Support for SFTP
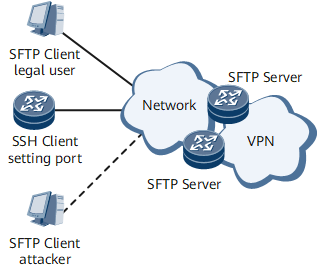
SFTP is based on SSH2.0. Before logging in to the server through an SFTP client, you must enter a correct user name, password, and private key for authentication by the server. After you are authenticated, you can remotely manage files as you do using FTP. The system uses a negotiated session key to encrypt data.
An attacker does not have the correct private key or password and therefore fails to be authenticated. In addition, the attacker cannot decrypt data or obtain a session key even though the attacker intercepts data exchanged between clients and the server. Only specified clients and the server can decrypt data exchanged between one another, ensuring secure data transmission on the network.
The system supports the following functions:
Support for both SFTP client and server functions
The device can function as either an SFTP server or an SFTP client that access other SFTP servers.
Enabling or disabling of the SFTP server function (disabled by default)
Disable the SFTP server function if you do not need it. This function is configured globally.
Supports the setting of the default directory that the SFTP client is allowed to access.
The server allocates different directories to clients, which implements file isolation among different clients.
Supports client and server using the transparent file system. For all file operations, a unified file system is used to access files on remote boards.
Supports the NETCONF file transfer process and provides acknowledge for a file transfer success or failure.
Figure 1 shows an SFTP application.