FTP Features Supported by VPNs
A File Transfer Protocol (FTP) client needs to access an FTP server deployed on a virtual private network (VPN) instead of a public IP network. A VPN extends a private network across a public network. It implements private transmission between devices and ensures secure data transmission on an insecure network, such as the Internet.
A VPN can also be used to connect two separate networks over the Internet and operate as a single network, which is useful for organizations that have two physical sites. VPNs are often used by organizations to provide remote access to secure organizational networks. VPNs do not require each PC to set up VPN connections, and a router is used to connect the two sites. After a VPN is deployed, the router maintains a constant tunnel between the two sites. The links between nodes of a VPN are formed over virtual circuits between hosts of a larger network.
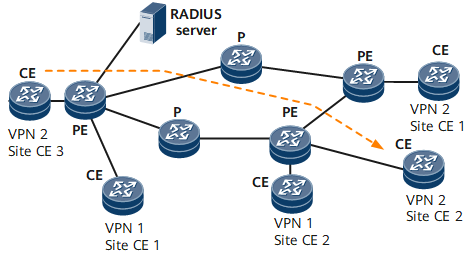
Figure 1 shows VPN networks.
Customer edge (CE): is physically deployed at the customer premise and provides access to VPN services.
Provider edge (PE): is located at the edge of a provider network and provides access services for customer sites. PEs monitor their connected VPNs and maintain VPN status.
Provider (P): operates inside a provider's core network and is not directly connected to CEs. Ps are used to implement provider-provisioned virtual private networks (PPVPNs). Ps do not monitor VPN sites or maintain VPN status. VPNs are generally configured on interfaces connecting PEs and CEs to provide VPN services to the CEs. As shown in Figure 1, Site CE 2 (FTP server) and Site CE 3 (FTP client) are connected to establish a VPN. The system must support VPN over IP.