Example for Configuring User Access in L2TP over IPsec Scenarios
This section provides an example for configuring user access in L2TP over IPsec scenarios.
Networking Requirements
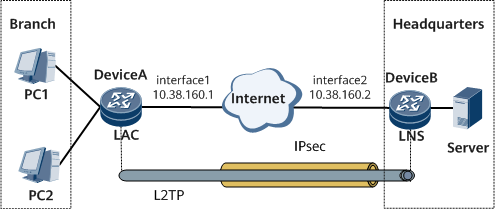
In Figure 1, the headquarters has branches in other cities. It is required that the headquarters provide L2TP access services for branch users and allow access of any user in a branch. In addition, when a branch accesses the headquarters, data must be encrypted to prevent data theft. The branch user (PC1) is connected to the PSTN through a modem and accesses the LAC (DeviceA). The LAC is connected to the LNS (DeviceB) at the headquarters through the WAN. The L2TP tunnel between the LAC and LNS runs over an IPsec IKE tunnel. The data packet transmission process is as follows: The LAC performs L2TP encapsulation and then IPsec encapsulation on the data packets. The encapsulated data is transmitted to the LNS at the headquarters through the L2TP over IPsec tunnel. After receiving the packet, the LNS at the headquarters restores the data in the packets based on the configured IPsec policy.
The device requirements are as follows:
- DeviceA (LAC) can initiate IKE negotiation with the LNS and go online through PPP dial-up.
- DeviceB (LNS side) can perform IKE negotiation with the LAC, receive PPP requests, and assign an IP address to DeviceA.
In this example, IPsec is configured in IKE mode. The encapsulation mode is tunnel mode, the authentication algorithm is SHA2-256, the encryption algorithm is AES-CBC 256, and the integrity algorithm is HMAC-SHA2-256.
Configuration Roadmap
The configuration roadmap is as follows:
- Configure IP addresses for device interfaces.
- Configure an IPsec tunnel. Details are as follows:
- Configure an ACL rule group to define the data flows to be protected.
- Configure an IKE proposal and an IKE peer.
- Configure an IPsec proposal and an IPsec policy.
- Configure a static route for IPsec traffic diversion.
- Configure an L2TP tunnel between devices. Details are as follows:
- Configure an L2TP connection.
- Configure a tunnel authentication mode.
- Configure a username and a password.
- Configure user access.
Data Preparation
To complete the configuration, you need the following data:
Usernames, domain names, and passwords of the LAC and LNS (The username, domain name, and password of the LAC must be the same as those of the LNS.)
Protocol, tunnel authentication mode (CHAP is used in this example), and tunnel password used by the LNS, local name and remote name of the LNS
VT number
L2TP group number
IDs, address ranges, and address masks of remote address pools
Loopback address
Procedure
- Create a dial-up network on the user side to receive the addresses assigned by the LNS server. In the dialup terminal window that is displayed, enter the username vpdnuser@huawei.com and password Hello. (The username and password have been registered on the LNS.)
- Configure IP addresses for interfaces.
# Configure the LAC.
<Device> system-view [~Device] sysname DeviceA [*Device] commit [~DeviceA] interface gigabitethernet 0/1/0 [*DeviceA-Gigabitethernet0/1/0] ip address 10.38.160.1 255.255.0.0 [*DeviceA-Gigabitethernet0/1/0] commit [~DeviceA-Gigabitethernet0/1/0] quit [~DeviceA] interface LoopBack1 [*DeviceA-LoopBack1] ip address 10.0.0.1 255.255.255.255 [*DeviceA-LoopBack1] commit [~DeviceA-LoopBack1] quit
# Configure the LNS.
<Device> system-view [~Device] sysname DeviceB [*Device] commit [~DeviceB] interface gigabitethernet 0/1/0 [*DeviceB-Gigabitethernet0/1/0] ip address 10.38.160.2 255.255.255.0 [*DeviceB-Gigabitethernet0/1/0] commit [~DeviceB-Gigabitethernet0/1/0] quit [~DeviceB] interface LoopBack2 [*DeviceB-LoopBack2] ip address 10.0.0.2 255.255.255.255 [*DeviceB-LoopBack2] commit [~DeviceB-LoopBack2] quit [~DeviceB] lns-group group1 [*DeviceB-lns-group-group1] bind slot 1 [*DeviceB-lns-group-group1] bind source Loopback2 [*DeviceB-lns-group-group1] commit [~DeviceB-lns-group-group1] quit
- Configure an IPsec tunnel. The configuration of the LNS is similar to the configuration of the LAC. For details, see Configuration Files.
