Example for Establishing an IPsec Tunnel Based on Certificates Obtained Through CMP
This section provides an example for establishing an IPsec tunnel based on certificates obtained through CMP.
Networking Requirements
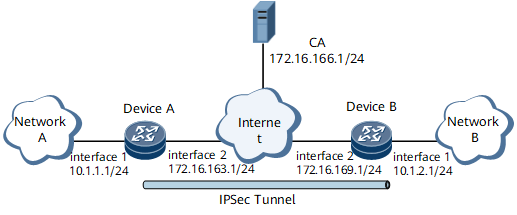
As shown in Figure1 Establishing an IPsec tunnel based on certificates obtained through CMP, network A is connected to the Internet through DeviceA, and network B is connected to the Internet through DeviceB. The network environment is as follows:
Network A belongs to subnet 10.1.1.0/24 and is connected to DeviceA through GigabitEthernet 0/1/1.
Network B belongs to subnet 10.1.2.0/24 and is connected to DeviceB through GigabitEthernet 0/1/1.
DeviceA and DeviceB are routable to each other.
To establish an IPsec tunnel in the IKE automatic negotiation mode to protect data traffic transmitted between networks A and B, perform the following operations:
Configure DeviceA and DeviceB to use CMP to obtain certificates and authenticate each other's identity.
Use the tunnel encapsulation mode.
Use ESP as the security protocol.
Set the encryption algorithm to AES for ESP.
Set the authentication algorithm to SHA2-256 for ESP.
Set the integrity algorithm to HMAC-SHA2-256.
Configuration Roadmap
The configuration roadmap is as follows:
Configure IP addresses for interfaces.
Create and configure a tunnel interface.
Configure a route (usually a static route) to the Internet on DeviceA and DeviceB.
Create ACL rules to define the data flow to be protected.
Configure certificate (obtained using CMP) authentication and use a default certificate attribute-based access control policy.
Create key pairs.
Configure entity information.
Configure CMP sessions.
Configure CMP-based certificate application.
Configure a CRL.
Use IPsec policies to establish an IPsec tunnel.
Data Preparation
To complete the configuration, you need the following data:
- IP addresses of interfaces
- ACL rules
- Entity information, PKI domain name, RSA key pairs, CA name, and certificate for device identity authentication and URL of a CMP server in a CMP request
- Security protocol, encryption algorithm, and authentication algorithm in an IPsec proposal and authentication algorithm in an IKE proposal
Procedure
- Configure DeviceA.
# Configure an IP address for GigabitEthernet 0/1/1.
<DeviceA> system-view [~DeviceA] interface GigabitEthernet 0/1/1 [~DeviceA-GigabitEthernet0/1/1] ip address 10.1.1.1 24 [*DeviceA-GigabitEthernet0/1/1] quit [*DeviceA] commit
# Configure an IP address for GigabitEthernet 0/1/2.
[~DeviceA] interface GigabitEthernet 0/1/2 [~DeviceA-GigabitEthernet0/1/2] ip address 172.16.163.1 24 [*DeviceA-GigabitEthernet0/1/2] quit [*DeviceA] commit
# Create and configure a tunnel interface.
[~DeviceA] interface Tunnel 10 [*DeviceA-Tunnel10] tunnel-protocol ipsec [*DeviceA-Tunnel10] ip address 172.19.1.1 24 [*DeviceA-Tunnel10] quit [*DeviceA] commit
# Configure two static routes to network B. One route uses Tunnel1 as the outbound interface and 172.20.1.2 as the next-hop address. The other route uses 172.16.163.2/24 as the next-hop address.
[~DeviceA] ip route-static 10.1.2.0 255.255.255.0 Tunnel 10 172.20.1.2 [*DeviceA] ip route-static 172.20.1.2 255.255.255.255 172.16.163.2 [*DeviceA] commit
# Create advanced ACL 3000 and configure a rule with source address 10.1.1.0/24 and destination address 10.1.2.0/24 for the ACL to match packets that need to be encrypted.
