Example for Configuring 802.1X Access
This section provides an example for configuring 802.1X access services. A networking diagram is provided to help you understand the configuration procedure. The example provides the networking requirements, configuration roadmap, configuration procedure, and configuration files.
Networking Requirements
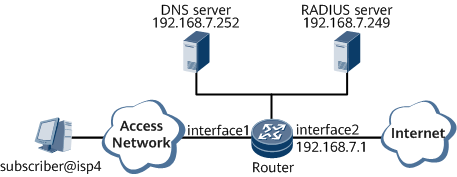
To prevent unauthorized users or devices from gaining access to a network and ensure network security, you can configure 802.1X access services to allow only authorized users to access the network. As shown in Figure 1,
Subscriber belongs to the domain isp4 and accesses the Internet through GE 0/1/2.1 on the router in 802.1X authentication mode.
RADIUS authentication and RADIUS accounting are used.

In the 802.1X system, the NetEngine 8000 F functions as a relay device, which must use the RADIUS server to transmit EAP packets.
The IP address of the RADIUS server is 192.168.7.249. The authentication port is numbered 1645 and the accounting port is numbered 1646. The RADIUS+1.1 protocol is adopted, with the key being itellin.
The IP address of the DNS server is 192.168.7.252.
The network-side interface on the NetEngine 8000 F is GE 0/1/9.
Configuration Roadmap
The configuration roadmap is as follows:
Configure a dot1x template.
Configure an authentication scheme.
Configures an accounting scheme.
Configure a RADIUS server group.
Configure an address pool.
Configure a domain named isp4.
Configure a BAS interface.
Data Preparation
To complete the configuration, you need the following data:
dot1x template name
Timeout period for the BRAS to wait for an EAP Response packet from the authentication server
Timeout period for the BRAS to wait for an EAP-Response/Identity packet from the client and the number of retransmissions of EAP-Request/Identity packets
Number of and timeout period for handshake packet retransmissions between the EAP client and server
IP address of the RADIUS server
Address pool name, gateway address, IP address range, and DNS server address
Procedure
- Configure a dot1x template.
<HUAWEI> system-view [~HUAWEI] sysname Router [*HUAWEI] commit [~Router] dot1x-template 4 [*Router-dot1x-template-4] authentication timeout 20 [*Router-dot1x-template-4] request interval 20 retransmit 3 [*Router-dot1x-template-4] reauthentication interval 1800 [*Router-dot1x-template-4] keepalive interval 15 retransmit 2 [*Router-dot1x-template-4] commit [~Router-dot1x-template-4] quit
- Configure an authentication scheme.
[~Router] aaa [~Router-aaa] authentication-scheme auth4 [*Router-aaa-authen-auth4] authentication-mode radius [*Router-aaa-authen-auth4] commit [~Router-aaa-authen-auth4] quit
- Configure an accounting scheme.
[~Router-aaa] accounting-scheme acct4 [*Router-aaa-accounting-acct4] accounting-mode radius [*Router-aaa-accounting-acct4] commit [~Router-aaa-accounting-acct4] quit [~Router-aaa] quit
- Configure a RADIUS server group.
[~Router] radius-server group rd4 [*Router-radius-rd4] radius-server authentication 192.168.7.249 1645 [*Router-radius-rd4] radius-server accounting 192.168.7.249 1646 [*Router-radius-rd4] radius-server shared-key Huawei [*Router-radius-rd4] radius-server type plus11 [*Router-radius-rd4] commit [~Router-radius-rd4] quit
- Configure an address pool.
[~Router] ip pool pool4 bas local [*Router-ip-pool-pool4] gateway 10.82.1.1 255.255.255.0 [*Router-ip-pool-pool4] section 0 10.82.1.2 10.82.1.200 [*Router-ip-pool-pool4] dns-server 192.168.7.252 [*Router-ip-pool-pool4] commit [~Router-ip-pool-pool4] quit
- Configure a domain named isp4.
[~Router] aaa [~Router-aaa] domain isp4 [*Router-aaa-domain-isp4] authentication-scheme auth4 [*Router-aaa-domain-isp4] accounting-scheme acct4 [*Router-aaa-domain-isp4] commit [~Router-aaa-domain-isp4] radius-server group rd4 [*Router-aaa-domain-isp4] commit [~Router-aaa-domain-isp4] ip-pool pool4 [*Router-aaa-domain-isp4] dot1x-template 4 [*Router-aaa-domain-isp4] commit [~Router-aaa-domain-isp4] quit [~Router-aaa] quit
- Configure a BAS interface.
[~Router] interface gigabitEthernet 0/1/2.1 [*Router-GigabitEthernet0/1/2.1] commit [~Router-GigabitEthernet0/1/2.1] user-vlan 100 [~Router-GigabitEthernet0/1/2.1-vlan-100-100] quit [~Router-GigabitEthernet0/1/2.1] bas [~Router-GigabitEthernet0/1/2.1-bas] access-type layer2-subscriber [*Router-GigabitEthernet0/1/2.1-bas] default-domain authentication isp4 [*Router-GigabitEthernet0/1/2.1-bas] authentication-method dot1x [*Router-GigabitEthernet0/1/2.1-bas] commit [~Router-GigabitEthernet0/1/2.1-bas] quit [~Router-GigabitEthernet0/1/2.1] quit
Configuration Files
#
sysname Router
#
radius-server group rd4
radius-server authentication 192.168.7.249 1645 weight 0
radius-server accounting 192.168.7.249 1646 weight 0
radius-server shared-key %^%#`E)v.Q@BHVzxxZ;ij{>&_M0!TGP7YRA@8a7mq<\/%^%#
radius-server type plus11
radius-server traffic-unit kbyte
#
interface GigabitEthernet0/1/2.1
user-vlan 100
bas
access-type layer2-subscriber default-domain authentication isp4
authentication-method dot1x
#
ip pool pool4 bas local
gateway 10.82.1.1 255.255.255.0
section 0 10.82.1.2 10.82.1.200
dns-server 192.168.7.252
#
dot1x-template 4
authentication timeout 20
request retransmit 3 interval 20
reauthentication interval 1800
keepalive retransmit 2 interval 15
#
aaa
authentication-scheme auth4
accounting-scheme acct4
domain isp4
authentication-scheme auth4
accounting-scheme acct4
radius-server group rd4
dot1x-template 4
ip-pool pool4
#
return