Configuring Three-Segment VXLAN to Implement Layer 3 Interworking
The three-segment VXLAN can be configured to enable communications between inter-subnet VMs in DCs that belong to different ASs.
Context
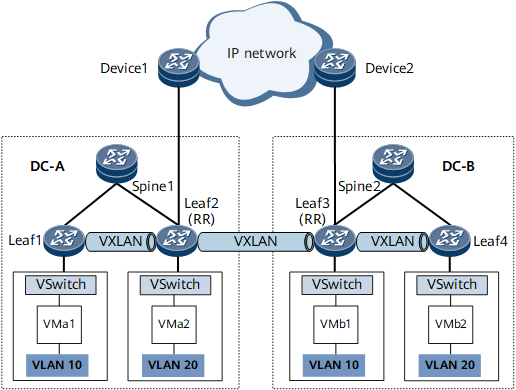
As shown in Figure 1, BGP EVPN must be configured to create VXLAN tunnels between distributed gateways in each DC and to create VXLAN tunnels between leaf nodes so that the inter-subnet VMs in DC A and DC B can communicate with each other.
When DC A and DC B belong to the same BGP AS, Leaf2 or Leaf3 does not forward EVPN routes received from an IBGP EVPN peer to other IBGP EVPN peers. Therefore, it is necessary to configure Leaf2 and Leaf3 as route reflectors (RRs).
Procedure
- Configure BGP EVPN within DC A and DC B to establish VXLAN tunnels. For details, see Configuring VXLAN in Distributed Gateway Mode Using BGP EVPN.
- Configure BGP EVPN on Leaf2 and Leaf3 to establish a VXLAN tunnel between them. For details, see Configuring VXLAN in Distributed Gateway Mode Using BGP EVPN.
- (Optional) Configure Leaf2 and Leaf3 as RRs. For details, see Configuring a BGP Route Reflector.
- Configure Leaf2 and Leaf3 to advertise routes that are re-originated by the EVPN address family to BGP EVPN peers.
- (Optional) Configure local EVPN route leaking on Leaf2 and Leaf3. To use different VPN instances for different service access in a data center, and to shield the VPN instance allocation within the data center from the external network by using an external VPN instance for communication with other data centers, perform the following steps on each edge leaf node:
- Run commit
The configuration is committed.