# Configure an ACL rule group to define the data flows to be protected.
[~DeviceA] acl number 3011 [*DeviceA-acl4-advance-3011] rule 5 permit ip source 10.0.0.1 0 destination 10.0.0.2 0 [*DeviceA-acl4-advance-3011] rule 10 permit ip source 10.0.0.2 0 destination 10.0.0.1 0 [*DeviceA-acl4-advance-3011] commit [~DeviceA-acl4-advance-3011] quit
# Configure an IKE proposal and an IKE peer.
[~DeviceA] ike proposal 11 [*DeviceA-ike-proposal-11] encryption-algorithm aes-cbc 256 [*DeviceA-ike-proposal-11] dh group14 [*DeviceA-ike-proposal-11] authentication-algorithm sha2-256 [*DeviceA-ike-proposal-11] integrity-algorithm hmac-sha2-256 [*DeviceA-ike-proposal-11] commit [~DeviceA-ike-proposal-11] quit [~DeviceA] ike peer l2tp [*DeviceA-ike-peer-l2tp] pre-shared-key cipher huawei_123 [*DeviceA-ike-peer-l2tp] undo version 2 [*DeviceA-ike-peer-l2tp] ike-proposal 11 [*DeviceA-ike-peer-l2tp] remote-address 10.255.255.2 [*DeviceA-ike-peer-l2tp] commit [~DeviceA-ike-peer-l2tp] quit
# Configure an IPsec tunnel.
[~DeviceA] ike v1 enable [*DeviceA] service-location 11 [*DeviceA-service-location-11] location follow-forwarding-mode [*DeviceA-service-location-11] commit [~DeviceA-service-location-11] quit [~DeviceA] service-instance-group 11 [*DeviceA-service-instance-group-11] service-location 11 [*DeviceA-service-instance-group-11] commit [~DeviceA-service-instance-group-11] quit [~DeviceA] ipsec proposal l2tp [*DeviceA-ipsec-proposal-l2tp] esp authentication-algorithm sha2-256 [*DeviceA-ipsec-proposal-l2tp] esp encryption-algorithm aes 256 [*DeviceA-ipsec-proposal-l2tp] commit [~DeviceA-ipsec-proposal-l2tp] quit [~DeviceA] ipsec policy l2tp 10 isakmp [*DeviceA-ipsec-policy-isakmp-l2tp-10] security acl 3011 [*DeviceA-ipsec-policy-isakmp-l2tp-10] ike-peer l2tp [*DeviceA-ipsec-policy-isakmp-l2tp-10] proposal l2tp [*DeviceA-ipsec-policy-isakmp-l2tp-10] commit [~DeviceA-ipsec-policy-isakmp-l2tp-10] quit [~DeviceA] interface Tunnel11 [*DeviceA-Tunnel11] ip address 10.255.255.1 255.255.255.255 [*DeviceA-Tunnel11] tunnel-protocol ipsec [*DeviceA-Tunnel11] ipsec policy l2tp service-instance-group 11 [*DeviceA-Tunnel11] commit [~DeviceA-Tunnel11] quit
# Configure a static route to divert IPsec traffic.
[~DeviceA] ip route-static 10.0.0.2 255.255.255.255 Tunnel11 10.255.255.2 [*DeviceA] ip route-static 10.255.255.2 255.255.255.255 10.38.160.2 [*DeviceA] commit
- Configure an L2TP tunnel on the LAC.
