802.1X Access Fundamentals
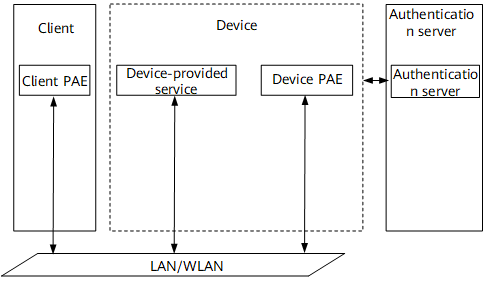
As shown in Figure 1, the three major components of the 802.1x authentication system are the client, device, and authentication server.
The client is at one end of a point-to-point (P2P) LAN segment and is authenticated by the device that is connected to the client through a link. Commonly, the client is a user terminal. The user initiates 802.1x authentication by starting the client software. The client must support EAP over LAN (EAPoL).
The device is at the other end of the P2P LAN segment and authenticates the client that is connected to the device through a link. Commonly, the device supports an 802.1x standard. The device provides the client with a LAN-accessing interface, which can be a physical interface (for example, an Ethernet interface on an Ethernet switch) or a logical interface (for example, the user MAC address or the VLAN ID).
The authentication server is an entity that provides authentication services for the device. The authentication server undertakes authentication, authorization, and accounting for users. You are recommended to use a RADIUS server as the authentication server.
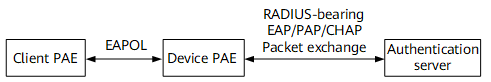
In the 802.1x authentication system, the authentication server and client exchange authentication information through EAP. Between the client Port Access Entity (PAE) and the device PAE, EAPoL encapsulation is adopted for EAP packets.
Between the device PAE and the RADIUS server, EAP packets can adopt EAP over RADIUS (EAPoR) encapsulation and be borne by RADIUS. EAP packets can be terminated on the device PAE. In this case, Password Authentication Protocol (PAP) or Challenge Handshake Authentication Protocol (CHAP) packets are transmitted between the device PAE and the RADIUS server.
The device PAE is isolated from the authentication function. The RADIUS server can authenticate the client PAE through any of several authentication mechanisms such as MD5-challenge, PAP, and EAP-PEAP.
The device PAE determines the status (authorized/unauthorized) of the controlled interface according to the instructions (accept/reject) from the RADIUS server.
Figure 2 shows the protocol structure of the 802.1x authentication system.