Defense Against Cross-Network Bogus Parent Attacks
Attack Behavior
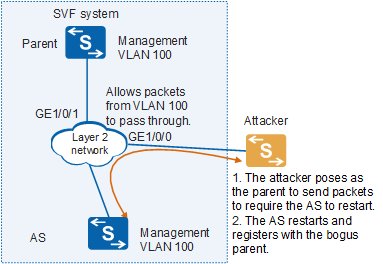
As shown in Figure 1, the management VLAN of the Super Virtual Fabric (SVF) system is VLAN 100, and the AS is connected to the parent through a third-party network which allows packets from VLAN 100 to pass through. An attacker poses as the parent to send packets in VLAN 100 to require the AS to restart. After the AS restarts, it registers with the bogus parent.
To prevent such an attack, use either of the following methods:
- Avoid adding the ports to which attackers may connect to VLAN 100.
- Configure DHCP snooping on the ports to which attackers may connect. You can also configure ACLs to discard Control and Provisioning of Wireless Access Points (CAPWAP) packets.
Security Policy
When an AS connects to the parent across a third-party network, control and data packets between the AS and parent pass through this network, and the control packets are non-encrypted data packets on this network.
To improve SVF system security and prevent a bogus parent from controlling the AS, configure the management VLAN of the SVF system as a transparent transmission VLAN on the third-party network. This prevents the packets sent by attackers from being transmitted in the same broadcast domain as SVF management packets. Alternatively, configure DHCP snooping on the third-party network's ports that attackers may connect to. This is to prevent attackers from posing as the parent to control the AS.
Configuration Method
Configure DHCP snooping on the third-party network. Assume that attackers may connect to GE1/0/0 and the network-side port on the third-party network is GE1/0/1.
<HUAWEI> system-view [HUAWEI] dhcp enable [HUAWEI] dhcp snooping enable [HUAWEI] interface gigabitethernet 1/0/0 [HUAWEI-Gigabitethernet1/0/0] dhcp snooping enable [HUAWEI-GigabitEthernet1/0/0] quit [HUAWEI] interface gigabitethernet 1/0/1 [HUAWEI-GigabitEthernet1/0/1] dhcp snooping trusted