SSH
SSH Client
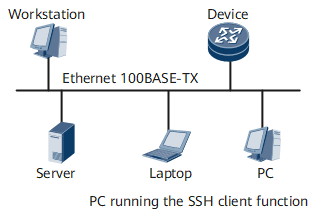
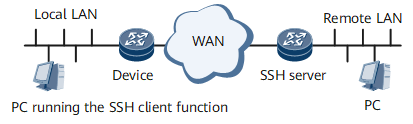
The Secure Shell (SSH) client function allows you to establish an SSH connection with a router that can function as an SSH server or with a UNIX host. Figure 1 and Figure 2 show how to set up SSH channels on a local area network (LAN) and a wide area network (WAN), respectively.
SFTP
Secure File Transfer Protocol (SFTP) is an SSH-based secure FTP. It enables users to securely log in to a remote device for file management and transmission, improving data transmission security. Through SFTP, you can log in to a remote SSH server from the device that functions as an SFTP client.
STelnet
STelnet is an SSH–based secure Telnet protocol. Compared with Telnet, STelnet enables an SSH server to perform authentication and bidirectional data encryption on a client, providing secure access services.
SCP
Secure Copy Protocol (SCP) is an SSH–based protocol that guarantees secure file transfer on a traditional insecure network by authenticating the client and encrypting the transmitted data.
SCP uses SSH for data transmission and user authentication, ensuring the authenticity and confidentiality of the transmitted data. A client can either upload files to a server or download files or directories from a server. SCP runs over TCP port 22 by default.
Server Access Through Other Ports
The standard monitoring port number of SSH is 22. Attackers' continual access to this port consumes bandwidth resources and degrades server performance, preventing other users from accessing this port. This is a kind of denial of service (DoS) attack.
If you set the monitoring port to a non-standard port on the SSH server, the attacker cannot detect the port change. This effectively prevents the attacker from continuously accessing the standard port to use the bandwidth and system resources. Authorized users can access the SSH service through the non-standard port to prevent DoS attacks.
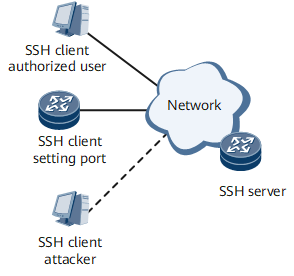
Figure 3 shows how the SSH server is accessed through other ports.
Only authorized clients can set up socket connections with the SSH server through a non-standard monitoring port. The clients and server then negotiate an SSH version and algorithm, generate session keys, and implement authentication, session requests, and interactive sessions.
SSH can be applied to transit switching devices or edge devices on the network to implement secure user access and management on the devices.
Secure Remote Access
SSH provides secure remote access on insecure networks through the following functions:
Supports Rivest-Shamir-Adleman (RSA)/digital signature algorithm (DSA)/elliptic curve cryptography (ECC) public key authentication modes. The public and private keys are generated based on the encryption principle of the asymmetric encryption system, ensuring secure key exchange and session process.
Supports certificate authentication modes. The client uses certificate signatures to authenticate the server, preventing the middleman attack.
Supports data encryption algorithms, such as Data Encryption Standard (DES), 3DES, and Advanced Encryption Standard (AES).
Encrypts the data exchanged between the SSH client and the server, including the user name and password. This encryption prevents the password from being intercepted.
SM2 elliptic curves cryptography (ECC) algorithm
The SM2 and RSA algorithms are based on the ECC and belong to the asymmetric cryptography system. The differences between the ECC and RSA algorithms are as follows:
- The RSA algorithm is based on large number factorization, which increases the key length. The long keys slow down the computing speed and complicate key storage and management.
- Based on discrete logarithm, the ECC algorithm is difficult to crack and is more secure.
Compared with the RSA algorithm, the ECC algorithm shortens the key length but provides the same security.
The ECC algorithm secures the encryption with short keys, which speeds up encryption. The ECC algorithm has the following advantages:
- Provides the same security with shorter keys.
- Requires less computation with a higher speed.
- Requires less storage space.
- Requires lower bandwidth.

To ensure high security, you are advised to use RSA_SHA2_256 and RSA_SHA2_512 for higher security.
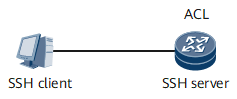
Support for ACLs
The SSH server can use access control lists (ACLs) to restrict SSH users' incoming and outgoing call authorities. ACL prevents unauthorized users from setting up TCP connections and entering the SSH negotiation phase, which improves SSH server security.
Support for IPv6
SSH clients support access to IPv6 host addresses, and SSH servers can receive IPv6 connection requests.