Binding Authentication Process
Binding authentication uses the physical information of user connections to automatically generate usernames and passwords for authentication, without requiring users to manually input usernames or passwords. This authentication mode is mainly used in DHCP and static access scenarios.
In binding authentication, user terminals send IP packets to a BRAS to trigger the start of the authentication process, or a BRAS initiates authentication after detecting that users are online using ARP. The BRAS generates usernames and passwords based on the user location information, such as the slot IDs, card IDs, port numbers, VLAN IDs, and DHCP Option 82 information. The BRAS then authenticates the users by itself or sends the usernames and passwords to an AAA server for authentication. Users are not aware of the binding authentication process, simplifying user access and improving service security.
Binding Authentication Process
The following describes the binding authentication processes for a DHCP user and a static user, respectively.
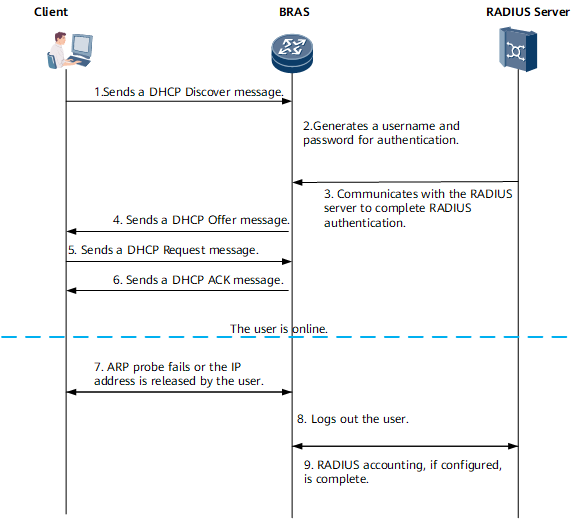
Figure 1 shows the binding authentication process for a DHCP user.
1. The user starts the terminal (or runs the ipconfig command to release the IP address in use and applies for a new IP address) and sends a DHCP Discover packet.
2. After receiving the packet, the BRAS uses the VLAN ID of the access interface to generate a username and password in binding mode for authentication.
3. The BRAS communicates with the RADIUS server to complete RADIUS authentication.
4. The standard DHCP process starts. The BRAS selects an unassigned IP address from the IP address pool and sends a DHCP Offer packet that carries the leased IP address and other settings to the user.
5. The user sends a DHCP Request packet to the BRAS. The packet carries the desired IP address.
6. The BRAS sends a DHCP ACK packet to the user. The packet carries the assigned IP address and other parameter configurations. After obtaining the IP address, the user goes online successfully.
7. The BRAS periodically sends ARP packets to detect the user's online status and maintain the link connection status. If the user fails to respond within the time limit (for example, if the user powers off the terminal, removes the network cable, or proactively releases the assigned IP address), the BRAS considers the user offline.
8. The BRAS logs out the user and completes accounting.
9. If RADIUS accounting is used, the BRAS logs out the user and completes RADIUS accounting with the RADIUS server.
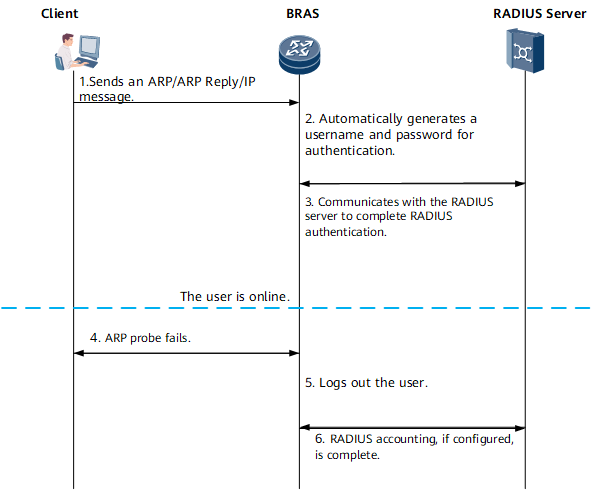
Figure 2 shows the binding authentication process for a static user.
- The user sends an ARP Request/ARP Reply/IP packet to the BRAS.
- After receiving the packet, the BRAS uses the VLAN ID of the access interface to generate a username and password in binding mode for authentication. After the user is authenticated, the user can go online successfully.
- When the user is online, the BRAS and client exchange ARP packets periodically to maintain the link status. If ARP probe fails, for example, after the client is powered off or the network cable is removed, the BRAS considers the user offline.
- The BRAS logs out the user and completes accounting.
- If RADIUS accounting is used, the BRAS logs out the user and completes RADIUS accounting with the RADIUS server.
Username Generation Mode
In binding authentication mode, if a username template is bound to the BAS interface through which users go online, the system generates usernames based on the username template. If no username template is bound to the user access interface but a mode for generating pure usernames is configured in the AAA view, the system generates pure usernames based on the configured mode. If neither of the preceding configurations is available, the system generates usernames based on the default configuration. Interface-specific configuration applies only to the interface, whereas the default configuration and the configuration in the AAA view take effect globally.
- The system uses the IP address carried in the access request packet of a user as the pure username. This method applies only to Layer 3 access users and static users whose access request packets carry IP addresses.
- The system uses the MAC address carried in the access request packet as the pure username.
- The system uses the Access-Line-Id information (DHCP Option 82) carried in the access request packet of a user as the pure username.
- The system uses the hostname configured using the sysname host-name command in the system view as the pure username.
- The system uses the combination of any of the IP address, MAC address, Access-line-id (DHCP Option 82), and hostname as the pure username. These fields are presented in the order they are configured.
- The system generates a pure username based on access interface and VLAN information of a user in the format configured using the vlanpvc-to-username command.
The system then generates a username based on the pure username, default authentication domain configured on the BAS interface, and domain name delimiter and position configured in the system. The username can be in either of the following formats: pure username+domain name delimiter+domain name (if the system is configured to place the domain name behind the domain name delimiter) or domain name+domain name delimiter+pure username (if the system is configured to place the domain name before the domain name delimiter).
Password Generation Modes
The BRAS can be configured to use any of the following methods to automatically generate a password for an IPoE user. By default, the BRAS uses a VLAD ID to automatically generate a password for an IPoE user.
- The system uses the manually configured IPoE user password.
- The system uses all or part of the Vendor-Class attribute (DHCPv4 Option 60) carried in the user's access request packet as the IPoE user password.
- The system uses all of the User-Class attribute (DHCPv4 Option 77) carried in the user's access request packet as the IPoE user password.
Advantages and Disadvantages of Binding Authentication
Advantages:
- Binding authentication uses DHCP extended fields, and therefore is applicable to scenarios in which no client program is required on user terminals so that you do not need to enter the username or password, for example, IPTV scenarios.
- If a BRAS provides the DHCP server functionality, binding authentication allows it to perform local authentication, without the need to deploy an AAA or DHCP server in actual applications.
Disadvantages:
- It takes a long time for abnormal logout detection, and therefore is inapplicable to time-based charging users. Binding authentication is applicable to IPTV monthly package users.
- When binding authentication is used, the BRAS only determines the interface number, VLAN ID of a DHCP relay agent, but not the user terminal. Therefore, binding authentication allows the BRAS to authenticate only users but not devices.