Key Data
The version file information is obtained by parsing the bootstrapping data, which consists of the conveyed information, ownership voucher, and owner certificate. As such, the bootstrapping data can be regarded as the key data for implementing SZTP.
Conveyed Information
Conveyed information consists of the redirect information and onboarding information.
- Redirect information, which may be trusted or untrusted, defines a list of bootstrap servers that a device can access.
- The trusted redirect information is obtained from a trusted source. A trusted source is configured with the bootstrap server's certificate, which is used to establish a secure channel between the device and the bootstrap server. Data that needs to be transmitted through this channel is authenticated before the channel is established, ensuring that the data is not tampered with. As a result, the ownership voucher and owner certificate are not needed.
- The untrusted redirect information can be transmitted only through insecure channels and requires a digital signature. Consequently, the ownership voucher and owner certificate are needed to ensure a chain of trust.
The following is an example of redirect information:<?xml version="1.0" encoding="utf-8"?> <conveyed-information xmlns="urn:ietf:params:xml:ns:yang:ietf-sztp-conveyed-info"> <redirect-information> <bootstrap-server> <address>192.168.1.2</address> //Indicates the IP address of the bootstrap server. <trust-anchor>base64encodedvalue==</trust-anchor> //Indicates the trust anchor certificate of the redirect server. This parameter is optional. </bootstrap-server> <bootstrap-server> <address>192.168.1.3</address> <port>445</port> //Indicates the port number of the bootstrap server. This parameter is optional, and the default value is 443. <trust-anchor>base64encodedvalue==</trust-anchor> </bootstrap-server> <bootstrap-server> <address>huawei.com</address> <port>446</port> </bootstrap-server> </redirect-information> </conveyed-information>
- SZTP currently can redirect a device to a maximum of 10 bootstrap servers.
- By loading the trusted anchor certificate, the device can establish a secure TLS connection with the redirect server. If the redirect information is untrusted, the device will discard the trusted anchor certificate.
- Onboarding information provides the paths for downloading version files (such as the system software package, configuration files, and patch files) and information such as the scripts that the device must successfully execute and the mode of processing configuration files. Onboarding information, which includes the data source and transmission channel, must be trusted.The following is an example of onboarding information:
<?xml version="1.0" encoding="utf-8"?> <conveyed-information xmlns="urn:ietf:params:xml:ns:yang:ietf-sztp-conveyed-info"> <onboarding-information> <boot-image> <download-uri>https://10.1.1.1/path/image/file.cc</download-uri> //Indicates the address for downloading version files. Currently, version files can be downloaded only through HTTPS. <download-uri>https://10.1.1.1/path/image/file.pat</download-uri> <download-uri>https://10.1.1.1/path/config/file.cfg</download-uri> <image-verification> //Indicates that version files are verified. Each version file corresponds to a <download-uri>. <hash-algorithm>ietf-sztp-conveyed-info:sha-256</hash-algorithm> //Indicates the hash algorithm type. Currently, only SHA256 is supported. <hash-value>xxxxxx</hash-value> //Indicates the hash value. </image-verification> <image-verification> <hash-algorithm>ietf-sztp-conveyed-info:sha-256</hash-algorithm> <hash-value>xxxxxx</hash-value> </image-verification> <image-verification> <hash-algorithm>ietf-sztp-conveyed-info:sha-256</hash-algorithm> <hash-value>xxxxxx</hash-value> </image-verification> </boot-image> <configuration-handling>replace</configuration-handling> //Indicates the mode of processing configuration files. Currently, configuration files can only be replaced. </onboarding-information> </conveyed-information>
Redirect information redirects a device to another bootstrap server to obtain onboarding information. In load balancing or multi-vendor interworking scenarios, the device may need to perform redirection.
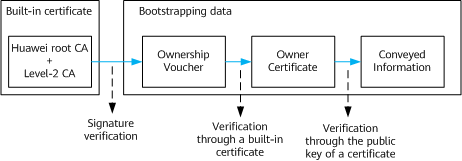
Establishing a Chain of Trust Using the Ownership Voucher and Owner Certificate
Before a device is delivered, it is configured with an IDevID. The IDevID contains information such as the ESN of the device and the public key of the identity certificate, and enables an SZTP-enabled device to establish a TLS connection with the bootstrap server. If a device does not contain a user's trusted root certificate, the device can use the ownership voucher and owner certificate to establish a secure chain of trust so that it can verify the conveyed information.
- The ownership voucher is used to identify the owner of a device. It contains the ESN of the device and is embedded with the trusted root certificate of the bootstrap server. A device vendor signs the ownership voucher and transfers it to users in the form of a CMS file.

The process of issuing the ownership voucher is as follows:
- A user sends the root certificate of the bootstrap server to Huawei technical support.
- Huawei issues the ownership voucher based on the root certificate of the bootstrap server and the ESN of the device to be deployed.
- Huawei technical support sends the ownership voucher to the user.
- The owner certificate is used to verify the signature of the conveyed information. It contains the identity certificate and intermediate certificate of the bootstrap server. Similar to the ownership voucher, the owner certificate is also transferred in the form of a CMS file.

- The bootstrap server is embedded with Huawei level-2 CA certificate, ownership voucher, and owner certificate. The issued ownership voucher is valid only when Huawei level-2 CA certificate is preset on the bootstrap server.
- The device is preconfigured with the IDevID, Huawei root CA certificate, and Huawei level-2 CA certificate.