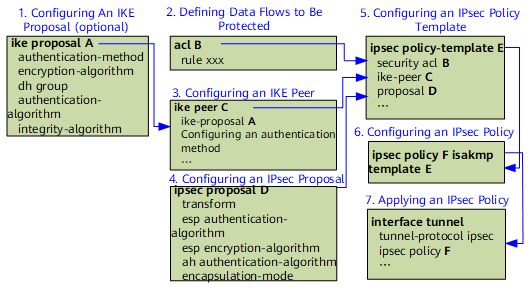
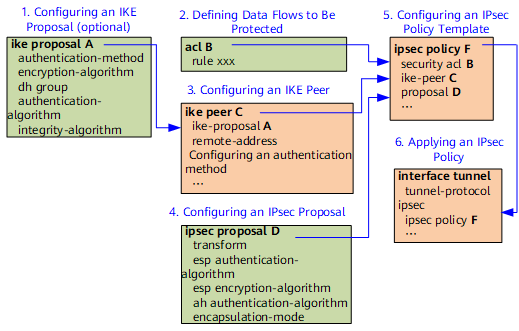
Configuration Workflow
This section describes the process of creating an IPsec SA through IKE negotiation and the command calling relationship.
IPsec policies or IPsec policy templates can be applied. You can configure an IPsec policy on both ends of an IPsec tunnel. You can also configure an IPsec policy on one end and an IPsec policy template on the other end. The IPsec policy template is mainly applicable to the scenario in which the peer IP address is not fixed.
Parameters that can be set in an IPsec policy template are the same as those that can be set in an IPsec policy. The parameters include the IPsec proposal, data flow to be protected, PFS feature, lifetime, and IKE peer. Note that the ACL, IPsec proposal, and IKE peer are mandatory. The other parameters are optional. If the IPsec policy template is used to match the policy during IKE negotiation, the configured parameters must match those in the policy template. The non-configured parameters can adopt values configured by the initiating party.