# Enable basic L2TP functions.
[~DeviceA] l2tp enable [*DeviceA] l2tp-group 1 [*DeviceA-l2tp-1] tunnel name LAC [*DeviceA-l2tp-1] start l2tp ip 10.0.0.2 [*DeviceA-l2tp-1] tunnel source LoopBack1 [*DeviceA-l2tp-1] commit
# Configure a tunnel authentication mode and set the tunnel authentication password.
[~DeviceA-l2tp-1] tunnel authentication [*DeviceA-l2tp-1] tunnel password cipher huawei_123 [*DeviceA-l2tp-1] commit [~DeviceA-l2tp-1] quit
# Set the username and password. The username and password on the LAC must be the same as those on the LNS.
[~DeviceA] local-aaa-server [~DeviceA-local-aaa-server] user vpdnuser@huawei.com password cipher huawei_123 authentication-type p [~DeviceA-local-aaa-server] quit
- Configure user access on the LAC.
# Configure a user access domain.
[~DeviceA] aaa [~DeviceA-aaa] authentication-scheme auth1 [*DeviceA-aaa-authen-auth1] authentication-mode local [*DeviceA-aaa-authen-auth1] commit [~DeviceA-aaa-authen-auth1] quit [~DeviceA-aaa] accounting-scheme default0 [*DeviceA-aaa-accounting-default0] accounting-mode none [*DeviceA-aaa-accounting-default0] commit [~DeviceA-aaa-accounting-default0] quit [~DeviceA-aaa] domain huawei.com [*DeviceA-aaa-domain-huawei.com] authentication-scheme auth1 [*DeviceA-aaa-domain-huawei.com] accounting-scheme default0 [*DeviceA-aaa-domain-huawei.com] l2tp-group 1 [*DeviceA-aaa-domain-huawei.com] commit [~DeviceA-aaa-domain-huawei.com] quit [~DeviceA-aaa] quit
# Configure a VT.[~DeviceA] interface virtual-template 1 [*DeviceA-Virtual-Template1] ppp authentication-mode chap [*DeviceA-Virtual-Template1] commit [~DeviceA-Virtual-Template1] quit
# Bind VT1 to GE0/1/8.100.[~DeviceA] interface gigabitethernet 0/1/8.100 [*DeviceA-GigabitEthernet0/1/8.100] pppoe-server bind virtual-template 1 [*DeviceA-GigabitEthernet0/1/8.100] commit [~DeviceA-GigabitEthernet0/1/8.100] user-vlan 1 100 [~DeviceA-GigabitEthernet0/1/8.100-vlan-1-100] quit
# Configure a BAS interface.[~DeviceA-GigabitEthernet0/1/8.100] bas [*DeviceA-GigabitEthernet0/1/8.100-bas] access-type layer2-subscriber default-domain authentication huawei.com [*DeviceA-GigabitEthernet0/1/8.100-bas] authentication-method ppp [*DeviceA-GigabitEthernet0/1/8.100-bas] commit [~DeviceA-GigabitEthernet0/1/8.100-bas] quit [~DeviceA-GigabitEthernet0/1/8.100] quit
- Configure an L2TP tunnel on the LNS.
# Enable basic L2TP functions.
[~DeviceB] l2tp enable [*DeviceB] l2tp-group 1 [*DeviceB-l2tp-1] tunnel name LNS [*DeviceB-l2tp-1] allow l2tp virtual-template 1 remote LAC [*DeviceB-l2tp-1] commit
# Configure a tunnel authentication mode and set the tunnel authentication password.
[~DeviceB-l2tp-1] tunnel authentication [*DeviceB-l2tp-1] tunnel password cipher huawei_123 [*DeviceB-l2tp-1] commit [~DeviceB-l2tp-1] quit
# Configure the device to perform mandatory CHAP authentication.
[~DeviceB-l2tp-1] mandatory-chap [*DeviceB-l2tp-1] commit [~DeviceB-l2tp-1] quit
# Set the username and password. The username and password on the LAC must be the same as those on the LNS.
[~DeviceB] local-aaa-server [~DeviceB-local-aaa-server] user vpdnuser@huawei.com password cipher huawei_123 authentication-type p [~DeviceB-local-aaa-server] quit
- Configure user access on the LNS.
