Example for Configuring URPF
By configuring flow-based URPF, you can prevent packets of certain types from starting source address spoofing attacks.
Networking Requirements
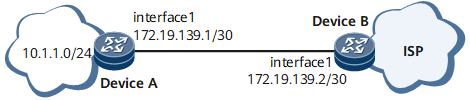
In this example, URPF is enabled on the inbound interface of the ISP. As shown in Figure 1, DeviceA (the client device) and DeviceB (the ISP device) are directly connected. URPF is enabled on GE 0/1/0 of DeviceB. Configure the URPF strict check on DeviceB and Configure an ACL to perform URPF check on the packets whose source addresses are in ACL 2010. Enable URPF on GE 0/1/0 of router A, configure the URPF strict check, and enable the default route match.
Configuration Roadmap
The configuration roadmap is as follows:
Configure a traffic policy on the ISP router to allow traffic from a certain network segment to pass the URPF check.
Configure an IP address for the interface on DeviceA and enable URPF on the interface.
Data Preparation
To configure URPF, you need the following data:
IP addresses of interfaces
Network segment that can pass the URPF check
Procedure
- Configure DeviceB.
# Configure an ACL to perform URPF check on the packets whose source addresses are in ACL 2010.
<routerB> system-view [~routerB] acl number 2010 [*routerB-acl-basic-2010] rule permit source 10.1.1.0 0.0.0.255 [*routerB-acl-basic-2010] commit [~routerB-acl-basic-2010] quit
# Configure traffic classifiers and define matching rules based on ACL numbers.
[~routerB] traffic classifier classifier1 [*routerB-classifier-classifier1] if-match acl 2010 [*routerB-classifier-classifier1] commit [~routerB-classifier-classifier1] quit
# Define a traffic behavior and configure URPF.
[~routerB] traffic behavior behavior1 [*routerB-behavior-behavior1] ip urpf strict [*routerB-behavior-behavior1] commit [~routerB-behavior-behavior1] quit
# Define traffic policies and associate traffic classes and traffic behaviors.
[~routerB] traffic policy policy1 [*routerB-trafficpolicy-policy1] classifier classifier1 behavior behavior1 [*routerB-trafficpolicy-policy1] commit [~routerB-trafficpolicy-policy1] quit
# Apply the traffic policy to the interface.
[~routerB] interface gigabitethernet 0/1/0 [~routerB-GigabitEthernet0/1/0] undo shutdown [*routerB-GigabitEthernet0/1/0] ip address 172.19.139.2 255.255.255.252 [*routerB-GigabitEthernet0/1/0] traffic-policy policy1 inbound [*routerB-GigabitEthernet0/1/0] commit
- Configure DeviceA
# Configure GE 0/1/0.
<routerA> system-view [~routerA] interface gigabitethernet 0/1/0 [~routerA-GigabitEthernet0/1/0] undo shutdown [*routerA-GigabitEthernet0/1/0] ip address 172.19.139.1 255.255.255.252
# Enable URPF on GE 0/1/0, set the URPF check mode to strict, and enable default route match.
[*routerA-GigabitEthernet0/1/0] ip urpf strict allow-default [*routerA-GigabitEthernet0/1/0] commit
Configuration Files
Device A configuration file
# sysname routerA # interface GigabitEthernet0/1/0 undo shutdown ip address 172.19.139.1 255.255.255.252 ip urpf strict allow-default # return
Device B configuration file
# sysname routerB # acl number 2010 rule 5 permit source 10.1.1.0 0.0.0.255 # traffic classifier classifier1 operator or if-match acl 2010 # traffic behavior behavior1 ip urpf strict # traffic policy policy1 classifier classifier1 behavior behavior1 # interface GigabitEthernet0/1/0 undo shutdown ip address 172.19.139.2 255.255.255.252 traffic-policy policy1 inbound # return