ACLs Applied to a Route-Policy
About Route Policy
Route-policy can use ACL, IP-prefix, AS-Path filter, community-filter, extcommunity-filter, RD-filter, Route-Policy to define matching rules as shown in the following:
# route-policy a permit node 1 if-match acl 2000 if-match as-path-filter 2 apply local-preference 20 # route-policy a permit node 2 if-match acl 2001 if-match as-path-filter 3 apply cost 1000 # route-policy a permit node 3 if-match ip-prefix prefix1
A Route-policy can have multiple nodes. The logic between the nodes is "OR". The device processes the nodes according to the ascending order of the node number. If the route matches one of the nodes, the route is considered to match the policy, and the matching action is not continued for the matched routes.
Each node can have one or more if-match clauses and apply clauses.
The if-match clauses define the matching rules and the matching objects are route attributes. The logic between the if-match clauses in the same node is "AND". If the route matches all the if-match clauses, the route is considered to match the node. If the route does not match all the if-match clauses of the node, the route continues to be matched against the next node.
The apply clauses define the action applied to the route that matches the node.
Matching Principle of ACLs Applied to a Route-policy
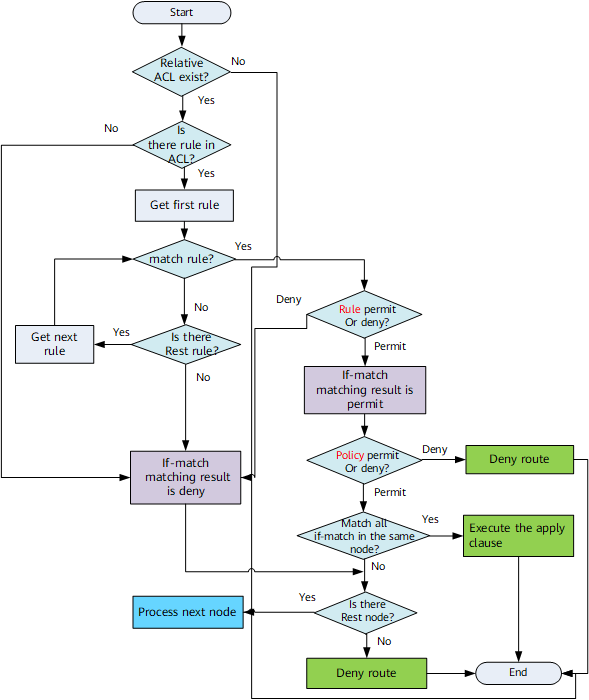
Node Action |
ACL Action |
Route Matches ACL Rule or Not |
Result |
|---|---|---|---|
Permit |
Permit |
Yes |
The route is considered to match the if-match clause, and the device continues to process the rest if-match clauses in the same node.
|
No |
The route is considered to not match the if-match clause, and the apply clause is not executed. The device just continues to process the rest nodes for the route. If there is no rest node, the mismatched route is "deny". |
||
Permit |
Deny |
Yes |
The node does not take effect, and the device just continues to process the rest nodes for the route. If there is no rest node, the route is "deny". |
No |
|||
Deny |
Permit |
Yes |
The route is "deny", and the apply clause is not executed. And the device does not continue to process the rest nodes for the route. |
No |
The route does not match the if-match clause, and the apply clause is not executed. The device just continues to process the rest nodes for the route. If there is no rest node, the route is "deny". |
||
Deny |
Deny |
Yes |
The node does not take effect, and the device just continues to process the rest nodes for the route. If there is no rest node, the route is "deny". |
No |

- The device continues to process the rest nodes if the route is deny by the ACL.
The device continues to process the rest nodes if the route does not match any rule in the ACL.
- It is recommended that you configure deny rules with smaller numbers to filter out the unwanted routes. Then, configure permit rules with larger numbers in the same ACL to receive or advertise the other routes.
- It is recommended that you configure permit rules with a smaller number to permit the routes to be received or advertised by the device. Then, configure deny rules with larger numbers in the same ACL to filter out unwanted routes.
ACL Matching Result |
Route-policy Processing Result |
|---|---|
The relative ACL does not exist |
Route policy does not support this kind of ACL. |
The relative ACL exists and there are rules in the ACL, but the rule matching result is "mismatched". |
The if-match clause matching result is set as "deny". The device stops to process the other if-match clauses, and the apply clause is not executed.
|
The relative ACL exists but there is no rule in the ACL. |
If Unsupported ACL Filter Option Applied to a Route-policy
Only numbered basic ACL (rule ID ranges from 2000 to 2999) can apply to route-policy.
The numbered basic ACL and named ACL applied to route-policy support only two matching options, source-address and the time-range, not support other options (such as destination-address, vpn-instance).
If the unsupported matching option is configured for route-policy, the matching result of the option is "permit".
