ND Fundamentals
Neighbor discovery (ND) is a group of messages and processes that identify relationships between neighboring nodes. IPv6 ND provides similar functions as the Address Resolution Protocol (ARP) and ICMP router discovery in IPv4, as well as additional functions.
Router Solicitation (RS): After startup, a host sends an RS message to a router, and waits for the router to respond with a Router Advertisement (RA) message.
Router Advertisement (RA): A router periodically advertises RA messages containing prefixes and flag bits.
Neighbor Solicitation (NS): An IPv6 node uses NS messages to obtain the link-layer address of its neighbor, check that the neighbor is reachable, and detect address conflicts.
Neighbor Advertisement (NA): After receiving an NS message, an IPv6 node responds with an NA message. In addition, the IPv6 node initially sends NA messages when the link layer changes.
Duplicate Address Detection
Duplicate address detection (DAD) checks whether an IPv6 unicast address is being used before the address is assigned to an interface. DAD is required if IPv6 addresses are configured automatically. An IPv6 unicast address that is assigned to an interface but not verified by DAD is called a tentative address. An interface cannot use such an address for unicast communication but will join two multicast groups: all-nodes multicast group and solicited-node multicast group.
IPv6 DAD is similar to IPv4 gratuitous ARP. A node sends an NS message that requests the tentative address as the destination address to the solicited-node multicast group. If the node receives an NA message in response, another node is using the tentative address for communication. In this case, the node does not use the tentative address for communication.
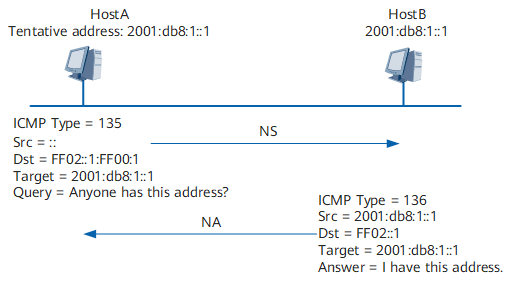
Figure 1 shows a DAD example.
The IPv6 address 2001:db8:1::1 is assigned to HostA as a tentative IPv6 address. To check the validity of this address, HostA sends an NS message containing the requested address 2001:db8:1::1 to the solicited-node multicast group to which 2001:db8:1::1 belongs. Because 2001:db8:1::1 is not specified, the source address of the NS message is an unspecified address. After receiving the NS message, HostB processes the message as follows:
If 2001:db8:1::1 is a tentative or unused address of HostB, HostB does not use this address as an interface address, nor does it send an NA message.
If HostB checks that 2001:db8:1::1 is a used address, it sends an NA message that contains 2001:db8:1::1 to 2001:db8:2::1. After receiving the message, HostA finds that its tentative address is duplicate.
Address Conflict Self-Recovery
When DAD detects an address conflict on an interface, the IPv6 protocol status of the interface remains down. The interface can go up only after the shutdown and undo shutdown commands are manually run. Address conflict self-recovery resolves this issue. After an IPv6 address conflict is detected using DAD, a device automatically performs address conflict self-recovery until the address conflict is removed and the IPv6 protocol of the interface goes up. Address conflict self-recovery applies to the following scenarios:
- A device receives an NA message after sending an NS message (common address conflict).
- A device receives an NS message with the same target address but a different source MAC address from a peer device while sending an NS message.
- A device receives an NS message with the same target address and source MAC address from a peer device while sending an NS message.
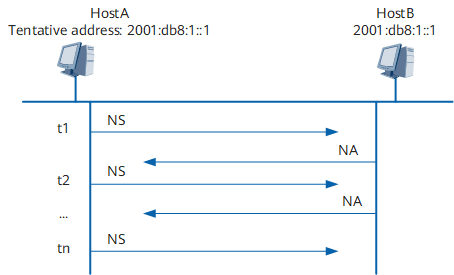
Figure 2 shows an address conflict self-recovery example (common address conflict). The principles for other scenarios are similar to those for the common address conflict scenario.
At t1, HostA sends an NS message. After receiving an NA message from HostB, HostA continues to perform address conflict detection at t2 and send an NS message to HostB.
- If HostB replies with an NA message, HostA continues to perform address conflict detection at the next time and send an NS message to HostB.
- If HostB does not reply with an NA message, the address is available and HostA stops sending NS messages to HostB.
