Application Scenarios for 802.1x Access
The networking of 802.1X port-based authentication is similar to that of IPoE, IPoEoVLAN, and IPoEoQ. The supplicant's Ethernet interface encapsulates EAP packets into EAP over LAN (EAPOL) packets, which can reach the authenticator directly or through a LAN switch or DSLAM after the LAN switch adds VLAN tags or the DSLAM performs AAL5 encapsulation.
Through EAPOL packet decapsulation and VLAN tag identification, the authenticator obtains user physical information, user names, and passwords from the packets to prepare data for user access authentication.
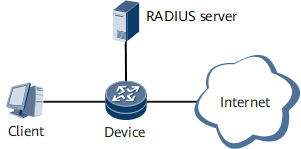
Figure 1 shows the typical networking for 802.1X port-based authentication. The authenticator performs access authentication for the supplicant.
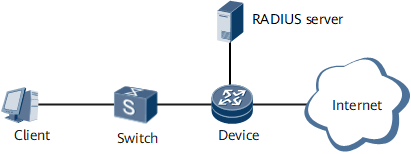
Figure 2 shows the networking for 802.1XoEoV port-based authentication. Single VLAN tags are added to supplicant packets on the switch, and the packets are then sent to the authenticator for access authentication.
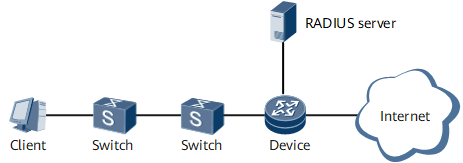
Figure 3 shows the networking for 802.1XoEoQ port-based authentication. Single VLAN tags are added to supplicant packets on each switch, and the packets are then sent to the authenticator for access authentication.