[~DeviceA] acl 3000 [*DeviceA-acl-adv-3000] rule permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255 [*DeviceA-acl-adv-3000] quit [*DeviceA] commit
# Create an RSA key pair.
[~DeviceA] rsa pki local-key-pair key-a create [*DeviceA] commit
# Configure entity information.
[~DeviceA] pki entity entitya [*DeviceA-pki-entitya] common-name DeviceA [*DeviceA-pki-entitya] quit [*DeviceA] commit
# Configure a CMP session.
[~DeviceA] pki domain domaina [*DeviceA-pki-domaina] pki cmp session session-a [*DeviceA-pki-domaina-pki-cmp-session-a] cmp request entity entitya [*DeviceA-pki-domaina-pki-cmp-session-a] cmp request rsa local-key-pair key-a regenerate [*DeviceA-pki-domaina-pki-cmp-session-a] cmp request ca-name "/C=cn/ST=beijing/L=shangdi/O=BB/OU=BB/CN=AB" [*DeviceA-pki-domaina-pki-cmp-session-a] cmp request server url http://172.16.73.168:8080 [*DeviceA-pki-domaina-pki-cmp-session-a] cmp request authentication-cert cert-a.cer [*DeviceA-pki-domaina-pki-cmp-session-a] quit [*DeviceA-pki-domaina] pki cmp initial-request [*DeviceA-pki-domaina] quit [*DeviceA] commit
# Import local certificate session-a_ir.cer and CA certificate session-a_ca0.cer.
[~DeviceA] pki import-certificate local filename session-a_ir.cer [~DeviceA] pki import-certificate ca filename session-a_ca0.cer
# Specify the local certificate in the CMP request for device identity authentication.
[~DeviceA] pki domain domaina [*DeviceA-pki-domaina] pki cmp session session-a [*DeviceA-pki-domaina-pki-cmp-session-a] cmp request authentication-cert session-a_ir.cer
# Configure automatic certificate update.
[~DeviceA-pki-domaina-pki-cmp-session-a] certificate auto-update enable [~DeviceA-pki-domaina-pki-cmp-session-a] quit [~DeviceA-pki-domaina] quit [*DeviceA] commit
# Enable CRL check.
[~DeviceA] pki crl check enable [*DeviceA] commit
# Configure automatic CRL update.
[~DeviceA] pki domain domaina [*DeviceA-pki-domaina] crl auto-update enable [*DeviceA-pki-domaina] crl update-period 3 [*DeviceA-pki-domaina] crl http [*DeviceA-pki-domaina] crl url http://172.18.166.1/crl.crl [*DeviceA-pki-domaina] quit [*DeviceA] commit
# Configure IPsec proposal tran1.
[~DeviceA] ipsec proposal tran1 [*DeviceA-ipsec-proposal-tran1] encapsulation-mode tunnel [*DeviceA-ipsec-proposal-tran1] transform esp [*DeviceA-ipsec-proposal-tran1] esp authentication-algorithm sha2-256 [*DeviceA-ipsec-proposal-tran1] esp encryption-algorithm aes 256 [*DeviceA-ipsec-proposal-tran1] quit [*DeviceA] commit
# Configure an IKE proposal.
[~DeviceA] ike proposal 10 [*DeviceA-ike-proposal-10] authentication-method rsa-sig [*DeviceA-ike-proposal-10] authentication-algorithm sha2-256 [*DeviceA-ike-proposal-10] integrity-algorithm hmac-sha2-256 [*DeviceA-ike-proposal-10] dh group14 [*DeviceA-ike-proposal-10] quit [*DeviceA] commit
# Configure an IKE peer.
[~DeviceA] ike peer b [*DeviceA-ike-peer-b] ike-proposal 10 [*DeviceA-ike-peer-b] certificate local-filename session-a_ir.cer [*DeviceA-ike-peer-b] remote-address 172.20.1.2 [*DeviceA-ike-peer-b] quit [*DeviceA] commit
# Configure IPsec policy map1.
[~DeviceA] ipsec policy map1 10 isakmp [*DeviceA-ipsec-policy-isakmp-map1-10] security acl 3000 [*DeviceA-ipsec-policy-isakmp-map1-10] proposal tran1 [*DeviceA-ipsec-policy-isakmp-map1-10] ike-peer b [*DeviceA-ipsec-policy-isakmp-map1-10] quit [*DeviceA] commit
# Apply IPsec policy map1 to the tunnel interface.
[~DeviceA] interface Tunnel 10 [*DeviceA-Tunnel10] ipsec policy map1 [*DeviceA-Tunnel10] quit [*DeviceA] commit
- Configure DeviceB.
