Overview of L2TP Access
Definition
Virtual Private Dial Network (VPDN) is a virtual private network implemented through the dial-in function of a public network such as an Integrated Services Digital Network (ISDN) and a Public Switched Telephone Network (PSTN) and access networks. This technology is often used to provide remote access for enterprises, small Internet Service Providers (ISPs), mobile staff.
Adopting a special encryption communication protocol, the VPDN sets up safe virtual private networks over a public network for enterprises. In this manner, international offices of enterprises and staff traveling on business can access the headquarters across the public network through an encrypted virtual tunnel. Users on the public network, however, cannot access the resources inside the enterprise network through this virtual tunnel.
Among multiple protocols used by VPDN tunnels, the most popular protocol is the Layer 2 Tunneling Protocol (L2TP).
PPP defines an encapsulation mechanism for transmitting multi-protocol packets across Layer 2 point-to-point links. Therefore, it needs to be run on the connections between users and Network Access Servers (NASs).
L2TP supports the tunneling of PPP-encapsulated packets. It extends the PPP model by allowing the Layer 2 and PPP endpoints to reside on different devices interconnected through the packet switching technology.
With L2TP, a user can set up an end-to-end PPP session on a non-point-to-point network. L2TP combines advantages of the Layer 2 Forwarding (L2F) and Point-to-Point Tunneling protocol (PPTP), and therefore is standardized by the IETF.
L2TP involves the following concepts:
Users
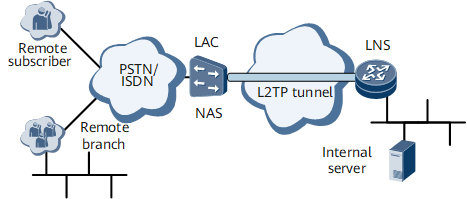
In an L2TP networking, users are devices (such as PCs) to access a private network. The access modes and locations of VPDN users are always changing. In this situation, VPDN users can set up connections with an L2TP Access Concentrator (LAC) through the PSTN or ISDN or directly accesses the Internet to communicate with the server of the headquarters.
A user is always the initiator of a PPP negotiation. Therefore, the user is both a Layer 2 PPP link end and a PPP session end.
LAC
An L2TP Access Concentrator (LAC) is a device on the switched network, with the capability of terminating PPP packets and performing L2TP functions. Usually, the LAC is an access device of the local ISP, such as the NAS, which provides access services for users through the PSTN or ISDN.
The LAC tunnels individual PPP packets to the NAS through L2TP tunnels and PPP sessions. An LAC can provide services not only for a specified VPN but also for multiple VPNs.
The LAC sits between the L2TP Network Server (LNS) and a remote system (remote subscribers and branches), as shown in Figure 1.
The LAC exchanges packets between the LNS and the remote system. It sends packets from the remote system to the LNS after the L2TP encapsulation process, and sends packets from the LNS to the remote system after the decapsulation process.
The LAC and the remote system can be connected through local links or PPP links. Usually, PPP links are used between VPDN users and the LAC. The LAC is both an end to responds to users' requests and a PPP link end.
LNS
An L2TP Network Server (LNS) is a PPP session end. Users who pass the authentication on the LNS can access the private network. The LNS acts as one side of an L2TP tunnel endpoint and is a peer to the LAC. It is the logical termination point of a PPP session that is being tunneled from the remote system by the LAC.
The LNS sits at the boundary between the private and public networks, and is usually a gateway device. The gateway provides the network access and LNS functions.
Two types of messages utilized by L2TP
Control messages are used in the establishment, maintenance, and teardown of tunnels and sessions. In addition, control messages are used in transmission control. The L2TP tunnel applies mechanisms (such as packet retransmission and periodical detection of the tunnel connectivity) to guarantee the reliable transmission of control messages. In addition, the L2TP tunnel supports the traffic and congestion control over the control messages.
Data messages encapsulate PPP frames and are transmitted over the tunnel. Data messages are not retransmitted if message loss occurs. The L2TP tunnel does not support the traffic and congestion control over data messages.
AVP
Parameters in control messages are identified by Attribute Value Pairs (AVPs). This can increase the interoperability and scalability of L2TP. Control messages contain multiple AVPs.
Control connections and session connections
L2TP is connection-oriented. There are two types of connections between a pair of LNS and LAC:
A control connection that defines a pair of LNS and LAC and controls the establishment, maintenance and teardown of tunnels and sessions. The procedures for establishing a control connection involve the exchange of information about identity protection, L2TP version, frame type, and parameters of the physical links.
A session connection is a PPP session multiplexed on the tunnel connections.
Multiple L2TP tunnels can be set up between a pair of LNS and LAC. A tunnel consists of a control connection and one or more session connections. A session connection can be set up only after a control connection is set up. Each session corresponds to a PPP data flow transmitted between the LAC and LNS.
Control messages and data messages (PPP messages) are transmitted through tunnels.
Purpose
Advantages L2TP are as follows:
Flexible authentication mechanism and high security
L2TP itself cannot guarantee the connection security. It utilizes an authentication mechanism (such as CHAP and PAP) provided by PPP and therefore possesses all PPP security features.
L2TP can be applied with encryption technologies (such as tunnel encryption, end-to-end data encryption, and link layer data encryption) as required to increase the security.
Multi-protocol transmission
L2TP transmits PPP packets. PPP itself supports the transmission of multi-protocol packets. Therefore, multi-protocol packets (even packets of link layer protocols, such as Ethernet packets) can be encapsulated in PPP packets and are transmitted by L2TP.
RADIUS authentication
An LAC sends a user name and password to a RADIUS server for authentication.
Obtainment of RADIUS attributes from a RADIUS server
A RADIUS server delivers attributes and dynamically allocates VPN attributes to users.
Private address allocation
An LNS can be placed behind the firewall of the enterprise network to perform the dynamic address allocation and management, and support private address application (RFC1918, Address Allocation for Private Internets).
Flexible network accounting
Both the ISP (LAC) and the gateway of the enterprise network (LNS) can perform the accounting function. L2TP provides accounting information, such as the number of transmitted packets, number of bytes, start and end point of the connection, and ending time.
Reliability
L2TP sets up the backup LNS. When the master LNS becomes unavailable, the backup LNS sets up a connection with the LAC, therefore enhancing the reliability and fault tolerance ability of the VPN services.
L2TP supports load balancing on an LNS. When an L2TP connection is set up on a LAC, the LAC can be configured with or obtain from a RADIUS server multiple LNSs' IP addresses. The LAC then allocates sessions to these LNSs.
Benefits
L2TP brings remarkable benefits to carriers:
Provides an authenticatable and a manageable tunnel transmission mechanism.
Provides a flexible mode for batch transmission. In this mode, L2TP services can be authenticated and charged by both the carrier and the ISP.