Alarm Suppression
Alarm suppression can be classified as jitter suppression or correlation suppression.
Jitter suppression: uses alarm continuity analysis to allow the device not to report the alarm if a fault lasts only a short period of time and to display a stable alarm if a fault flaps.
Correlation suppression: uses alarm correlation rules to reduce the number of reported alarms, reducing the network load and facilitating fault locating.
Alarm Continuity Analysis
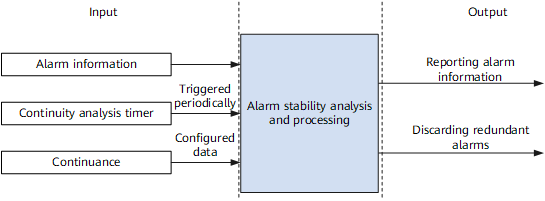
Figure 1 illustrates principles of alarm continuity analysis.
Alarm continuity analysis aims to differentiate events that require analysis and attention from those that do not and to filter out unstable events.
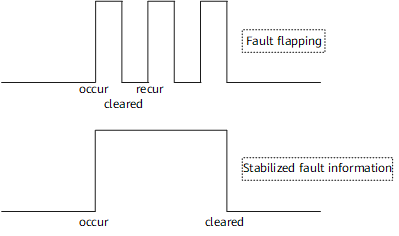
Continuity analysis measures time after a stable event, such as fault occurrence or fault rectification, occurs. If the event continues for a specified period of time, an alarm is sent. If the event is cleared, the event is filtered out and no alarm is sent. If a fault lasts only a short period of time, it is filtered out and no alarm is reported. Only stable fault information is displayed when a fault flaps.
Figure 2 shows the alarm generated if a fault flaps.
Alarm Correlation Analysis
An event may cause multiple alarms. These alarms are correlated. Alarm correlation analysis facilitates fault locating by differentiating root alarms from correlative alarms.
Alarm correlation analyzes the relationships between alarms based on the predefined alarm correlations. Use the linkDown alarm as an example. If a linkDown alarm is generated on an interface and the link down event results in the interruption of circuit cross connect (CCC) services on the interface, an hwCCCVcDown alarm is generated. According to the predefined alarm correlations, the linkDown alarm is a root alarm, and the hwCCCVcDown alarm is a correlative alarm.
After the system generates an alarm, it analyzes the alarm's correlation with other existing alarms. After the analysis is complete, the alarm carries a tag identifying whether it is a root alarm, a correlative alarm or independent alarm. If the alarm needs to be sent to a Simple Network Management Protocol (SNMP) agent and forwarded to the network management system (NMS), the system determines whether NMS-based correlative alarm suppression is configured.
If NMS-based correlative alarm suppression is configured, the system filters out correlative alarms and reports only root alarms and independent alarms to the NMS.
If NMS-based correlative alarm suppression is not configured, the system reports root alarms, correlative alarms and independent alarms to the NMS.