TCP Applications of Keychain
In TCP application of Keychain, authentication is done at the TCP level, not at the application level. An application specifies that TCP will use Keychain to extract authentication information. TCP initializes or de-initializes itself with the Keychain module through the exposed Keychain initialization API.
TCP uses the Enhanced Authentication Option for authenticated communication, as specified in the TCPM Working Group draft. The following figure shows the Option format.
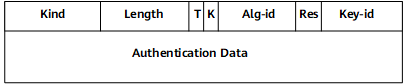
Because the draft is not a standard yet, the Internet Assigned Numbers Authority (IANA) has not defined the kind value (Option type) nor the algorithm-id for some algorithms. Thus different vendors use different values. To be interoperable with other vendors, the kind value and TCP algorithm-id of TCP are configurable and are maintained in Keychain.
The Keychain API provides a query function for applications to obtain TCP kind and algorithm-id values.
When a TCP application needs to send packets, it performs the process shown in the following figure.
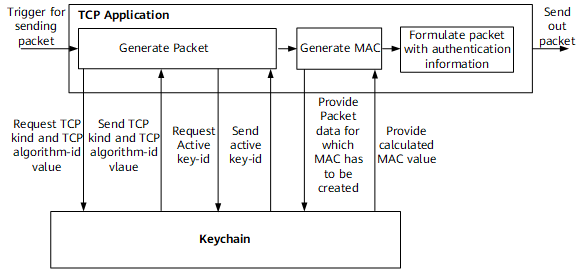
- To set the Enhanced Authentication Option, the application queries the Keychain module to get the active send key-id authentication information.
- From the authentication information obtained, the application generates packet data and sends it to Keychain to generate a MAC. Keychain calculates the MAC and sends it to the application.
- The application fills in the TCP kind value, TCP algorithm-id that corresponds to the active send key-id algorithm, and generated MAC in the Enhanced Authentication Option format and sends out the packet.
When the TCP application receives a packet, it performs the process shown in the following figure.
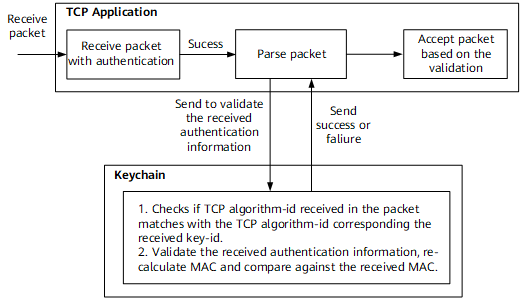
- The application extracts authentication information from the packet and provides it to Keychain for validation.
- Keychain checks whether the TCP algorithm-id in the packet matches the TCP algorithm-id that corresponds to the received key-id algorithm. If algorithm-ids do not match, then a failure message will be returned.
- Keychain re-calculates the MAC and compares the generated MAC and received MAC. If they match, then a success message is returned to the application; otherwise, a failure message is returned.
- The application accepts or rejects the packet based on the Keychain validation.