Configuring Static BGP VPN Flow Specification
In VPNs, BGP VPN Flow Specification routes are generated manually to control traffic in static BGP VPN Flow Specification.
Usage Scenario
When deploying static BGP VPN Flow Specification, a BGP VPN Flow Specification route needs to be generated manually, and a BGP VPN Flow Specification peer relationship needs to be established between the device that generates the BGP VPN Flow Specification route and each ingress in the network to transmit BGP VPN Flow Specification routes.
In an AS with multiple ingresses, a BGP VPN Flow route reflector (Flow RR) can be deployed to reduce the number of BGP VPN Flow Specification peer relationships and save network resources.
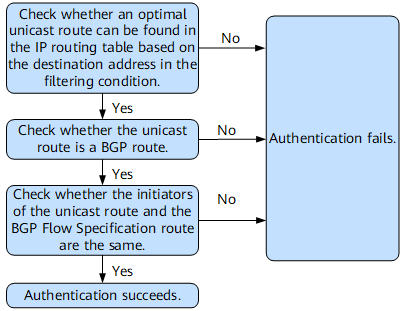
If you want to filter traffic based on the address prefix but the BGP VPN Flow Specification route carrying the filtering rule cannot be authenticated, disable the authentication of BGP VPN Flow Specification routes received from a specified peer.
Pre-configuration Tasks
Before configuring static BGP VPN Flow Specification, configure a VPN instance and bind interfaces to a VPN instance.
Procedure
- Generate a BGP VPN Flow Specification route manually.
- Establish a BGP VPN Flow Specification peer relationship.
- (Optional) Configure a Flow RR.
Before configuring a Flow RR, establish a BGP VPN Flow Specification peer relationship between the Flow RR and device on which the BGP VPN Flow Specification route is generated and between the Flow RR and every network ingress.
- (Optional) Add the AS_Path attribute as a check item to BGP VPN Flow Specification route verification rules.
- (Optional) Disable BGP VPN Flow Specification route authentication.
- (Optional) Disable the device from validating the routes that carry a redirection extended community attribute and are received from a specified EBGP peer.
- (Optional) Set the redirection next-hop attribute ID for BGP VPN Flow Specification routes.
The redirection next-hop attribute ID can be 0x010C (ID defined in a relevant RFC) or 0x0800 (ID defined in a relevant draft). If a Huawei device needs to communicate with a non-Huawei device that does not support the redirection next-hop attribute ID of 0x010C or 0x0800, set the redirection next-hop attribute ID of BGP VPN Flow Specification routes as required.
Set the redirection next-hop attribute ID to 0x010C (ID defined in a relevant RFC) for BGP VPN Flow Specification routes.
Run system-view
The system view is displayed.
Run bgp as-number
The BGP view is displayed.
Run ipv4-flow vpn-instance vpn-instance-name
The BGP-Flow VPN instance IPv4 address family view is displayed.
Run peer ipv4-address redirect ip rfc-compatible
The redirection next-hop attribute ID is set to 0x010C (ID defined in a relevant RFC) for BGP VPN Flow Specification routes.
Run commit
The configuration is committed.
Set the redirection next-hop attribute ID to 0x0800 (ID defined in a relevant draft) for BGP VPN Flow Specification routes.
Run system-view
The system view is displayed.
Run bgp as-number
The BGP view is displayed.
Run ipv4-flow vpn-instance vpn-instance-name
The BGP-Flow VPN instance IPv4 address family view is displayed.
Run peer ipv4-address redirect ip draft-compatible
The redirection next-hop attribute ID is set to 0x0800 (ID defined in a relevant draft) for BGP VPN Flow Specification routes.
Run commit
The configuration is committed.
- (Optional) Enable the CAR statistics and packet
loss statistics function for BGP Flow Specification.
- (Optional) Disable BGP Flow Specification on the interface.
- (Optional) Disable BGP FlowSpec protection.
- (Optional) Enable BGP Flow Specification IPv4 fragmentation rules to comply with RFC 5575.
Verifying the Configuration
After configuring static BGP VPN Flow Specification, verify the configuration.
Run the display bgp flow vpnv4 vpn-instance vpn-instance-name peer [ [ ipv4-address ] verbose ] command to check information about BGP VPN Flow Specification peers.
Run the display bgp flow vpnv4 vpn-instance vpn-instance-name routing-table command to check information about BGP VPN Flow Specification routes.
Run the display bgp flow vpnv4 vpn-instance vpn-instance-name routing-table [ peer ipv4-address { advertised-routes | received-routes [ active ] } ] statistics command to check statistics about BGP VPN Flow Specification routes.
- Run the display flowspec rule reindex-value slot slot-id command to check information about combined rules in the BGP FlowSpec local rule table.
- Run the display flowspec rule statistics slot slot-id command to check statistics about the rules for BGP FlowSpe routes to take effect.