Example for Configuring KOD in Unicast Client/Server Mode
Context
Networking Requirements
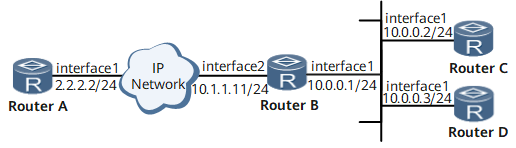
On the network shown in Figure 1:
Device A functions as a unicast NTP server. The clock on it functions as a stratum 2 NTP master clock.
Device B functions as a unicast NTP client. Its clock needs to be synchronized with the clock on Device A.
Device C and Device D function as NTP clients of Device B.
NTP authentication needs to be enabled.
- Enable KOD on Device A so that Device A can perform access control when it receives a large number of access packets and cannot bear the load.

Interface 1 and Interface 2 in this example represent GE 0/1/0 and GE 0/1/8, respectively.
Precautions
- Before configuring a key on the client and server, ensure that the key already exists.
- The authentication key must be reliable on both the client and server. Authentication must be enabled on the client.
Configuration Roadmap
The configuration roadmap is as follows:
Configure Device A as an NTP server and configure a master clock on it.
Configure Device B as an NTP client and synchronize its clock with the clock of Device A.
Configure Device C and Device D as NTP clients to synchronize their clocks with the clock of Device B.
Enable NTP authentication on all Devices.

You must enable NTP authentication on the client prior to specifying the IP address of the NTP server and the authentication key to be sent to the server. Otherwise, NTP authentication is not performed before clock synchronization.
To implement authentication successfully, configure both the server and the client.
Data Preparation
To complete the configuration, you need the following data:
IP address of the reference clock
Stratum of the NTP master clock
Authentication key and its ID
Password
Procedure
- Configure the IP addresses based on Figure 1 so that Device A, Device B, Device C, and Device D are routable. For configuration details, see Configuration Files in this section.
- Configure an NTP master clock and listening interfaces on Device A and enable NTP authentication.
# Set the local clock on Device A as a stratum 2 NTP master clock.
<HUAWEI> system-view [~HUAWEI] sysname DeviceA [*HUAWEI] commit [~DeviceA] ntp-service refclock-master 2
# Specify a listening interface on Device A.
[~DeviceA] ntp-service server source-interface gigabitethernet 0/1/0
# Enable NTP authentication, configure an authentication key, and declare the key to be reliable.
[*DeviceA] ntp-service authentication enable [*DeviceA] ntp-service authentication-keyid 42 authentication-mode hmac-sha256 Hello123 [*DeviceA] ntp-service reliable authentication-keyid 42 [*DeviceA] commit
Note that authentication keys configured on the server and the client must be the same.
# Configure an ACL rule.[~DeviceA] acl 2000 [*DeviceA-acl4-basic-2000] rule 2000 permit source 10.0.0.1 0 [*DeviceA-acl4-basic-2000] commit [*DeviceA-acl4-basic-2000] quit
# Configure access control.
[~DeviceA] ntp-service access limited 2000
# Configure the minimum and average intervals for receiving NTP packets.
[*DeviceA] ntp-service discard min-interval 4 avg-interval 4
# Enable KOD.
[*DeviceA] ntp-service kod-enable [*DeviceA] commit
- Configure an NTP master clock and listening interfaces on Device B and enable NTP authentication.
# On Device B, enable NTP authentication, configure an authentication key, and declare the key to be reliable.
<HUAWEI> system-view [~HUAWEI] sysname DeviceB [*HUAWEI] commit [~DeviceB] ntp-service authentication enable [*DeviceB] ntp-service authentication-keyid 42 authentication-mode hmac-sha256 Hello123 [*DeviceB] ntp-service reliable authentication-keyid 42
# Specify a listening interface on Device B.
[*DeviceB] ntp-service server source-interface gigabitethernet 0/1/0
# Specify Device A to be the NTP server of Device B and use the authentication key.
[*DeviceB] ntp-service unicast-server 2.2.2.2 authentication-keyid 42 [*DeviceB] commit
- On Device C, specify Device B to be the NTP server of Device C.
<HUAWEI> system-view [~HUAWEI] sysname DeviceC [*HUAWEI] commit [~DeviceC] ntp-service authentication enable [*DeviceC] ntp-service authentication-keyid 42 authentication-mode hmac-sha256 Hello123 [*DeviceC] ntp-service reliable authentication-keyid 42 [*DeviceC] ntp-service unicast-server 10.0.0.1 authentication-keyid 42 [*DeviceC] commit
- On Device D, specify Device B to be the NTP server of Device D.
<HUAWEI> system-view [~HUAWEI] sysname DeviceD [*HUAWEI] commit [~DeviceD] ntp-service authentication enable [*DeviceD] ntp-service authentication-keyid 42 authentication-mode hmac-sha256 Hello123 [*DeviceD] ntp-service reliable authentication-keyid 42 [*DeviceD] ntp-service unicast-server 10.0.0.1 authentication-keyid 42 [*DeviceD] commit
- Verify the configuration
After completing the configurations, check that the clock on Device B can be synchronized with the clock on Device A.
