Example for Configuring Port Security
Port Security Overview
Port security changes the dynamic MAC addresses learned on an interface into secure MAC addresses (including dynamic and static secure MAC addresses, and sticky MAC addresses). This function prevents unauthorized users from communicating with the switch using this interface. Generally, port security is configured on access devices to bind users to interfaces and control access users on interfaces.
Compared with the static MAC address entry and user-bind used to bind users statically, port security dynamically binds users to interfaces.
Compared with DHCP snooping that also dynamically binds users to interface, port security is easier to configure. In addition, port security can limit the number of access users.
Configuration Notes
- After MAC address limiting is configured on an interface, port security cannot be configured on the interface.
- This example applies to all versions of all S series switches.
Networking Requirements
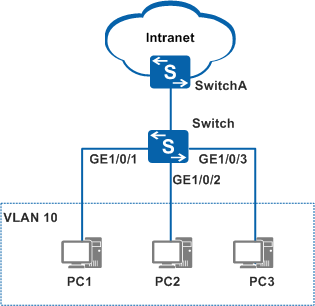
As shown in Figure 1, PC1, PC2, and PC3 connect to the company network through the switch. To improve user access security, port security is enabled on the interface of the switch so that external users cannot use their PCs to access the company network.
Configuration Roadmap
The configuration roadmap is as follows:
Create a VLAN to implement Layer 2 forwarding.
Configure port security and enable the sticky MAC function so that MAC address entries are not lost after the device configuration is saved and the device restarts.
Procedure
- Create a VLAN on the switch and add interfaces to the VLAN. The configurations of GE1/0/2 and GE1/0/3 are similar to the configuration of 1/0/1,
and are not mentioned here.
<HUAWEI> system-view [HUAWEI] sysname Switch [Switch] vlan 10 //Create VLAN 10. [Switch-vlan10] quit [Switch] interface gigabitethernet 1/0/1 [Switch-GigabitEthernet1/0/1] port link-type access //The link type of the interface connected to the PC must be access. The default link type of an interface is not access, so you need to manually configure the link type of the interface. [Switch-GigabitEthernet1/0/1] port default vlan 10 [Switch-GigabitEthernet1/0/1] quit
- Configure port security on GE1/0/1. The configurations of GE1/0/2 and GE1/0/3 are similar to the configuration of GE1/0/1, and are not mentioned here.
[Switch] interface gigabitethernet 1/0/1 [Switch-GigabitEthernet1/0/1] port-security enable //Enable port security. [Switch-GigabitEthernet1/0/1] port-security mac-address sticky //The sticky MAC function can be enabled only after port security is enabled. [Switch-GigabitEthernet1/0/1] port-security max-mac-num 1 //After port security is enabled, an interface can learn only one secure MAC address entry by default. If one user needs to be limited, ignore this configuration.

- An interface can learn only one secure MAC address entry by default. If multiple PCs connect to the company network using one interface, run the port-security max-mac-num command to change the maximum number of secure MAC addresses.
- If a PC connects to the switch using an IP phone, set the maximum number of secure MAC addresses to 3 because the IP phone occupies two MAC address entries and the PC occupies one MAC address entry. The VLAN IDs in two MAC address entries used by the IP phone are different. The two VLANs are used to transmit voice and data packets respectively.
- Verify the configuration.
If PC1, PC2, and PC3 are replaced by other PCs, the PCs cannot access the company network.
Configuration Files
Configuration file of the switch
# sysname Switch # vlan batch 10 # interface GigabitEthernet1/0/1 port link-type access port default vlan 10 port-security enable port-security mac-address sticky # interface GigabitEthernet1/0/2 port link-type access port default vlan 10 port-security enable port-security mac-address sticky # interface GigabitEthernet1/0/3 port link-type access port default vlan 10 port-security enable port-security mac-address sticky # return