Overview of AAA and User Management
Definition
- Authentication: checks whether a user has the rights to access the network.
- Authorization: authorizes a user so that the user can use a specified service.
- Accounting: records the usage of network resources for charging purposes.
Purpose
AAA provides authentication, authorization, and accounting for users.
Benefits
AAA offers the following benefits:
AAA enhances system security by preventing invalid login.
HWTACACS
Terminal Access Controller Access Control System (TACACS) allows a remote access server to communicate with an authentication server in order to determine if the user has access to the network. TACACS+ is stronger than TACACS in security.
Unlike TACACS, TACACS+ provides separate authentication, authorization, and accounting services and encrypts the entire packet (except the header). TACACS+ allows any-content-or-length-based authentication, therefore enabling the TACACS+ client to use multiple authentication mechanisms.
Huawei Terminal Access Controller Access-Control System (HWTACACS) is developed based on TACACS+ and adds specific Huawei proprietary attributes, such as user group name, FTP directory, user right, and user access type. As a protocol intended for the control plane, HWTACACS provides access control services for AAA. In this document, AAA operations are performed by HWTACACS on the client side.
HWTACACS works in client mode. An HWTACACS instance that is operating in client mode is also known as a Network Access Server (NAS), which operates as a client of HWTACACS. Specifically, the HWTACACS client passes the user information to the designated HWTACACS servers and acts on the response received.
HWTACACS uses transmission control protocol (TCP) to provide reliable transmission of packets. HWTACACS encrypts the main contents of packets except the standard HWTACACS header, while separating authentication from authorization. HWTACACS is intended for security control and configuration authorization.
RADIUS
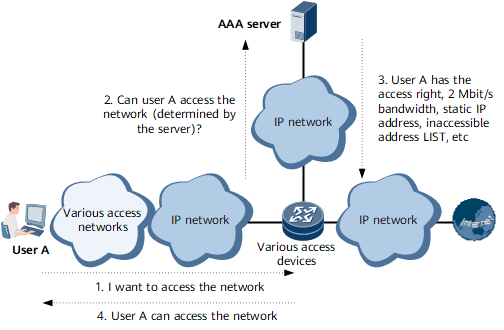
As one of the commonly-used protocols that implement Authentication, Authorization and Accounting (AAA), RADIUS was initially used to manage a large number of geographically-dispersed users that use serial ports and modems. Now it is widely used in the Network Access Server (NAS) system.
In a NAS system, a user must set up a connection with the NAS through a network, such as a telephony network, to obtain the rights to access certain networks or to use certain network resources. In this case, the NAS is in charge of authenticating the user or the connection.
Specifically, the NAS sends the user information to the RADIUS server. RADIUS prescribes how to transmit the user information and accounting information between the NAS and RADIUS servers. Upon receiving requests from users, the RADIUS server authenticates the users and then sends the required configuration information back to the NAS.
The authentication information is transmitted with key encryption between the NAS and RADIUS server to protect the user passwords on less secure networks.
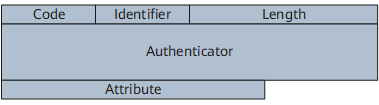
Figure 2 shows the format of a RADIUS packet.
A RADIUS packet has the following fields:
Code: indicates the message type, such as access request, access permit, or accounting request.
Identifier: contains numerics in ascending order. It is used to match the request packets and response packets.
Length: indicates the total length of all fields.
Authenticator: authenticates the reply from the RADIUS server.
Attribute: contains user-specific attributes.
Command-Line Authorization
Command-line authorization determines whether the user has the right to run a command. Command-line authorization is classified into level authorization and task authorization.
The priority of level authorization is higher than that of task authorization, that is, if both the level authorization and task authorization are configured on a local user, the level authorization takes effect.
Level authorization
The users of different levels can run commands of different levels.
By default, commands are registered according to levels 0 to 3.
- Commands of level 0, the visit level: include diagnostic tools (such as the ping and tracert commands) and the commands that are used to access a remote device (such as Telnet and SSH).
- Commands of level 1, the monitoring level: are used for system maintenance, including display commands.
- Commands of level 2, the configuration level: include commands used for service configuration, such as routing commands and commands at each network layer to provide network services to users.
- Commands of level 3, the management level: are used for system basic operation to support services, including file system, FTP, Trivial File Transfer Protocol (TFTP), and configuration file switching commands, slave board control commands, user management commands, command level configuration commands, and debugging commands.
To implement refined right management, the user can extend the command level range to levels 0 to 15. If the user does not adjust the level of any command, the levels of the registered commands are automatically adjusted as follows after the command level range is extended to levels 0 to 15:
- The levels of the original level-0 and level-1 commands remain unchanged.
- The level of the original level-2 commands is changed to level 10.
- The level of the original level-3 commands is changed to level 15.
- For the command levels 2 to 9 and 11 to 14, no command line exists. The user can add command lines to these command levels to implement refined right management.
Level authorization is classified into local authorization and remote HWTACACS authorization.
Task authorization
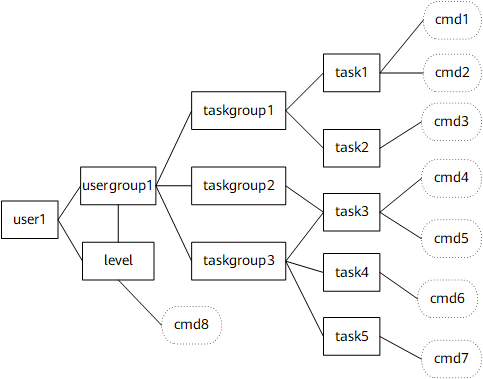
The user can use the task to organize commands (the user cannot customize the task and the commands under the task, as shown by the dotted lines in Figure 3), use the task group to organize tasks, and use the user group to organize task groups. Then, a three-level right control model is formed, and the right control granularity increases in the order of the task, task group, and user group.
- When a user is created, the user group or user level can be specified for the user. Therefore, the command set that the user can run is determined during user creation.
- User authorization is implemented according to the user group or level, and the users in the same user group or of the same level have the same rights.
- The user can configure the command level to adjust the rights.
- The default user groups are automatically mapped to levels 0 to 3, and the customized user groups cannot be mapped to the levels.
The user can customize task groups and user groups. For example, user group 1 is assigned to administrator A to configure and manage OSPF command lines, and the OSPF is controlled as a whole; user group 2 is assigned to administrator B to manage VPN services.
Command-Line Recording
For command-line recording, the command lines run by the user are uploaded to the HWTACACS server based on the HWTACACS protocol. The user can use command-line recording to implement security management.
The difference between command-line recording and operation logs is that command lines run by the user are recorded on the same HWTACACS server whereas operation logs are recorded on different devices.