Configuring IPsec NAT Traversal
When an NAT device exists between IPsec peers, the NAT traversal function must be enabled on both ends.
Context
AH is mainly used to ensure the message integrity, including the IP packet headers. Because the IP packet headers are modified by NAT, the IP packet header verification by AH fails. Therefore, an IPsec tunnel protected by AH cannot traverse the NAT gateway. Packets encrypted by ESP do not encounter this problem because the integrity verification by ESP does not include IP packet headers (outer IP packet header in tunnel mode).
When the NAT gateway is configured to allocate indexes dynamically, the same private network IP address can be mapped by NAT to different addresses and port numbers after the IPsec SA is disconnected and reconnected. When the NAT gateway is configured to allocate indexes statically, a private network IP address is mapped by NAT to only one IP address and port number. Configuring the NAT gateway to allocate indexes statically is recommended.
Procedure
- Run system-view
The system view is displayed.
- Run ike peer peer-name
An IKE peer is created, and the IKE peer view is displayed.
- Run nat traversal
NAT traversal is enabled.
- Run remote-address [ authentication-address | vpn-instance vpn-instance-name ] remote-low-address [ remote-high-address ]
The peer IP address or address segment is configured.
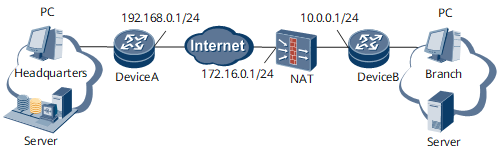
Configuration of device A:
If the HQ network does not need to initiate an access, you can configure the IPsec policy template for device A. The IKE peer defined in the IPsec policy template may not specify the peer IP address (that is, the remote-address command used to configure the translated IP address for device A and device B, is not configured).
If the HQ network needs to initiate an access, you must configure the IPsec policy in IKE mode for device A. The IKE peer defined in the IPsec policy must specify the peer IP address that is translated (running the remote-address 172.16.0.1 command).
If the local ID of device B is set to the IP address, you must run the remote-address authentication-address command to set the outbound interface address or address segment (IP address before NAT) of gateway B as the verification address (remote-address authentication-address 10.0.0.1) for device A.
Configuration of device B:
Configure the IPsec policy in IKE mode for device B. Specify the peer IP address (remote-address 192.168.0.1) on the IKE peer defined in the IPsec policy.
- Run quit
Return to the system view.
- Run ike sa nat-keepalive-timer interval seconds
The interval at which NAT update packets are sent by IKE is set.
A NAT session has a certain survival period on the NAT gateway. After a tunnel is established, if no packet traverses the gateway for a long period of time, the NAT session is deleted. As a result, data cannot be transmitted over the tunnel. A NAT-keepalive message can be sent to the peer party before the NAT session expires to maintain the NAT session and address the preceding issue.
- Run commit
The configuration is committed.
Follow-up Procedure
Run the display ike peer command to check the nat traversal field in the output and determine whether NAT traversal is enabled.