Configuring PKI Certificate
Configuring PKI certificate involves creating RSA key pairs, configuring entity information, obtaining certificates and verifying the certification validity.
Applicable Environment
Two devices use digital certificates to authenticate each other's identity when establishing a VPN, which prevents middleman attacks.
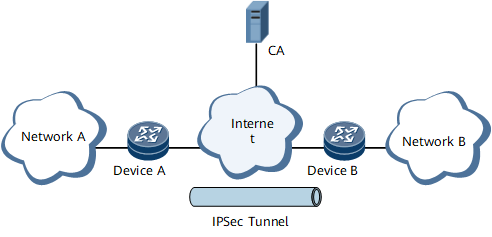
As shown in Figure 1, Device A and Device B apply for certificates from a same CA server, and download CA certificates and local certificates from the server. When an IPsec VPN needs to be established for data transmission between Device A and Device B, Device A and Device B must authenticate each other using certificates. When both have passed authentication, they can set up the IPsec VPN.
Figure 1 Diagram for configuring certificate-based authentication

- Creating an RSA Key Pair
- Before applying for certificates, create RSA key pairs.
- Configuring Entity Information
- When applying for certificates, an entity must add entity information to a certificate request file and send the file to the CA. The CA uses a piece of important information to describe an entity, and identifies the entity using a unique Distinguished Name (DN).
- Obtaining a Certificate
- To use certificates to authenticate users, the entity needs to obtain a local certificate and CA certificates. A local certificate proves the identity of the entity, and a CA certificate proves that the local certificate is issued by a legal CA.
- Verifying the PKI Certificate Configuration
- After configuring PKI certificate, check the configurations.