Example for Configuring DNS Redirect for Web Authentication of Layer 2 IPoE Users
This section provides an example for configuring DNS redirect for web authentication of Layer 2 IPoE users.
Networking Requirements
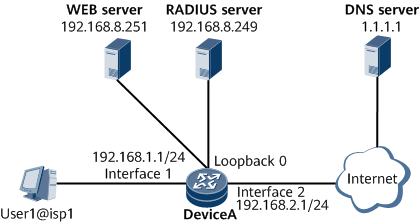
On the network shown in Figure 1, the user belongs to the isp1 domain. DNS redirect, RADIUS authentication, and RADIUS accounting are used. The user accesses the network in Layer 2 IPoE access mode through GE 0/1/2 of DeviceA.
Configuration Roadmap
The configuration roadmap is as follows: (All the configurations are performed on DeviceA.)
Configure a user group.
Configure an address pool.
Configure authentication and accounting schemes.
Configure a RADIUS server group.
Configure web pre-authentication and authentication domains.
Configure a web authentication server.
Configure ACL rules and a traffic policy.
Configure whitelists.
Configure a BAS interface and an upstream interface.
Data Preparation
To complete the configuration, you need the following data:
Authentication scheme name and authentication mode
Accounting scheme name and accounting mode
RADIUS server group name, RADIUS authentication server's IP address and port number, and RADIUS accounting server's IP address and port number
IP address pool name, gateway address, and DNS server address
Domain names
Address of the web server and web authentication server (in this example, the two servers are deployed on the same device that supports DNS)
ACL rules
Traffic policies
Whitelist configuration
BAS interface parameters
Procedure
- Configure a user group.
<HUAWEI> system-view [~HUAWEI] sysname DeviceA [*HUAWEI] commit [~DeviceA] user-group huawei
- Configure a local address pool on the Device.
[~DeviceA] ip pool huawei bas local [*DeviceA-ip-pool-huawei] gateway 10.10.10.1 24 [*DeviceA-ip-pool-huawei] commit [~DeviceA-ip-pool-huawei] section 0 10.10.10.2 10.10.10.200 [~DeviceA-ip-pool-huawei] quit
- Configure AAA schemes.
# Configure an authentication scheme.
[~DeviceA] aaa [*DeviceA-aaa] authentication-scheme auth2 [*DeviceA-aaa-authen-auth2] authentication-mode radius [*DeviceA-aaa-authen-auth2] commit [~DeviceA-aaa-authen-auth2] quit [~DeviceA-aaa] authentication-scheme none [*DeviceA-aaa-authen-none] authentication-mode none [*DeviceA-aaa-authen-none] commit [~DeviceA-aaa-authen-none] quit
# Configure an accounting scheme.
[~DeviceA-aaa] accounting-scheme acct2 [*DeviceA-aaa-accounting-acct2] accounting-mode radius [*DeviceA-aaa-accounting-acct2] commit [~DeviceA-aaa-accounting-acct2] quit [~DeviceA-aaa] accounting-scheme none [*DeviceA-aaa-accounting-none] accounting-mode none [*DeviceA-aaa-accounting-none] commit [~DeviceA-aaa-accounting-none] quit [~DeviceA-aaa] quit
- Configure a RADIUS server group.
[~DeviceA] radius-server group rd2 [*DeviceA-radius-rd2] radius-server authentication 192.168.8.249 1812 [*DeviceA-radius-rd2] radius-server accounting 192.168.8.249 1813 [*DeviceA-radius-rd2] radius-server shared-key Huawei [*DeviceA-radius-rd2] commit [~DeviceA-radius-rd2] quit
- Configure domains and DNS redirect.
# Configure a web pre-authentication domain named web_before. Then, configure DNS redirect.
[~DeviceA] aaa [~DeviceA-aaa] domain web_before [*DeviceA-aaa-domain-web_before] authentication-scheme none [*DeviceA-aaa-domain-web_before] accounting-scheme none [*DeviceA-aaa-domain-web_before] commit [~DeviceA-aaa-domain-web_before] user-group huawei [~DeviceA-aaa-domain-web_before] dns primary-ip 1.1.1.1 [*DeviceA-aaa-domain-web_before] dns-redirect web-server 192.168.8.251 [*DeviceA-aaa-domain-web_before] commit [~DeviceA-aaa-domain-web_before] ip-pool huawei [~DeviceA-aaa-domain-web_before] quit
# Configure a web authentication domain named isp1.
[~DeviceA-aaa] domain isp1 [*DeviceA-aaa-domain-isp1] authentication-scheme auth2 [*DeviceA-aaa-domain-isp1] accounting-scheme acct2 [*DeviceA-aaa-domain-isp1] commit [~DeviceA-aaa-domain-isp1] radius-server group rd2 [*DeviceA-aaa-domain-isp1] commit [~DeviceA-aaa-domain-isp1] quit [~DeviceA-aaa] quit
- Configure a loopback interface.
[~DeviceA] interface LoopBack 0 [*DeviceA-LoopBack0] ip address 192.168.8.1 32 [*DeviceA-LoopBack0] commit [~DeviceA-LoopBack0] quit

The loopback interface must be routable to the DNS server.
- Configure a web authentication server.
