DSVPN IPsec Protection
If an enterprise needs to protect the security of data transmitted between the headquarters and branches or between branches through encryption on a DSVPN, bind an IPsec profile to the DSVPN to dynamically establish mGRE and IPsec tunnels between branches.
- The establishment of an mGRE tunnel immediately triggers the establishment of an IPsec tunnel.
- The common IPsec technology uses an ACL to identify unicast traffic to be encrypted. An IPsec security policy requires the definition of complex ACL rules, complicating implementation. If deployed with IPsec, a DSVPN using NHRP and mGRE technologies can guarantee high security for data transmission while simplifying network deployment.
- An IPsec tunnel is dynamically established between branches, preventing IPsec data exchanged between branch spokes from being decrypted and then encrypted by the hub, which in turn reducing the delay in data transmission.
Figure 1 DSVPN IPsec protection
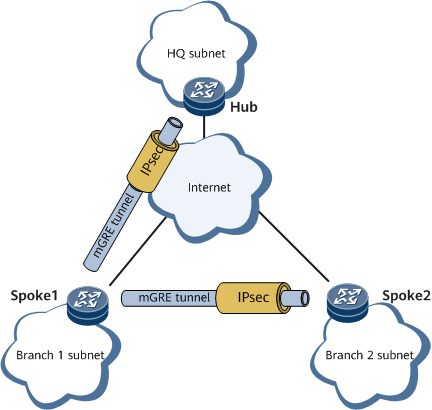

On a DSVPN, IPsec profiles are configured on the mGRE interfaces of the hub and spokes. The DSVPN over IPsec mechanism works as follows:
- All the spokes on the network send registration requests to the hub and report the NHRP peer information to IPsec. The Internet Key Exchange (IKE) modules of the spokes and hub negotiate IPsec tunnel parameters with each other.
- The hub records mappings between tunnel addresses and public network addresses of the spokes and generates NHRP peer entries for the spokes based on registration requests received. The hub then sends registration replies to spokes.
- The spokes establish an mGRE tunnel upon traffic transmission request. For details about how to establish an mGRE tunnel, see DSVPN Principles in Non-Shortcut Scenarios and DSVPN Principles in Shortcut Scenarios.
- After the spokes establish an mGRE tunnel, the IPsec module obtains NHRP peer information, adds or deletes IPsec peers based on the information, and triggers the spokes to dynamically establish an IPsec tunnel.
- After an IPsec tunnel is established between the spokes, packets are routed based on destination IP addresses. If the outbound interface is an mGRE interface, the spoke searches the NHRP peer table for the public network address corresponding to the next hop of the route. After obtaining the public network address, the spoke searches for a matching IPsec security association (SA) to encrypt the packets.

Digital envelop authentication is not supported when NHRP and IPsec are both configured.