Neighbor Discovery
Similar to ARP in IPv4, IPv6 ND parses the neighbor addresses and detects the availability of neighbors based on NS and NA messages.
When a node needs to obtain the link-layer address of another node on the same local link, it sends an ICMPv6 type 135 NS message. An NS message is similar to an ARP request message in IPv4, but is destined for a multicast address rather than a broadcast address. Only the node whose last 24 bits in its address are the same as the multicast address can receive the NS message. This reduces the possibility of broadcast storms. A destination node fills its link-layer address in the NA message.
An NS message is also used to detect the availability of a neighbor when the link-layer address of the neighbor is known. An NA message is the response to an NS message. After receiving an NS message, a destination node responds with an ICMPv6 type 136 NA message on the local link. After receiving the NA message, the source node can communicate with the destination node. When the link-layer address of a node on the local link changes, the node actively sends an NA message.
Router Discovery
Router discovery is used to locate a neighboring router and learn the address prefix and configuration parameters related to address autoconfiguration. IPv6 router discovery is implemented based on the following messages:
RS message
When a host is not configured with a unicast address, for example, when the system has just started, it sends an RS message. An RS message helps the host rapidly perform address autoconfiguration without waiting for the RA message that is periodically sent by an IPv6 device. An RS message is of the ICMPv6 type 133.
RA message
Interfaces on each IPv6 device periodically send RA messages only when they are enabled to do so. After a router receives an RS message from an IPv6 device on the local link, the router responds with an RA message. An RA message is sent to the all-nodes multicast address (FF02::1) or to the IPv6 unicast address of the node that sent the RS message. An RA message is of the ICMPv6 type 134 and contains the following information:
Whether or not to use address autoconfiguration
Supported autoconfiguration type: stateless or stateful
One or more on-link prefixes (On-link nodes can perform address autoconfiguration using these address prefixes.)
Lifetime of the advertised on-link prefixes
Whether the router sending the RA message can be used as a default router (If so, the lifetime of the default router is also included, expressed in seconds.)
Other information about the host, such as the hop limit and the MTU that specifies the maximum size of the packet initiated by a host
After an IPv6 host on the local link receives an RA message, it extracts the preceding information to obtain the updated default router list, prefix list, and other configurations.
Neighbor Tracking
A neighbor state can transit from one to another. Hardware faults and hot swapping of interface cards interrupt communication with neighboring devices. Communication cannot be restored if the destination of a neighboring device becomes invalid, but it can be restored if the path fails. Nodes need to maintain a neighbor table to monitor the state of each neighboring device.
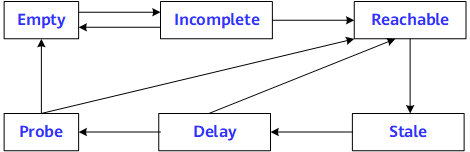
RFC standards define five neighbor states: Incomplete, Reachable, Stale, Delay, and Probe.
Figure 3 shows the transition of neighbor states. The Empty state indicates that the neighbor table is empty.
The following example describes changes in neighbor state of node A during its first communication with node B.
- Node A sends an NS message and generates a cache entry. The neighbor state of node A is Incomplete.
- If node B replies with an NA message, the neighbor state of node A changes from Incomplete to Reachable. Otherwise, the neighbor state changes from Incomplete to Empty after a certain period of time, and node A deletes this entry.
- After the neighbor reachable time times out, the neighbor state changes from Reachable to Stale, indicating that the neighbor reachable state is unknown.
- If node A in the Reachable state receives an unsolicited NA message from node B, and the link-layer address of node B carried in the message is different from that learned by node A, the neighbor state of node A changes to Stale.
- After the aging time of ND entries in the Stale state expires, the neighbor state changes to Delay.
- After a period of time (5s), the neighbor state changes from Delay to Probe. During this time, if node A receives an NA message, the neighbor state of node A changes to Reachable.
- Node A in the Probe state sends three unicast NS messages at the configured interval (1s). If node A receives an NA message, the neighbor state of node A changes from Probe to Reachable. Otherwise, the state changes to Empty and node A deletes the entry.
Address Autoconfiguration
A router can notify hosts of how to perform address autoconfiguration using RA messages and prefix flags. For example, the router can specify stateful (DHCPv6) or stateless address autoconfiguration for the hosts.
When stateless address autoconfiguration is employed, a host uses the prefix information in a received RA message and local interface ID to automatically form an IPv6 address, and sets the default router according to the default router information in the message. Or the host obtains DNS information based on the RDNSS and DNSSL options in the message.
