Example for Configuring a Local SNMPv3 User on a Device to Communicate with an NMS
This section provides an example for configuring a local SNMPv3 user on a device to communicate with an NMS. The NMS is granted permissions to manage some MIB objects on the device.
Networking Requirements
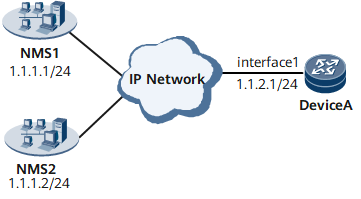
In Figure 1, two NMSs and the router are connected through a public network. NMS2 is allowed to use a local SNMPv3 user account to manage all objects on the router, whereas NMS1 no longer manages the router.
The data transmitted between NMS2 and the router needs to be encrypted and the NMS administrator needs to be authenticated because the data has to travel across the public network.
Contact information of the equipment administrator needs to be configured on the router. This helps the NMS administrator to contact the equipment administrator if a fault occurs.

Interface 1 in this example represents GE 0/1/0.
Configuration Roadmap
The configuration roadmap is as follows:
Configure an AAA task group and grant permissions.
Configure an AAA user group and associate it with the task group.
Configure a local AAA user and set its access service type to SNMP.
Enable the SNMP agent.
Configure the router to run SNMPv3.
- Configure a source interface for SNMP to receive and respond to NMS request packets.
Configure a local SNMPv3 user.
Configure the contact information of the equipment administrator.
Configure NMS2.
Data Preparation
To complete the configuration, you need the following data:
SNMP version
User group name
Task group name
User name and password
Authentication and privacy algorithms
Contact information of the device administrator
Procedure
- Configure available routes between the router and the NMSs. Details for the configuration procedure are not provided here.
- Configure an AAA task group and grant permissions.
<HUAWEI> system-view [~HUAWEI] sysname DeviceA [~HUAWEI] aaa [~HUAWEI-aaa] task-group tg1 [*HUAWEI-aaa-task-group-tg1] task snmp read [*HUAWEI-aaa-task-group-tg1] task snmp write [*HUAWEI-aaa-task-group-tg1] commit [~DeviceA-aaa-task-group-tg1] quit
- Configure an AAA user group and associate it with the task group.
[~DeviceA-aaa] user-group grp1 [*DeviceA-aaa-user-group-grp1] task-group tg1 [*DeviceA-aaa-user-group-grp1] commit [~DeviceA-aaa-user-group-grp1] quit
- Configure a local AAA user and set its access service type to SNMP.
[~DeviceA-aaa] local-user nms2-admin password Please configure the password (8-128) Enter Password: Confirm Password: [*DeviceA-aaa] local-user nms2-admin user-group grp1 [*DeviceA-aaa] local-user nms2-admin service-type snmp [*DeviceA-aaa] commit [~DeviceA-aaa] quit
- Enable the SNMP agent.
[~DeviceA] snmp-agent password min-length 10 [*DeviceA] snmp-agent [*DeviceA] commit
- Configure the router to run SNMPv3.
[~DeviceA] snmp-agent sys-info version v3 [*DeviceA] commit
- Configure a source interface for SNMP to receive and respond to NMS request packets.
[~DeviceA] snmp-agent protocol source-interface Loopback0 [*DeviceA] commit
- Configure a local SNMPv3 user.
[~DeviceA] snmp-agent local-user v3 nms2-admin authentication-mode sha2-224 privacy-mode aes128 Please configure the authentication password (10-255) Enter Password: Confirm Password: Please configure the privacy password (10-255) Enter Password: Confirm Password: [*DeviceA] commit
- Configure the contact information of the device administrator.
[~DeviceA] snmp-agent sys-info contact call Operator at 010-12345678 [*DeviceA] commit
- Configure the NMS.
For details on how to configure NMS2, see the relevant NMS configuration guide.
- Verify the configuration.
After the configuration is complete, run the following commands to verify that the configuration has taken effect.
# Check the configured SNMP version.
[~DeviceA] display snmp-agent sys-info version SNMP version running in the system: SNMPv3
# Display local user information.
<DeviceA> display snmp-agent local-user User name: nms2-admin Engine ID: 800007DB03001974593301 Authentication Protocol: sha Privacy Protocol: aes128 State: Active# Display the contact information of the device administrator.
<DeviceA> display snmp-agent sys-info contact The contact person for this managed node: call Operator at 010-12345678
Configuration Files
router configuration file
# sysname DeviceA # aaa local-user nms2-admin password irreversible-cipher %#%#n}=%C*UimYlx9-:$>T=*_y4PX*e~u6I_Aa9s=I1$%#%# local-user nms2-admin service-type snmp local-user nms2-admin user-group grp1 # task-group tg1 task snmp write # user-group grp1 task-group tg1 # interface GigabitEthernet0/1/0 undo shutdown ip address 1.1.2.1 255.255.255.0 # interface loopback0 ip address 1.1.3.1 255.255.255.255 # ospf 1 area 0.0.0.0 network 1.1.2.0 0.0.0.255 network 1.1.3.1 0.0.0.0 # snmp-agent snmp-agent password min-length 10 snmp-agent local-engineid 800007DB03001974593301 # snmp-agent protocol source-interface Loopback0 # snmp-agent sys-info contact call Operator at 010-12345678 snmp-agent sys-info version v3 snmp-agent local-user v3 nms2-admin authentication-mode sha2-224 cipher %#%#n}=%C*UimYlx9-:$>T=*_y4PX*e~u6I_Aa9s=I1$%#%# privacy-mode aes128 cipher %#%#at{pQGh!uMyq..8WSJ(<bU`~K_)[f-}s&*Gmw!iE%#%# # return