Example for Collecting IPv4 Original Flow Statistics
This section provides an example for configuring NetStream to collect statistics about abnormal IPv4 packets on the user side. The NetStream traffic statistics collection function helps rapidly analyze the type and location of abnormal traffic.
Networking Requirements
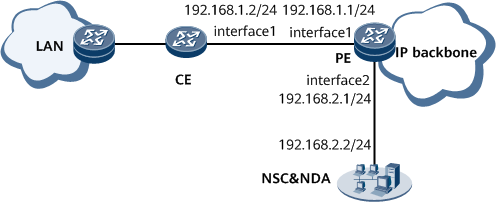
On the network shown in Figure 1, NetStream is configured to collect statistics about the source IP address, destination IP address, port, and protocol information of network packets on the user side. Such statistics help analyze users' behaviors and detect the virus-infected terminals, source and destination of Denial of service (DoS) and Distributed Denial of service (DDoS) attacks, source of spams, and unauthorized websites. In addition, NetStream allows users to rapidly identify virus types and locate the IP address of abnormal traffic. Based on other NetStream flow attributes, users can filter out virus-infected traffic and prevent it from spreading over the network.
Configuration Roadmap
The configuration roadmap is as follows:
Configure PEs and CEs to communicate.
Configure NetStream to collect statistics about incoming and outgoing flows on the user-side interface of the PE.
Data Preparation
To complete the configuration, you need the following data:
Name of the user-side interface of the PE
Output format of NetStream flows
Destination IP address, destination port number, and source IP address of NetStream flows to be output
ID of the slot where the NetStream service processing board resides (In this example, the NetStream service processing board is in slot 1.)
Procedure
- Configure PEs and CEs to communicate.
# Assign the IP address and mask to each interface according to Figure 1. For configuration details, see "Configuration Files" in this section.
- Enable the NetStream statistics collection function on GE 0/1/0 of the PE.
# Specify the distributed NetStream service processing mode on a board.
[*PE] slot 1 [*PE-slot-1] ip netstream sampler to slot self [*PE-slot-1] quit
# Enable the statistics collection for TCP flags in original flows.
[*PE] ip netstream tcp-flag enable# Specify the destination address, destination port number, and source address for NetStream flows output in V5 format.
[*PE] ip netstream export host 192.168.2.2 9001 [*PE] ip netstream export source 192.168.2.1
# Enable NetStream sampling and configure the fixed packet sampling mode.
[*PE] ip netstream sampler fix-packets 10000 inbound [*PE] ip netstream sampler fix-packets 10000 outbound [*PE] commit
# Configure NetStream to collect statistics about incoming and outgoing flows on GE 0/1/0 of the PE.
[*PE] interface GigabitEthernet 0/1/0 [*PE-GigabitEthernet0/1/0] undo shutdown [*PE-GigabitEthernet0/1/0] ip netstream inbound [*PE-GigabitEthernet0/1/0] ip netstream outbound [*PE-GigabitEthernet0/1/0] quit [*PE] commit

NetStream enabled on a main interface cannot collect traffic statistics about its sub-interface.
- Verify the configuration.
# After the configuration is complete, run the display ip netstream cache origin slot 1 command. The command output shows information about various original flows in the NetStream flow buffer.
[~PE] display ip netstream cache origin slot 1 DstIf SrcIf DstP Msk Pro Tos SrcP Msk Flags Ttl Packets Bytes NextHop Direction DstIP DstAs SrcIP SrcAs BGP: BGP NextHop TopLabelType Label1 Exp1 Bottom1 Label2 Exp2 Bottom2 Label3 Exp3 Bottom3 TopLabelIpAddress VlanId VniId CreateFlowTime LastRefreshTime VPN FlowLabel Rdvalue -------------------------------------------------------------------------- GigabitEthernet0/1/8 GigabitEthernet0/1/0 0 24 253 0 0 24 0 60 3 384 192.168.2.1 in 192.168.1.3 0 192.168.1.4 0 0.0.0.0 UNKNOWN 0 0 0 0 0 0 0 0 0 0.0.0.0 0 0 2018-05-09 11:38:07 2018-05-09 11:40:30 -- -- -:-
Configuration Files
CE configuration file
# sysname CE # interface GigabitEthernet 0/1/0 ip address 192.168.1.2 255.255.255.0 # returnPE configuration file
# slot 1 ip netstream sampler to slot self # sysname PE # ip netstream tcp-flag enable ip netstream sampler fix-packets 10000 inbound ip netstream sampler fix-packets 10000 outbound ip netstream export source 192.168.2.1 ip netstream export host 192.168.2.2 9001 # interface gigabitethernet 0/1/8 ip address 192.168.2.1 255.255.255.0 # interface GigabitEthernet 0/1/0 ip address 192.168.1.1 255.255.255.0 ip netstream inbound ip netstream outbound # return