View the NTP status on Device B. You can find that the clock state is synchronized. The stratum of the clock is 3, one stratum lower than that on DeviceA.
[~DeviceB] display ntp-service status clock status: synchronized clock stratum: 3 reference clock ID: 2.2.2.2 nominal frequency: 60.0002 Hz actual frequency: 60.0002 Hz clock precision: 2^18 clock offset: 3.8128 ms root delay: 31.26 ms root dispersion: 74.20 ms peer dispersion: 34.30 ms reference time: 11:55:56.833 UTC Mar 2 2006(C7B15BCC.D5604189) synchronization state: spike (clock will be set in 180 secs)
After completing the configurations, check that the clock on Device C can be synchronized with the clock on Device B.
View the NTP status on Device C. You can find that the clock state is synchronized. The stratum of the clock is 4, one stratum lower than that on Device B.
[~DeviceC] display ntp-service status clock status: synchronized clock stratum: 4 reference clock ID: 10.0.0.1 nominal frequency: 60.0002 Hz actual frequency: 60.0002 Hz clock precision: 2^18 clock offset: 3.8128 ms root delay: 31.26 ms root dispersion: 74.20 ms peer dispersion: 34.30 ms reference time: 11:55:56.833 UTC Mar 2 2006(C7B15BCC.D5604189) synchronization state: spike (clock will be set in 180 secs)
View the NTP status on DeviceD. The command output shows that the clock state is synchronized and the stratum of the clock on DeviceD is 4, one stratum lower than that on DeviceB.
[~DeviceD] display ntp-service status clock status: synchronized clock stratum: 4 reference clock ID: 10.0.0.1 nominal frequency: 60.0002 Hz actual frequency: 60.0002 Hz clock precision: 2^18 clock offset: 3.8128 ms root delay: 31.26 ms root dispersion: 74.20 ms peer dispersion: 34.30 ms reference time: 11:55:56.833 UTC Mar 2 2006(C7B15BCC.D5604189) synchronization state: spike (clock will be set in 180 secs)
View NTP status on Device A.
[~DeviceA] display ntp-service status clock status: synchronized clock stratum: 2 reference clock ID: LOCAL(0) nominal frequency: 60.0002 Hz actual frequency: 60.0002 Hz clock precision: 2^18 clock offset: 0.0000 ms root delay: 0.00 ms root dispersion: 26.50 ms peer dispersion: 10.00 ms reference time: 12:01:48.377 UTC Mar 2 2006(C7B15D2C.60A15981) synchronization state: spike (clock will be set in 180 secs)
Configuration Files
Device A configuration file
# sysname DeviceA # interface GigabitEthernet0/1/0 undo shutdown ip address 2.2.2.2 255.255.255.0 # ospf 1 area 0.0.0.0 network 2.2.2.0 0.0.0.255 # ntp-service authentication enable ntp-service authentication-keyid 42 authentication-mode hmac-sha256 cipher %#%#JA!v6M22=Gg\{>U.lx%#)c%yY}0*"/`5mi><QS)L%#%# ntp-service reliable authentication-keyid 42 ntp-service refclock-master 2 acl 2000 rule 2000 permit source 10.0.0.1 0 ntp-service access limited 2000 ntp-service discard min-interval 4 avg-interval 4 ntp-service server source-interface gigabitethernet 0/1/0 ntp-service kod-enable # return
Device B configuration file
# sysname DeviceB # interface GigabitEthernet0/1/0 undo shutdown ip address 10.0.0.1 255.255.255.0 interface GigabitEthernet0/1/8 undo shutdown ip address 10.0.1.1 255.255.255.0 # ospf 1 area 0.0.0.0 network 10.0.1.0 0.0.0.255 network 10.0.0.0 0.0.0.255 # ntp-service authentication enable ntp-service authentication-keyid 42 authentication-mode hmac-sha256 cipher %#%#>hD8))_H-XZVut2u3!_0lq3,+Ph=:OE}pX;T2M'9%#%# ntp-service reliable authentication-keyid 42 ntp-service unicast-server 2.2.2.2 authentication-keyid 42 ntp-service server source-interface gigabitethernet 0/1/0 # return
Device C configuration file
# sysname DeviceC # interface GigabitEthernet0/1/0 undo shutdown ip address 10.0.0.2 255.255.255.0 # ntp-service authentication enable ntp-service authentication-keyid 42 authentication-mode hmac-sha256 cipher %#%#m:fVJfk*r&3x"1J`21^K`Y;LH;B+g(t2<ZX^}Q_~%#%# ntp-service reliable authentication-keyid 42 ntp-service unicast-server 10.0.0.1 authentication-keyid 42 # return
Device D configuration file
# sysname DeviceD # interface GigabitEthernet0/1/0 undo shutdown ip address 10.0.0.3 255.255.255.0 # ntp-service authentication enable ntp-service authentication-keyid 42 authentication-mode hmac-sha256 cipher %#%#$\`_6BKWy1]kdR@=c;O@UX!)Vor5iYi|zIYEG_v5%#%# ntp-service reliable authentication-keyid 42 ntp-service unicast-server 10.0.0.1 authentication-keyid 42 # return