# Configure an IP address for GigabitEthernet 0/1/1.
<DeviceB> system-view [~DeviceB] interface GigabitEthernet 0/1/1 [~DeviceB-GigabitEthernet0/1/1] ip address 10.1.2.1 24 [*DeviceB-GigabitEthernet0/1/1] quit [*DeviceB] commit
# Configure an IP address for GigabitEthernet 0/1/2.
[~DeviceB] interface GigabitEthernet 0/1/2 [~DeviceB-GigabitEthernet0/1/2] ip address 172.16.169.1 24 [*DeviceB-GigabitEthernet0/1/2] quit [*DeviceB] commit
# Create and configure a tunnel interface.
[~DeviceB] interface Tunnel 10 [*DeviceB-Tunnel10] tunnel-protocol ipsec [*DeviceB-Tunnel10] ip address 172.20.1.2 24 [*DeviceB-Tunnel10] quit [*DeviceB] commit
# Configure two static routes to network A. One route uses Tunnel1 as the outbound interface and 172.19.1.1 as the next-hop address. The other route uses 172.16.169.2/24 as the next-hop address.
[~DeviceB] ip route-static 10.1.1.0 255.255.255.0 Tunnel 10 172.19.1.1 [*DeviceB] ip route-static 172.19.1.1 255.255.255.255 172.16.169.2 [*DeviceB] commit
# Create advanced ACL 3000 and configure a rule with source address 10.1.2.0/24 and destination address 10.1.1.0/24 for the ACL to match packets that need to be encrypted.
[~DeviceB] acl 3000 [*DeviceB-acl-adv-3000] rule permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255 [*DeviceB-acl-adv-3000] quit [*DeviceB] commit
# Create an RSA key pair.
[~DeviceB] rsa pki local-key-pair key-b create [*DeviceB] commit
# Configure entity information.
[~DeviceB] pki entity entityb [*DeviceB-pki-entityb] common-name DeviceB [*DeviceB-pki-entityb] quit [*DeviceB] commit
# Configure a CMP session.
[~DeviceB] pki domain domainb [*DeviceB-pki-domainb] pki cmp session session-b [*DeviceB-pki-domainb-pki-cmp-session-b] cmp request entity entityb [*DeviceB-pki-domainb-pki-cmp-session-b] cmp request rsa local-key-pair key-b regenerate [*DeviceB-pki-domainb-pki-cmp-session-b] cmp request ca-name "/C=cn/ST=beijing/L=shangdi/O=BB/OU=BB/CN=AB" [*DeviceB-pki-domainb-pki-cmp-session-b] cmp request server url http://172.16.73.168:8080 [*DeviceB-pki-domainb-pki-cmp-session-b] cmp request authentication-cert cert-b.cer [*DeviceB-pki-domainb-pki-cmp-session-b] quit [*DeviceB-pki-domainb] pki cmp initial-request [*DeviceB-pki-domainb] quit [*DeviceB] commit
# Import local certificate session-b_ir.cer and CA certificate session-b_ca0.cer.
[~DeviceB] pki import-certificate local filename session-b_ir.cer [~DeviceB] pki import-certificate ca filename session-b_ca0.cer
# Specify the local certificate in the CMP request for device identity authentication.
[~DeviceB] pki domain domainb [*DeviceB-pki-domainb] pki cmp session session-b [*DeviceB-pki-domainb-pki-cmp-session-b] cmp request authentication-cert session-b_ir.cer
# Configure automatic certificate update.
[~DeviceB-pki-domainb-pki-cmp-session-b] certificate auto-update enable [~DeviceB-pki-domainb-pki-cmp-session-b] quit [*DeviceB-pki-domainb] quit [*DeviceB] commit
# Enable CRL check.
[~DeviceB] pki crl check enable [*DeviceB] commit
# Configure automatic CRL update.
[~DeviceB] pki domain domainb [*DeviceB-pki-domainb] crl auto-update enable [*DeviceB-pki-domainb] crl update-period 3 [*DeviceB-pki-domainb] crl http [*DeviceB-pki-domainb] crl url http://172.18.166.1/crl.crl [*DeviceB-pki-domainb] quit [*DeviceB] commit
# Configure IPsec proposal tran1.
[~DeviceB] ipsec proposal tran1 [*DeviceB-ipsec-proposal-tran1] encapsulation-mode tunnel [*DeviceB-ipsec-proposal-tran1] transform esp [*DeviceB-ipsec-proposal-tran1] esp authentication-algorithm sha2-256 [*DeviceB-ipsec-proposal-tran1] esp encryption-algorithm aes 256 [*DeviceB-ipsec-proposal-tran1] quit [*DeviceB] commit