Security Neighbor Discovery
IPsec is well suited for IPv6 networks, but it does not address all security issues. In addition to IPsec, IPv6 requires more security mechanisms.
In the IPv6 protocol suite, ND is significant in ensuring the availability of neighbors on the local link. However, as network security problems intensify, the security of ND becomes a concern. Standards define several threats to ND security, some of which are described as follows.
Attack Method |
Description |
|---|---|
NS/NA spoofing |
An attacker sends an authorized node (host or router) an NS message with a bogus source link-layer address option, or an NA message with a bogus target link-layer address option. Then packets from the authorized node are sent to this link-layer address. |
Neighbor unreachability detection (NUD) failure |
An attacker repeatedly sends forged NA messages in response to an authorized node's NUD NS messages so that the authorized node cannot detect the neighbor unreachability. The consequences of this attack depend on why the neighbor became unreachable and how the authorized node would behave if it knew that the neighbor has become unreachable. |
Duplicate Address Detection (DAD) attack |
An attacker responds to every DAD attempt made by a host that accesses the network, claiming that the address is already in use. This is performed to ensure that the host will never obtain an address. |
Spoofed Redirect message |
An attacker uses the link-local address of the first-hop router to send a Redirect message to an authorized host. The authorized host accepts this message because the host mistakenly considers that the message came from the first-hop router. |
Replay attack |
An attacker obtains valid messages and replays them. Even if Neighbor Discovery Protocol (NDP) messages are cryptographically protected so that their contents cannot be forged, they are still prone to replay attacks. |
Bogus address prefix |
An attacker sends a bogus RA message specifying that some prefixes are on-link. If a prefix is on-link, a host will not send any packets that contain this prefix to the router. Instead, the host will send NS messages to attempt address resolution, but the NS messages are not responded to. As a result, the host is denied services. |
Malicious last-hop router |
An attacker multicasts bogus RA messages or unicasts bogus RA messages in response to multicast RS messages to a host attempting to discover a last-hop router. If the host selects the attacker as its default router, the attacker is able to insert himself as a man-in-the-middle and intercepts all messages exchanged between the host and its destination. |
To counter these threats, SEND specifies security mechanisms to extend ND. SEND defines cryptographically generated addresses (CGAs), CGA option, and Rivest Shamir Adleman (RSA) Signature option, which are used to ensure that the sender of an ND message is the owner of the message's source address. SEND also defines Timestamp and Nonce options to prevent replay attacks.
- CGA: contains an IPv6 interface identifier that is generated from a one-way hash of the public key and associated parameters.
- CGA option: contains information used to verify the sender's CGA, including the modifier value and public key of the sender. This option is used to check the validity of source IPv6 addresses carried in ND messages.
- RSA Signature option: contains the hash value of the sender's public key and contains the digital signature generated from the sender's private key and ND messages. This option is used to check the integrity of ND messages and authenticate the identity of the sender.

If an attacker uses an address that belongs to an authorized node, the attacker must use the node's public key for encryption. Otherwise, the receiver can detect the attempted attack after checking the CGA option. Even if the attacker obtains the public key of the authorized node, the receiver can still detect the attempted attack after checking the digital signature, which is generated from the sender's private key.
- Timestamp option: a 64-bit unsigned integer field containing a timestamp. The value indicates the number of seconds since January 1, 1970, 00:00 UTC. This option prevents unsolicited advertisement messages and Redirect messages from being replayed. The receiver is expected to ensure that the timestamp of the recently received message is the latest.
- Nonce option: contains a random number selected by the sender of a solicitation message. This option prevents replay attacks during message exchange. For example, a sender sends an NS message carrying the Nonce option and receives an NA message as a response that also carries the Nonce option; the sender verifies the NA message based on the Nonce option.
To reject insecure ND messages, an interface can have the IPv6 SEND function configured. An ND message that meets any of the following conditions is insecure:
- The received ND message does not carry the CGA or RSA option, which indicates that the interface sending this message is not configured with a CGA.
- The key length of the received ND message exceeds the length limit that the interface supports.
- The rate at which ND messages are received exceeds the system rate limit.
- The time difference between the sent and received ND messages exceeds the time difference allowed by the interface.

As router implementation complies with standard protocols, the key-hash field in the RSA signature option of ND packets is generated using the SHA-1 algorithm. SHA-1 has been proved not secure enough.