Example1
In the following configurations, the result is, all static routes are imported to BGP, and the local-preferences of all routes are modified.
acl number 2000 rule 5 deny source 10.1.0.0 0.0.0.255 # route-policy policy1 permit node 10 if-match acl number 2000 apply local-preference 1300 # bgp 100 import-route static route-policy policy1 #
Example2
In the following configurations, the result is, only the static route 10.1.1.1/24 can be imported to BGP, and the local-preferences of all routes are modified.
acl number 2000 rule 5 permit source 10.1.1.1 0.0.0.255 # route-policy policy1 permit node 10 if-match acl 2000 apply local-preference 1300 # bgp 100 import-route static route-policy policy1 #
Example3
In the following configurations, the result is, all routes to 10.1.0.0/24 cannot be advertised to BGP VPNv4 peer 1.1.1.1, no matter the L3VPNs the denied routes belong to. The "vpn-instance vpnb" does not take effect.
acl number 2000 rule 5 deny source 10.1.0.0 0.0.0.255 vpn-instance vpnb rule 10 permit # route-policy policy1 permit node 10 if-match acl 2000 # bgp 100 peer 1.1.1.1 as-number 100 peer 1.1.1.1 connect-interface LoopBack1 # ipv4-family vpnv4 policy vpn-target peer 1.1.1.1 enable peer 1.1.1.1 route-policy policy1 export #
What is "Route Matches ACL Rule" in a Route-policy
In route-policy, if the route is in the network segment range defined by the source address and its wildcard mask of the ACL rule, the route is considered to match the ACL rule.
For example, in the following configurations, the routes 10.1.1.0/24, 10.1.1.0/25, 10.1.1.0/30 is in the segment range of 10.1.1.0/24. Therefore, these routes are considered to match the ACL rule. The route 10.1.1.0/16 is considered to mismatch the ACL rule since it is outside of the segment range of 10.1.1.0/24.
acl number 2000 rule 1 permit source 10.1.1.0 0.0.0.255 rule 99 deny any
Examples for ACLs Applied to a Route-policy
Node Is Permit, Rule Is Permit.
Configuration example:
acl number 2000 rule 1 permit source 10.1.1.0 0.0.0.255 # route-policy policy1 permit node 10 if-match acl 2000 apply local-preference 1300 # route-policy policy1 permit node 20 # bgp 100 import-route static route-policy policy1 #
If there are two static routes, 10.1.1.0/24 and 10.1.2.0/24:
- The static route 10.1.1.0/24 matches the ACL in node 10 and the node 10 is permit, so the local-preference of 10.1.1.0/24 is modified to 1300.
- The static route 10.1.2.0/24 does not match node 10, but matches node 20. There is no rule in node20, so all attributes of 10.1.1.0/24 are not modified.
The result is, both the static routes are imported to BGP, and only the local-preference of 10.1.1.0/24 is modified.
Node Is Permit, Rule Is Permit.
Configuration example:
acl number 2000 rule 1 deny source 10.1.1.0 0.0.0.255 # route-policy policy1 permit node 10 if-match acl 2000 apply local-preference 1300 # route-policy policy1 permit node 20 # bgp 100 import-route static route-policy policy1 #
If there are two static routes, 10.1.1.0/24 and 10.1.2.0/24,
- 10.1.1.0/24 matches the deny rule in node 10, so 10.1.1.0/24 is denied, the apply clause in node 10 is not executed for 10.1.1.0/24, and the device continues to process node 20. As a result, 10.1.1.0/24 is imported to BGP and its local-preference is not changed.
- 10.1.2.0/24 does not match any rule in node 10, so the apply clause in node 10 is not executed, and the device continues to process node 20 for 10.1.2.0/24. As a result, 10.1.2.0/24 is imported to BGP.
The result is, both the static routes are imported to BGP, and the local-preferences of both routes are not modified.
Node Is Permit, Rule Is Permit.
Configuration example:
acl number 2000 rule 1 permit source 10.1.1.0 0.0.0.255 # route-policy policy1 deny node 10 if-match acl 2000 apply local-preference 1300 # route-policy policy1 permit node 20 # bgp 100 import-route static route-policy policy1 #
If there are two static routes, 10.1.1.0/24 and 10.1.2.0/24,
- 10.1.1.0/24 matches the permit rule in node 10 and the node 10 is deny, so 10.1.1.0/24 is denied, the apply clause in node 10 is not executed for 10.1.1.0/24, and the device stops to process node 20. As a result, 10.1.1.0/24 is not imported to BGP and its local-preference is not modified.
- 10.1.2.0/24 does not match node 10, so the apply clause in node 10 is not executed for 10.1.2.0/24, and the device continues to process node 20 for 10.1.2.0/24. As a result, 10.1.2.0/24 is imported to BGP.
The result is, only 10.1.2.0/24 is imported to BGP and its local-preference is not modified.
Node Is Permit, Rule Is Permit.4
Configuration example:
acl number 2000 rule 1 deny source 10.1.1.0 0.0.0.255 # route-policy policy1 deny node 10 if-match acl 2000 apply local-preference 1300 # route-policy policy1 permit node 20 # bgp 100 import-route static route-policy policy1 #
If there are two static routes, 10.1.1.0/24 and 10.1.2.0/24,
- 10.1.1.0/24 matches the deny rule in node 10, so 10.1.1.0/24 is denied, the apply clause in node 10 is not executed for 10.1.1.0/24, and the device continues to process node 20. As a result, 10.1.1.0/24 is imported to BGP and its local-preference is not modified.
- 10.1.2.0/24 does not match node 10, so the apply clause in node 10 is not executed for 10.1.2.0/24, and the device continues to process node 20 for 10.1.2.0/24. As a result, 10.1.2.0/24 is imported to BGP.
The result is, both the static routes are imported to BGP, and the local-preferences of both routes are not modified.