# Configure an IKE proposal.
[~DeviceB] ike proposal 10 [*DeviceB-ike-proposal-10] authentication-method rsa-sig [*DeviceB-ike-proposal-10] authentication-algorithm sha2-256 [*DeviceB-ike-proposal-10] integrity-algorithm hmac-sha2-256 [*DeviceB-ike-proposal-10] dh group14 [*DeviceB-ike-proposal-10] quit [*DeviceB] commit
# Configure an IKE peer.
[~DeviceB] ike peer a [*DeviceB-ike-peer-a] ike-proposal 10 [*DeviceB-ike-peer-a] certificate local-filename session-b_ir.cer [*DeviceB-ike-peer-a] remote-address 172.19.1.1 [*DeviceB-ike-peer-a] quit [*DeviceB] commit
# Configure IPsec policy map1.
[~DeviceB] ipsec policy map1 10 isakmp [*DeviceB-ipsec-policy-isakmp-map1-10] security acl 3000 [*DeviceB-ipsec-policy-isakmp-map1-10] proposal tran1 [*DeviceB-ipsec-policy-isakmp-map1-10] ike-peer a [*DeviceB-ipsec-policy-isakmp-map1-10] quit [*DeviceB] commit
# Apply IPsec policy map1 to the tunnel interface.
[~DeviceB] interface Tunnel10 [*DeviceB-Tunnel10] ipsec policy map1 [*DeviceB-Tunnel10] quit [*DeviceB] commit
Configuration Files
DeviceA configuration file.
# sysname DeviceA # acl number 3000 rule 5 permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255 # ike proposal 10 authentication-method rsa-sig encryption-algorithm aes-cbc 256 dh group14 authentication-algorithm sha2-256 integrity-algorithm hmac-sha2-256 # ike peer b ike-proposal 10 certificate local-filename session-a_ir.cer remote-address 172.20.1.2 # ipsec proposal tran1 esp authentication-algorithm sha2-256 esp encryption-algorithm aes 256 # ipsec policy map1 10 isakmp security acl 3000 ike-peer b proposal tran1 # interface GigabitEthernet0/1/1 ip address 10.1.1.1 255.255.255.0 # interface GigabitEthernet0/1/2 ip address 172.16.163.1 255.255.255.0 # interface Tunnel10 ip address 172.19.1.1 255.255.255.0 tunnel-protocol ipsec ipsec policy map1 # ip route-static 10.1.2.0 255.255.255.0 Tunnel 10 172.20.1.2 ip route-static 172.20.1.2 255.255.255.255 172.16.163.2 # pki entity entitya common-name DeviceA # pki domain domaina crl auto-update enable crl update-period 3 crl http crl url http://172.18.166.1/crl.crl pki cmp session session-a cmp request entity entitya cmp request rsa local-key-pair key-a regenerate cmp request ca-name "/C=cn/ST=beijing/L=shangdi/O=BB/OU=BB/CN=AB" cmp request server url http://172.16.73.168:8080 cmp request authentication-cert session-a_ir.cer certificate auto-update enable certificate request entity entitya # return
- DeviceB configuration file.
# sysname DeviceB # acl number 3000 rule 5 permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255 # ike proposal 10 authentication-method rsa-sig encryption-algorithm aes-cbc 256 dh group14 authentication-algorithm sha2-256 integrity-algorithm hmac-sha2-256 # ike peer a certificate local-filename session-b_ir.cer ike-proposal 10 remote-address 172.19.1.1 # ipsec proposal tran1 transform esp esp authentication-algorithm sha2-256 # ipsec policy map1 10 isakmp security acl 3000 ike-peer a proposal tran1 # interface GigabitEthernet0/1/1 ip address 10.1.2.1 255.255.255.0 # interface GigabitEthernet0/1/2 ip address 172.16.169.1 255.255.255.0 # interface Tunnel10 ip address 172.20.1.2 255.255.255.0 tunnel-protocol ipsec ipsec policy map1 # ip route-static 10.1.1.0 255.255.255.0 Tunnel 10 172.19.1.1 ip route-static 172.19.1.1 255.255.255.255 172.16.169.2 # pki entity entityb common-name DeviceB # pki domain domainb crl auto-update enable crl update-period 3 crl http crl url http://172.18.166.1/crl.crl pki cmp session session-b cmp request entity entityb cmp request rsa local-key-pair key-b regenerate cmp request ca-name "/C=cn/ST=beijing/L=shangdi/O=BB/OU=BB/CN=AB" cmp request server url http://172.16.73.168:8080 cmp request authentication-cert session-b_ir.cer certificate auto-update enable certificate request entity entityb # return