[~DeviceA] web-auth-server enable [~DeviceA] web-auth-server source interface LoopBack0 [~DeviceA] web-auth-server source-ip 192.168.8.1 [~DeviceA] web-auth-server 192.168.8.251 key cipher Huawei
- Configure traffic policies.
- Configure whitelists.
[~DeviceA] dns-url permit www.huawei.com [~DeviceA] dns-url permit 192.168.2.1
- Configure interfaces.
# Configure a BAS interface.
[~DeviceA] interface GigabitEthernet 0/1/2.1 [*DeviceA-GigabitEthernet0/1/2.1] commit [~DeviceA-GigabitEthernet0/1/2.1] user-vlan 1 [~DeviceA-GigabitEthernet0/1/2.1-vlan-1-1] quit [~DeviceA-GigabitEthernet0/1/2.1] bas [~DeviceA-GigabitEthernet0/1/2.1-bas] access-type layer2-subscriber default-domain pre-authentication web_before authentication isp1 [*DeviceA-GigabitEthernet0/1/2.1-bas] commit [~DeviceA-GigabitEthernet0/1/2.1-bas] authentication-method web [~DeviceA-GigabitEthernet0/1/2.1-bas] quit [~DeviceA-GigabitEthernet0/1/2.1] quit
# Configure an upstream interface connecting the BRAS to the Internet.
[~DeviceA] interface GigabitEthernet 0/1/1 [*DeviceA-GigabitEthernet0/1/1] ip address 192.168.2.1 255.255.255.0 [*DeviceA-GigabitEthernet0/1/1] commit [~DeviceA-GigabitEthernet0/1/1] quit [~DeviceA] quit
- Verify the configuration.
After completing the configurations, have the user go online. Then, run the display access-user domain command to check information about the user in the domain. The command output shows that the user has gone online successfully.
<DeviceA> display access-user domain web_before ------------------------------------------------------------------------------ UserID Username Interface IP address MAC Vlan IPv6 address Access type ------------------------------------------------------------------------------ 20 user1@web_before GE0/1/2.1 10.10.10.200 00e0-fc12-3456 1/- - IPOE ------------------------------------------------------------------------------
Normally, after the user opens a browser on the PC and enters an HTTP or HTTPS address in the address bar, a web authentication page is displayed. The user then enters the username and password. If the user is authenticated, it can enter the post-authentication domain.
<DeviceA> display access-user domain isp1 ------------------------------------------------------------------------------ UserID Username Interface IP address MAC Vlan IPv6 address Access type ------------------------------------------------------------------------------ 20 user1@isp1 GE0/1/2.1 10.10.10.200 00e0-fc12-3456 1/- - IPOE ------------------------------------------------------------------------------
Configuration Files
# sysname DeviceA # radius-server group rd2 radius-server shared-key-cipher %^%#`E)v.Q@BHVzxxZ;ij{>&_M0!TGP7YRA@8a7mq<\/%^%# radius-server authentication 192.168.8.249 1812 weight 0 radius-server accounting 192.168.8.249 1813 weight 0 # ip pool huawei bas local gateway 10.10.10.1 255.255.255.0 section 10.10.10.2 10.10.10.200 # user-group huawei # acl number 6000 rule 5 permit ip source user-group huawei destination ip-address 1.1.1.1 0 rule 15 permit ip source user-group huawei destination ip-address 192.168.8.251 0 # acl number 6001 rule 5 permit ip source user-group huawei # acl number 6002 rule 5 permit udp source-port eq dns destination user-group huawei # traffic classifier c1 operator or if-match acl 6000 precedence 8 # traffic classifier c2 operator or if-match acl 6001 precedence 9 # traffic classifier c3 operator or if-match acl 6002 precedence 10 # traffic behavior b1 # traffic behavior b2 deny # traffic behavior b3 dns-redirect # traffic policy p1 classifier c1 behavior b1 precedence 1 classifier c2 behavior b2 precedence 2 # traffic policy p2 classifier c3 behavior b3 precedence 1 # aaa # authentication-scheme none authentication-mode none # authentication-scheme auth2 # accounting-scheme acct2 # domain isp1 authentication-scheme auth2 accounting-scheme acct2 radius-server group rd2 # domain web_before authentication-scheme none accounting-scheme none ip-pool huawei dns primary-ip 1.1.1.1 user-group huawei dns-redirect web-server 192.168.8.251 # interface GigabitEthernet0/1/1 ip address 192.168.2.1 255.255.255.0 # interface GigabitEthernet0/1/2 undo shutdown # interface GigabitEthernet0/1/2.1 user-vlan 1 bas # access-type layer2-subscriber default-domain pre-authentication web_before authentication isp1 authentication-method web # # interface LoopBack0 ip address 192.168.8.1 255.255.255.255 # web-auth-server enable web-auth-server source interface LoopBack0 web-auth-server 192.168.8.251 port 50100 key cipher %^%#`E)v.Q@BHVzxxZ;ij{>&_M0!TGP7YRA@8a7mq<\/%^%# # undo web-auth-server source-ip all web-auth-server source-ip 192.168.8.1 # undo web-auth-server source-ipv6 all # dns-url permit 192.168.2.1 dns-url permit www.huawei.com # traffic-policy p1 inbound traffic-policy p2 outbound # return