192.168.1.0 0.0.0.255 acl number 3002 rule 5 permit ip source 192.168.2.0 0.0.0.255 # traffic classifier c0 operator or if-match acl 3000 traffic classifier c1 operator or if-match acl 3001 traffic classifier c2 operator or if-match acl 3002 # traffic behavior b0 permit traffic behavior b1 redirect ip-nexthop 10.1.20.1 traffic behavior b2 redirect ip-nexthop 10.1.30.1 # traffic policy p1 match-order config classifier c0 behavior b0 classifier c1 behavior b1 classifier c2 behavior b2 # interface Vlanif10 ip address 192.168.1.1 255.255.255.0 # interface Vlanif20 ip address 192.168.2.1 255.255.255.0 # interface Vlanif100 ip address 10.1.20.2 255.255.255.0 # interface Vlanif200 ip address 10.1.30.2 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type access port default vlan 100 # interface GigabitEthernet0/0/2 port link-type access port default vlan 200 # interface GigabitEthernet0/0/3 port link-type trunk port trunk allow-pass vlan 10 20 traffic-policy p1 inbound # ip route-static 0.0.0.0 0.0.0.0 10.1.20.1 ip route-static 0.0.0.0 0.0.0.0 10.1.30.1 # return
Applicable Products and Versions
Product |
Product Model |
Software Version |
|---|---|---|
S2700 |
S2700-EI |
Supported only by S2752EI V100R005 and V100R006 |
S2720-EI |
V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S3700 |
S3700-SI, S3700-EI |
V100R006C05 |
S3700-HI |
V200R001C00 |
|
S5700 |
S5700-EI |
V200R001(C00&C01), V200R002C00, V200R003C00, V200R005(C00&C01&C02&C03) |
S5710-EI |
V200R001C00, V200R002C00, V200R003C00, V200R005(C00&C02) |
|
S5720-EI |
V200R007C00, V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5720-LI, S5720S-LI |
V200R010C00, V200R011C00, V200R011C10, V200R012(C00&C20), V200R013C00, V200R019C00, V200R019C10 |
|
S5720-SI, S5720S-SI |
V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5720I-SI |
V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5730-SI |
V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5730S-EI |
V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5700-HI |
V200R001(C00&C01), V200R002C00, V200R003C00, V200R005(C00SPC500&C01&C02) |
|
S5710-HI |
V200R003C00, V200R005(C00&C02&C03) |
|
S5720-HI |
V200R006C00, V200R007(C00&C10), V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5730-HI |
V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5731-H |
V200R013C02, V200R019C00, V200R019C10 |
|
S5731-S, S5731S-S |
V200R019C00, V200R019C10 |
|
S5731S-H |
V200R019C00, V200R019C10 |
|
S5732-H |
V200R019C00, V200R019C10 |
|
S5735-L, S5735S-L |
V200R019C00, V200R019C10 |
|
S5735S-L-M |
V200R019C00, V200R019C10 |
|
S5735-S, S5735S-S |
V200R019C00, V200R019C10 |
|
S5700 |
S5735-S-I |
V200R019C10 |
S6700 |
S6700-EI |
V200R001(C00&C01), V200R002C00, V200R003C00, V200R005(C00&C01&C02) |
S6720-EI |
V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6720S-EI |
V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6720-SI, S6720S-SI |
V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6720-LI, S6720S-LI |
V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6720-HI |
V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6730-H |
V200R013C02, V200R019C00, V200R019C10 |
|
S6730S-H |
V200R019C10 |
|
S6730-S, S6730S-S |
V200R019C00, V200R019C10 |
|
S7700 |
S7703, S7706, S7712 |
V200R001(C00&C01), V200R002C00, V200R003C00, V200R005C00, V200R006C00, V200R007C00, V200R008C00, V200R009C00, V200R010C00, V200R011C10, V200R012C00, V200R013C00, V200R013C02, V200R019C00, V200R019C10 |
S7703 PoE |
V200R013C00, V200R019C00, V200R019C10 |
|
S7706 PoE |
V200R013C00, V200R019C00, V200R019C10 |
|
S9700 |
S9703, S9706, S9712 |
V200R001(C00&C01), V200R002C00, V200R003C00, V200R005C00, V200R006C00, V200R007(C00&C10), V200R008C00, V200R009C00, V200R010C00, V200R011C10, V200R012C00, V200R013C00 |

For details about software mappings, visit Hardware Query Tool and search for the desired product model.