# Configure a local IPv4 address pool.
[~DeviceB] ip pool pppoe-pool bas local [*DeviceB-ip-pool-pppoe-pool] gateway 192.168.1.1 255.255.0.0 [*DeviceB-ip-pool-pppoe-pool] section 0 192.168.1.1 192.168.255.255 [*DeviceB-ip-pool-pppoe-pool] commit [~DeviceB-ip-pool-pppoe-pool] quit
# Configure a user access domain.
[~DeviceB] aaa [~DeviceB-aaa] authentication-scheme auth1 [*DeviceB-aaa-authen-auth1] authentication-mode local [*DeviceB-aaa-authen-auth1] commit [~DeviceB-aaa-authen-auth1] quit [~DeviceB-aaa] accounting-scheme default0 [*DeviceB-aaa-accounting-default0] accounting-mode none [*DeviceB-aaa-accounting-default0] commit [~DeviceB-aaa-accounting-default0] quit [~DeviceB-aaa] domain huawei.com [*DeviceB-aaa-domain-huawei.com] authentication-scheme auth1 [*DeviceB-aaa-domain-huawei.com] accounting-scheme default0 [*DeviceB-aaa-domain-huawei.com] ip-pool pppoe-pool [*DeviceB-aaa-domain-huawei.com] commit [~DeviceB-aaa-domain-huawei.com] quit [~DeviceB-aaa] quit
- Verifying the Configurations
# After the configuration is completed and users go online, run the display l2tp tunnel command on the LAC and LNS to view the tunnel establishment status. The command output on the LNS is used as an example. If the command output contains information about the LAC and LNS, the L2TP tunnel is successfully established.
[~DeviceB] display l2tp tunnel --------------------------------------------------------- -----------tunnel information in LAC--------------------- Total 0, printed 0 --------------------------------------------------------- -----------tunnel information in LNS--------------------- The tunnel information of board 1 LocalTID RemoteTID RemoteAddress Port Sessions RemoteName --------------------------------------------------------- 13921 7958 10.0.0.1 1701 1 LAC --------------------------------------------------------- Total 1,1 printed from slot 2
Configuration Files
DeviceA configuration file
#
sysname DeviceA
#
l2tp enable
#
ike v1 enable
#
service-location 11
location follow-forwarding-mode
#
service-instance-group 11
service-location 11
#
acl number 3011
rule 5 permit ip source 10.0.0.1 0 destination 10.0.0.2 0
rule 10 permit ip source 10.0.0.2 0 destination 10.0.0.1 0
#
ike proposal 11
encryption-algorithm aes-cbc 256
dh group14
authentication-algorithm sha2-256
integrity-algorithm hmac-sha2-256
#
ike peer l2tp
pre-shared-key cipher %^%#P.To1S*u;<{B/a~F5BtGne*F*r3dU-9Wyv5v7+@/%^%#
undo version 2
ike-proposal 11
remote-address 10.255.255.2
#
ipsec proposal l2tp
esp authentication-algorithm sha2-256
esp encryption-algorithm aes 256
#
ipsec policy l2tp 10 isakmp
security acl 3011
ike-peer l2tp
proposal l2tp
#
interface Virtual-Template1
ppp authentication-mode chap
#
interface GigabitEthernet0/1/0
undo shutdown
ip address 10.38.160.1 255.255.255.0
undo dcn
#
interface GigabitEthernet0/1/8.100
pppoe-server bind Virtual-Template 1
undo shutdown
user-vlan 1 100
bas
access-type layer2-subscriber default-domain authentication huawei.com
