Security Isolation and Defense Mechanisms
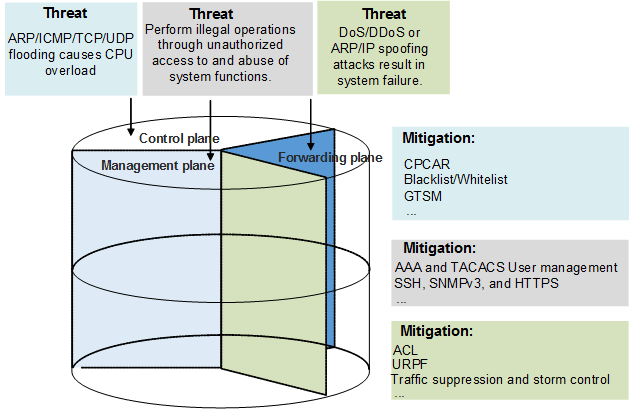
Switches comply with the three-layer three-plane security isolation mechanism of X.805. Figure 1 shows the security isolation architecture.
Management plane: This plane focuses on the security of application and service data for management users; that is, security of operation, maintenance, and management information.
Control plane: Switches have to run various protocols to implement services. The services must be protected against attacks or spoofing.
Forwarding plane: Switches use the destination MAC addresses and destination IP addresses of packets to search for routes for forwarding the packets. Security measures must be taken in the forwarding paths to prevent attacks on switches and spreading of attack traffic over the IP network.
By isolating the control, management, and forwarding planes, switches can ensure that attacks on any of the planes do not affect other planes.