Example for Configuring IPsec NAT Traversal
Networking Requirements
When a NAT gateway exists between the local and remote devices used for IPsec negotiation, NAT traversal capabilities need to be negotiated between the local and remote ends of the IPsec tunnel. Therefore, the local and remote devices must be able to support NAT traversal.
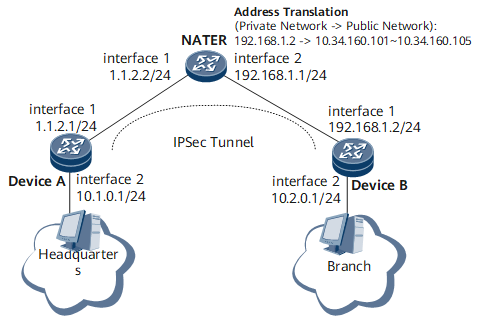
On the network shown in Figure 1, the headquarters egress gateway Device A and the branch egress gateway Device B translate addresses using the NATER, and they establish an IPsec tunnel that supports NAT traversal.
Precautions
- Configure the NATER, to ensure the communication between DeviceA and DeviceB.
- Device A, the responder of IPsec negotiation, must use a security policy template.
- Both Device A and Device B must be enabled with NAT traversal.
- The encapsulation mode can be set to tunnel only.
- IKE negotiation in main mode does not support IPsec NAT traversal.
Configure DPD.
Procedure
- Configure Device A.
# sysname DeviceA //Configure the host name of the device. # service-location 1 location slot 1 # service-instance-group group1 service-location 1 # ike dpd interval 10 10 //You are suggested to deploy the DPD function. # acl number 3000 //Configure an ACL. rule 0 permit ip source 10.1.0.0 0.0.0.255 destination 10.2.0.0 0.0.0.255 # ipsec proposal rta //Configure an IPsec proposal. esp authentication-algorithm sha2-256 esp encryption-algorithm aes 256 # ike proposal 1 //Configure an IKE proposal. dh group14 # ike peer rta //Configure an IKE peer. ike-proposal 1 pre-shared-key cipher %^%#JvZxR2g8c;a9~FPN~n'$7`DEV&=G(=Et02P/%\*!%^%# //Configure the PSK as huawei in ciphertext. local-id-type ip //Configure the IKE ID in the IP format. nat traversal //Configure NAT traversal. # ipsec policy-template rta_temp 1 //Configure the firt IPsec policy template. ike-peer rta proposal rta security acl 3000 # ipsec policy rta 1 isakmp template rta_temp //Configure an SA for the IPsec policy template. # interface Tunnel1 ip address 1.1.1.1 24 tunnel-protocol ipsec ipsec policy rta service-instance-group 1 # interface gigabitethernet0/1/1 ip address 1.1.2.1 255.255.255.0 # interface gigabitethernet0/1/2 ip address 10.1.0.1 255.255.255.0 # ospf 1 area 0.0.0.0 network 1.1.2.0 0.0.0.255 # ip route-static 192.168.0.0 255.255.0.0 Tunnel1 192.168.0.2 //Configure a static route destined to the network segment 192.168.0.0. ip route-static 192.168.0.2 255.255.255.255 1.1.2.2 //Configure the static route destined to DeviceB Tunnel interface. # return
- Configure Device B.
# sysname DeviceB //Configure a host name for the device. # service-location 1 location slot 1 # service-instance-group group1 service-location 1 # ike dpd interval 10 10 //You are suggested to deploy the DPD function. # acl number 3000 //Configure an ACL. rule 0 permit ip source 10.2.0.0 0.0.0.255 destination 10.1.0.0 0.0.0.255 # ipsec proposal rtb //Configure an IPsec proposal. esp authentication-algorithm sha2-256 esp encryption-algorithm aes 256 # ike proposal 1 //Configure an IKE proposal. dh group14 # ike peer rtb //Configure an IKE peer. ike-proposal 1 pre-shared-key cipher %^%#JvZxR2g8c;a9~FPN~n'$7`DEV&=G(=Et02P/%\*!%^%# //Configure the PSK as huawei in ciphertext. local-id-type ip //Configure the IKE ID in the IP format. remote-address 1.1.1.1 //Configure the IP address of the IKE peer. nat traversal //Configure NAT traversal. # ipsec policy rtb 1 isakmp //Configure an IPsec policy. security acl 3000 ike-peer rtb proposal rtb # interface Tunnel1 ip address 192.168.0.2 24 tunnel-protocol ipsec ipsec policy rtb service-instance-group 1 # interface gigabitethernet0/1/1 ip address 192.168.1.2 255.255.255.0 # interface gigabitethernet0/1/2 ip address 10.2.0.1 255.255.255.0 # ospf 1 area 0.0.0.0 network 192.168.1.0 0.0.0.255 # ip route-static 10.1.0.0 255.255.255.0 Tunnel1 1.1.1.1 //Configure a static route destined to the network segment 10.1.0.0. ip route-static 1.1.1.1 255.255.255.255 192.168.1.1 //Configure the static route destined to DeviceA Tunnel interface. # return
- Configure NATER.
# sysname NATER //Configure the host name of the device. # service-location 1 location slot 1 # service-instance-group group1 service-location 1 # nat instance nat1 id 1 service-instance-group 1 nat address-group address-group1 group-id 1 10.34.160.101 10.34.160.105 # acl number 3000 //Configure ACL 3000. rule 0 permit ip source 192.168.0.0 0.0.0.255 destination 1.1.1.0 0.0.0.255 # interface gigabitethernet0/1/1 ip address 1.1.2.2 255.255.255.0 nat bind acl 3000 instance nat1 //Configure NAT outbound on the interface. # interface gigabitethernet0/1/2 ip address 192.168.1.1 255.255.255.0 # ospf 1 import-route unr area 0.0.0.0 network 1.1.2.0 0.0.0.255 network 192.168.1.0 0.0.0.255 # ip route-static 1.1.1.1 32 1.1.2.1 //Configure the static route destined to DeviceA Tunnel interface. ip route-static 192.168.0.2 32 192.168.1.2 //Configure the static route destined to DeviceB Tunnel interface. # return
- Verify the configuration.
After an IPsec session is established upon the ping operation, run the display ike sa verbose remote ip-address and display ipsec sa commands on Device A. The command output displays configurations of the IPsec tunnel.