authentication-method ppp
#
interface LoopBack1
ip address 10.0.0.1 255.255.255.255
#
interface Tunnel11
ip address 10.255.255.1 255.255.255.255
tunnel-protocol ipsec
ipsec policy l2tp service-instance-group 11
#
ip route-static 10.0.0.2 255.255.255.255 Tunnel11 10.255.255.2
ip route-static 10.255.255.2 255.255.255.255 10.38.160.2
#
l2tp-group 1
tunnel password cipher %@%##!!!!!!!!!"!!!!"!!!!(!!!!1];16qfZ81fv"uMoKKZ.1k"`AO!X2K2N.b~'NB^V!!!!!!!!!!1!!!!o/4J(q"J1F.!K9%M!6x8%@%#
tunnel name LAC
start l2tp ip 10.0.0.2
tunnel source LoopBack1
#
local-aaa-server
user vpdnuser@huawei.com password cipher %@%##!!!!!!!!!"!!!!"!!!!(!!!!1];16qfZ81wtNj:ej5XU>Jf_<1a"!)dspWPNxp5I!!!!!!!!!!1!!!!*M%{F9=pQ/,YelLM6Ad;%@%#
authentication-type p
#
aaa
accounting-scheme auth1
accounting-mode none
authentication-scheme default0
authentication-mode none
domain huawei.com
authentication-scheme auth1
accounting-scheme default0
#
return
DeviceB configuration file
#
sysname DeviceB
#
l2tp enable
#
ike v1 enable
#
service-location 11
location follow-forwarding-mode
#
service-instance-group 11
service-location 11
#
acl number 3011
rule 5 permit ip source 10.0.0.2 0 destination 10.0.0.1 0
rule 10 permit ip source 10.0.0.1 0 destination 10.0.0.2 0
#
ike proposal 11
encryption-algorithm aes-cbc 256
dh group14
authentication-algorithm sha2-256
integrity-algorithm hmac-sha2-256
#
ike peer l2tp
pre-shared-key cipher %^%#=!7vTqO+M;/c3#O/k44*7i(lHZ/.tK/d$]Bw#-F/%^%#
undo version 2
ike-proposal 11
remote-address 10.255.255.1
#
ipsec proposal l2tp
esp authentication-algorithm sha2-256
esp encryption-algorithm aes 256
#
ipsec policy-template temp11 1
security acl 3011
ike-peer l2tp
proposal l2tp
#
ipsec policy l2tp 10 isakmp template temp11
#
interface Gigabitethernet0/1/0
undo shutdown
ip address 10.38.160.2 255.255.255.0
undo dcn
#
interface Virtual-Template1
ppp authentication-mode chap
#
interface LoopBack2
ip address 10.0.0.2 255.255.255.255
#
interface Tunnel11
ip address 10.255.255.2 255.255.255.255
tunnel-protocol ipsec
ipsec policy l2tp service-instance-group 11
#
ip route-static 10.0.0.1 255.255.255.255 Tunnel11 10.255.255.1
ip route-static 10.255.255.1 255.255.255.255 10.38.160.1
#
l2tp-group 1
mandatory-chap
allow l2tp virtual-template 1 remote LAC
tunnel password cipher %@%##!!!!!!!!!"!!!!"!!!!(!!!!1];16qfZ81fv"uMoKKZ.1k"`AO!X2K2N.b~'NB^V!!!!!!!!!!1!!!!o/4J(q"J1F.!K9%M!6x8%@%#
tunnel name LNS
#
lns-group group1
bind slot 1
bind source LoopBack2
#
ip pool pppoe-pool bas local
gateway 192.168.1.1 255.255.0.0
section 0 192.168.1.1 192.168.255.255
#
local-aaa-server
user vpdnuser@huawei.com password cipher %@%##!!!!!!!!!"!!!!#!!!!(!!!!JMi&5#;qTW7C9)&16~.M{sv*SzKjgN>0b[,G:tb%!!!!!!!!!!1!!!!E'QA>XV7kJ+tIm3UL=c=%@%#
authentication-type p
#
aaa
authentication-scheme auth1
authentication-mode local
authentication-scheme default0
authentication-mode none
domain huawei.com
authentication-scheme auth1
accounting-scheme default0
ip-pool pppoe-pool
#
return