Configuring NS Multicast Suppression on an EVPN MPLS
When a user accesses an EVPN MPLS through a BD, NS multicast suppression can be configured to reduce or suppress excess NS messages.
Usage Scenario
When a user is connected to an EVPN MPLS network through a BD, IPv6 host neighbors are discovered in NS multicast mode. When a device receives an NS message for IPv6 address resolution, the device forwards the NS message in multicast mode in its BD. If a large number of NS messages are received within a specified period, forwarding all these NS messages on the EVPN occupies excessive network resources, which affects service running.
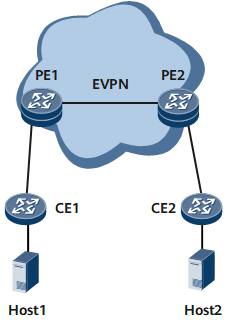
As shown in Figure 1, with NS multicast suppression configured on a PE, upon receipt of an NS message, the PE checks whether the request message contains information about the end user. If such information is contained in the request message, the PE simply implements proxy ND or converts multicast streams to unicast streams, thereby reducing or suppressing NS message flooding.
In addition, NS multicast suppression can prevent against ND spoofing attacks. An ND spoofing attack means that an attacker associates its MAC address with the IPv6 address of a host so that any traffic destined for the IPv6 address can be sent to the attacker. With NS multicast suppression enabled, if such an attack is launched, the proxy ND table conflict detection mechanism triggers an IPv6 address conflict alarm, reminding users of the potential ND spoofing attack.
Procedure
- Enable NS multicast suppression.
Run system-view
The system view is displayed.
Run bridge-domain bd-id
The BD view is displayed.
Run ipv6 nd multicast-suppress { proxy-reply [ unknown-options-unicast ] | unicast-forward } [ mismatch-discard ] enable
NS multicast suppression is enabled.
(Optional) Run ipv6 nd multicast-suppress { host | router }
The R flag carried in NA messages for proxy ND is configured.
(Optional) Run ipv6 nd multicast-suppress dynamic limit limit-value
The maximum number of dynamic proxy ND entries that can be learned in a BD is configured.
(Optional) Run ipv6 nd multicast-suppress dynamic expire-time expire-time-value
The aging time of dynamic proxy ND entries is configured.
Run commit
The configuration is committed.
Run quit
The BD view is exited.
- Enable the function to flood ND entries or proxy ND entries through EVPN routes.
Perform the following operations on a Layer 2 device:
Run bridge-domain bd-id
The BD view is displayed.
Run ipv6 nd collect host enable
The device has been enabled to flood proxy ND entries through EVPN routes.
Run commit
The configuration is committed.
Run quit
The BD view is exited.
Perform the following operations on a Layer 3 device:
Run interface vbdif bd-id
A VBDIF interface is created, and the VBDIF interface view is displayed.
Run ipv6 enable
IPv6 is enabled on the interface.
Run ipv6 nd collect host enable
The device has been enabled to flood ND entries through EVPN routes.
Run commit
The configuration is committed.
Run quit
The VBDIF interface view is exited.
- Configure BGP EVPN to advertise routes.
-
The BGP-EVPN address family view or BGP multi-instance EVPN address family view is displayed.
Run peer { ipv4-address | group-name } advertise nd
The device is configured to advertise ND routes to the BGP EVPN peer.
Run commit
The configuration is committed.
Run quit
The BGP-EVPN address family view or BGP multi-instance EVPN address family view is exited.
Run quit
The BGP view or BGP multi-instance view is exited.
-
- (Optional) Configure performance limit for ND message processing.
Run ipv6 nd { rs | ra | ns | na } anti-attack rate-limit limit-number
The rate at which ND messages are sent is configured. That is, the number of ND messages allowed to be processed per second is configured.
Run ipv6 nd miss anti-attack rate-limit limit-number
The rate at which ND Miss messages are sent is configured. That is, the number of ND Miss messages allowed to be processed per second is configured.
Run commit
The configuration is committed.
Verifying the Configuration
Run the display ipv6 nd multicast-suppress bridge-domain bd-id [ verbose ] command to view information about the proxy ND table in a specified BD. If the bd-id parameter is not specified, information about proxy ND tables in all BDs is displayed.
Run the display ipv6 nd packet statistics bridge-domain [ bd-id ] command to view ND message statistics in a specified BD. If the bd-id parameter is not specified, statistics about ND messages in all BDs are displayed.

In the user view, run the reset ipv6 nd multicast-suppress dynamic bridge-domain [ bd-id ] command to clear dynamic proxy ND entries in a specified BD. If the bd-id parameter is not specified, dynamic ND proxy entries in all BDs are cleared.
In the user view, run the reset ipv6 nd packet statistics bridge-domain [ bd-id ] command to clear ND message statistics in a specified BD. If the bd-id parameter is not specified, ND message statistics in all BDs are displayed.