BFD for BGP Tunnel
Background
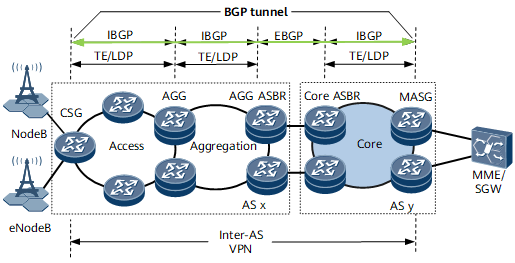
The IP/MPLS network shown in Figure 1 transmits VPN services. PEs, such as a CSG, AGG, ASBR, and MASG, establish multi-segment MPLS tunnels between directly connected devices. In this case, VPN service provision on PEs is complex, and the VPN service scalability decreases. As PEs establish BGP peer relationships, a routing policy can be used to assign MPLS labels for BGP routes so that an E2E BGP tunnel can be established. The BGP tunnel consists of a primary BGP LSP and a backup BGP LSP. VPN services can travel along the E2E BGP tunnel, which simplifies service provision and improves VPN service scalability.
To rapidly detect faults in an E2E BGP tunnel, BFD for BGP tunnel is used. BFD for BGP tunnel establishes a dynamic BFD session, which is also called a BGP BFD session and bound to both the primary and backup BGP LSPs. If both BGP LSPs fail, the BGP BFD session detects the faults and triggers VPN FRR switching.
Usage Scenarios
BFD for BGP tunnel is used in the following scenarios:
Inter-AS VPN Option C scenario
Intra- or inter-AS seamless MPLS scenario
Principles
Dynamic BGP BFD sessions are established using either of the following policies:
Host address-based policy: used when all host addresses are available to trigger the creation of BGP BFD sessions.
IP address prefix list-based policy: used when only some host addresses can be used to establish BFD sessions.
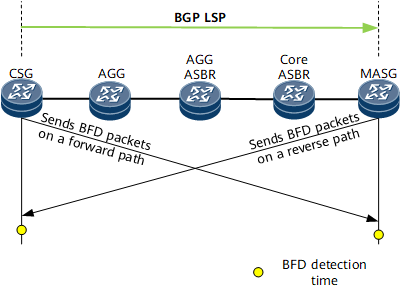
A BGP BFD session working in asynchronous mode monitors BGP LSPs over BGP tunnels. In Figure 2, the ingress (CSG) and egress (MASG) of E2E BGP LSPs exchange BFD packets periodically. Forward BFD packets are forwarded along the BGP LSP, and returned BFD packets are forwarded along an IP route destined for the CSG's LSRID. Therefore, the CSG must be configured to advertise the IP route. If either node receives no BFD packet after a specified detection period elapses, the node considers the BGP LSP faulty. If both the primary and backup BGP LSPs fail, the BGP BFD session triggers VPN FRR switching.