SRv6 Midpoint Protection
TI-LFA FRR Failure Scenario
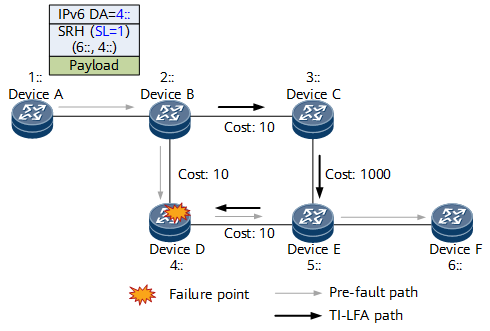
In SRv6 TE Policy scenarios, the forwarding path of data packets usually needs to be constrained by specifying the nodes or links they need to traverse. For example, on the network shown in Figure 1, node A is required to send a packet to node F over a forwarding path that passes through node D. Because the backup path also needs to pass through node D, TI-LFA FRR cannot provide protection if this node fails.
SRv6 Midpoint Protection
In an SRv6 TE Policy scenario, strict node constraints may result in a TI-LFA FRR protection failure. To resolve this issue, a proxy forwarding node (a node upstream to the failed midpoint) takes over from the failed midpoint to complete the forwarding. Specifically, after detecting that the next-hop interface of the packet fails, the next-hop address is the destination address of the packet, and the SL value is greater than 0, the proxy forwarding node performs the End behavior on behalf of the midpoint. The behavior involves decrementing the SL value by 1, copying the next SID to the DA field in the outer IPv6 header, and then forwarding the packet according to the instruction bound to the SID. In this way, the failed midpoint is bypassed, achieving SRv6 midpoint protection.
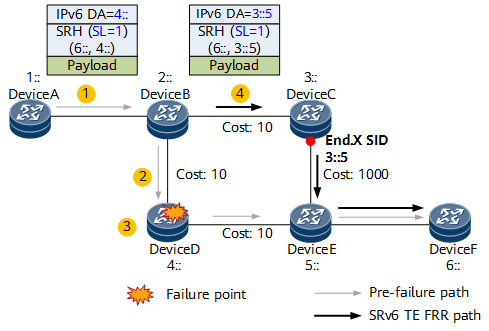
- Node A forwards a packet to destination node F, with an SRv6 SRH instructing the packet to pass through the midpoint node D.
- If node D fails, node B detects that the next-hop interface of the received packet fails. It also learns that the next-hop address is the current destination address 4:: of the packet, and the SL value is greater than 0. In this case, node B functions as a proxy forwarding node, decrementing the SL value by 1 and copying the next SID 6:: to the DA field in the outer IPv6 header. Because the SL value is now 0, node B can remove the SRH and then search the corresponding table to forward the packet based on the destination address 6::.
- The primary next hop to the destination address 6:: is still node D. Because the SL value is 0 and node B is not the penultimate hop of the destination address, node B can no longer perform proxy forwarding. Instead, it switches the packet to a backup path according to the normal TI-LFA process, with the repair segment list on the backup path as <3::5>. As such, node B executes the H.Insert behavior, which involves encapsulating the segment list 3::5 into the packet, adding an SRH, and then forwarding the packet to node F over the backup path.
- After node A detects that node D fails and that IGP convergence is completed, it deletes the forwarding entry towards node D. Consequently, when node A searches the corresponding table based on 4::, it cannot find any matching route. In this case, node A needs to function as a proxy forwarding node to perform proxy forwarding, so it decrements the SL value by 1, copies the next SID 6:: to the outer IPv6 header, searches the corresponding table based on the destination address 6::, and then forwards the packet to node B accordingly. If node B has already converged, it forwards the packet to node F over the post-convergence shortest path; otherwise, it forwards the packet to node F over the backup path according to the TI-LFA process. In this way, the failed node D is bypassed.Figure 2 SRv6 midpoint protection

SRv6 midpoint protection uses the next SID to guide packet forwarding over the bypass path, thereby bypassing the failure point. This mechanism is similar to MPLS TE FRR, which enables traffic to bypass the failure point using a bypass LSP. SRv6 midpoint protection is therefore also called SRv6 TE FRR.
Differences Between TI-LFA FRR and Midpoint Protection
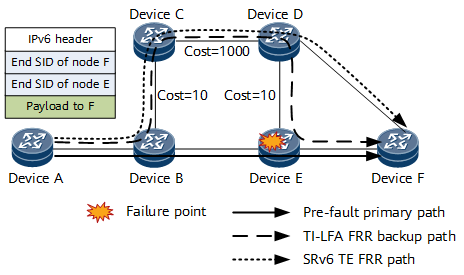
The difference between SRv6 TI-LFA FRR and midpoint protection lies in whether the next-hop node is a transit node or a midpoint that corresponds to a SID in the SRH.
On the network shown in Figure 3, node A sends a packet carrying the segment list <E, F>. Because SRv6 TI-LFA FRR computes a backup path based on the destination address of the packet, the backup path passes through node E. If node E fails, SRv6 TI-LFA FRR cannot provide protection. In contrast, in an SRv6 midpoint protection scenario, packet forwarding is implemented based on the next SID to be processed. This ensures that the failed midpoint node E is bypassed, thereby achieving SRv6 TE Policy midpoint protection.