Example for Configuring VXLAN over IPsec
VXLAN packets are unencrypted and vulnerable if being simply transmitted on networks. You can configure VXLAN over IPsec to ensure secure transmission of VXLAN packets.
Networking Requirements
Figure 1 shows the networking diagram.
Figure 1 VXLAN over IPsec networking
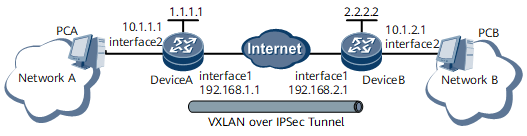

Interfaces 1 and 2 in this example represent GE 0/1/1 and GE 0/1/2, respectively.

Network A belongs to subnetwork 10.1.1.0/24 and is connected to Device A through GE 0/1/2.
Network B belongs to subnetwork 10.1.2.0/24 and is connected to Device B through GE 0/1/2.
Device A and Device B are routable.
The network must meet the following requirements:
VMs in different data centers can communicate with each other.
Data transmitted between PCA and PCB is encrypted.
Configuration Roadmap
The configuration roadmap is as follows:
- Configure a VXLAN IP address.
- Configure a VXLAN service access point.
- Configure a VXLAN tunnel.
- Configure an ACL rule.
- Configure an IKE proposal.
- Configure an IPsec proposal.
- Configure an IKE peer.
- Configure an IPsec policy.
- Configure an IPsec service instance group.
- Create and configure an IPsec tunnel.
- Configure a static route that imports traffic into the tunnel.
Data Preparation
To complete the configuration, you need the following data:
- IP addresses of the interfaces
- VLAN ID and VXLAN gateway address of the VM
- The tunnel mode, IP address, source address, and destination address of the tunnel interface
- IP address segment of each network
- Pre-shared key
- Security protocols, encryption algorithms, and authentication algorithms used in the IPsec proposal
- Encryption algorithm and authentication algorithm that an IKE proposal uses
Configuration Files
Device A configuration file
# sysname DeviceA # bridge-domain 10 vxlan vni 1 # acl number 3000 rule 5 permit ip source 3.3.3.3 0 destination 4.4.4.4 0 # service-location 1 location slot 1 # service-instance-group group1 service-location 1 # ike proposal 10 encryption-algorithm aes-cbc 256 dh group14 authentication-algorithm sha2-256 integrity-algorithm hmac-sha2-256 # ike peer b pre-shared-key %$%$THBGMJK2659z"C(T{J"-,.2n%$%$ ike-proposal 10 remote-address 2.2.2.2 # ipsec proposal tran1 esp authentication-algorithm sha2-256 esp encryption-algorithm aes 256 # ipsec policy map1 10 isakmp security acl 3000 ike-peer b proposal tran1 local-address 1.1.1.1 # interface GigabitEthernet0/1/1 undo shutdown ip address 192.168.1.1 255.255.0.0 # interface GigabitEthernet0/1/2 undo shutdown # interface GigabitEthernet0/1/2.1 mode l2 encapsulation dot1q vid 10 rewrite pop single bridge-domain 10 # interface loopback1 ip address 1.1.1.1 255.255.255.255 # interface loopback2 ip address 3.3.3.3 255.255.255.255 # interface Nve1 source 3.3.3.3 vni 1 head-end peer-list 4.4.4.4 # interface Tunnel1 ip address unnumbered interface loopback1 tunnel-protocol ipsec ipsec policy map1 service-instance-group group1 # ip route-static 2.2.2.2 255.255.255.255 GigabitEthernet0/1/1 192.168.2.1 ip route-static 4.4.4.4 255.255.255.255 Tunnel1 2.2.2.2 # return
- Device B configuration file
# sysname DeviceB # bridge-domain 10 vxlan vni 1 # acl number 3000 rule 5 permit ip # service-location 1 location slot 1 # service-instance-group group1 service-location 1 # ike proposal 10 encryption-algorithm aes-cbc 256 dh group14 authentication-algorithm sha2-256 integrity-algorithm hmac-sha2-256 # ike peer 1 pre-shared-key %$%$THBGMJK2659z"C(T{J"-,.2n%$%$ ike-proposal 1 remote-address 1.1.1.1 # ipsec proposal tran1 esp authentication-algorithm sha2-256 esp encryption-algorithm aes 256 # ipsec policy-template temp1 1 # security acl 3000 ike-peer 1 proposal tran1 local-address 2.2.2.2 # ipsec policy 1 1 isakmp template temp1 # interface GigabitEthernet0/1/1 undo shutdown ip address 192.168.2.1 255.255.0.0 # interface GigabitEthernet0/1/2 undo shutdown # interface GigabitEthernet0/1/2.1 mode l2 encapsulation dot1q vid 10 rewrite pop single bridge-domain 10 # interface loopback1 ip address 2.2.2.2 255.255.255.255 # interface loopback2 ip address 4.4.4.4 255.255.255.255 # interface Nve1 source 4.4.4.4 vni 1 head-end peer-list 3.3.3.3 # interface Tunnel1 ip address unnumbered interface loopback1 tunnel-protocol ipsec ipsec policy 1 service-instance-group group1 # ip route-static 1.1.1.1 255.255.255.255 GigabitEthernet0/1/1 192.168.1.1 # return