ACLs Applied to Telnet (VTY), SNMP, FTP & TFTP
Filtering Principle
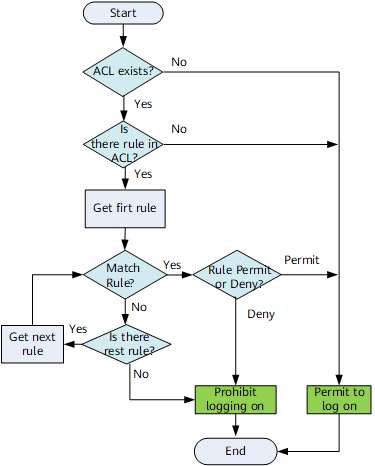
When an ACL is applied to Telnet, SNMP, FTP or TFTP:
- If the source IP address of the user matches the permit rule, the user is allowed to log on.
- If the source IP address of the user matches the deny rule, the user is prohibited from logging on.
- If the source IP address of the user does not match any rule in the ACL, the user is prohibit logging on.
- If there is no rule in the ACL, or the ACL does not exist, all users are allowed to log in.

The default behavior is deny if the source IP address of the user does not match any rule in the ACL applied to FTP.
When an ACL is applied to SNMP, if receiving a packet with the community name field being null, the device directly discards the packet without filtering the packet based on the ACL rule. In addition, the log about the community name error is generated. ACL filtering is triggered only when the community name is not null.
Example of ACLs Applied to Telnet (VTY)
On an IP bearer network, an ACL is applied to the device VTP for network access security, so that only the NMS server (IP address: 10.0.102.113) in the attached NM VPN can log in to the device.
Configurations:
# acl 2013 //Create a basic ACL with the number 2013. rule 5 permit vpn-instance vpna source 10.0.102.113 0 ////Permit the source IP 10.0.102.113 in the vpn-instance vpna to log in to the device. rule 500 deny //Forbid other terminals to log in to the device # user-interface vty 0 4 acl 2013 inbound //Restrict VTY0 to VTY4's access to the device. authentication-mode aaa protocol inbound all # user-interface vty 5 14 acl 2013 inbound //Restrict VTY5 to VTY14's access to the device.

If the NMS server belongs to a VPN, the VPN instance must be configured in the rule of ACL.
An ACL can be referenced in the VTY user interface accessed using Telnet only after user authentication is successful. After a TCP connection is set up, to reference the ACL, you need to perform the following operations:
- If the login mode configured in the VTY user interface is SSH login, run the ssh server acl command.
- If the login mode configured in the VTY user interface is Telnet login, run the telnet server acl command.
Example of ACLs Applied to FTP
A device is connected to two network segments: 10.1.1.0/24 and 10.1.2.0/24. In the network segment 10.1.1.0/24, a server provides web services and its IP address is 10.1.1.19.
Configure the following steps to implement that all hosts in these network segments are allowed to establish the FTP connection with the device except for this server (10.1.1.19).
# acl 2013 //Create a basic ACL with the number 2013. rule 5 deny source 10.1.1.19 0 // Deny the server at 10.1.1.19/32. rule 10 permit source 10.1.1.0 0.0.0.255 // Allow other hosts in network segment 10.1.1.0/24. rule 15 permit source 10.1.2.0 0.0.0.255 // Allow the hosts in network segment 10.1.2.0/24. # ftp acl 2013 // After ACL 2013 is applied to FTP, all IP addresses in the network segment 10.1.1.0/24 are allowed to establish the FTP connection with the device except for the address 10.1.1.19.