Support for Server Access Through Other Ports
The standard monitoring port number of SSH is 22. Attackers' continual access to this port consumes bandwidth resources and degrades server performance, preventing other users from accessing this port. This is a kind of denial of service (DoS) attack.
If you configure a non-standard port on the SSH server, attackers cannot detect the port change and continue to send socket connection requests to port 22. When the SSH server detects that the port is not a monitoring port, it rejects the requests.
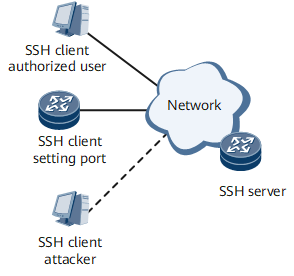
Figure 1 shows SSH server access through other ports.
Only authorized clients can set up socket connections with the SSH server through a non-standard monitoring port. The clients and server then negotiate an SSH version and algorithm, generate session keys, and implement authentication, session requests, and interactive sessions.
SSH can be applied to transit switching devices or edge devices on the network to implement secure user access and management on the devices.