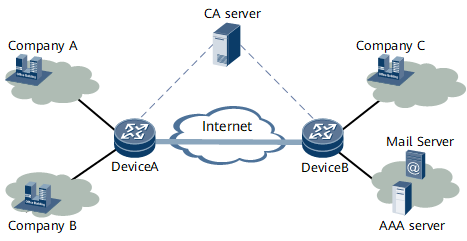
Certificate Application on the IPsec VPN
When a node remotely accesses another node over a VPN, digital certificates can be used to authenticate devices that attempt to communicate with each other.
For example, as shown in Figure1 Certificate application in the IPsec VPN, DeviceA and DeviceB apply for certificates from the same CA server. When an IPsec VPN needs to established for data transmission, between DeviceA and DeviceB, the authentication procedures on them are as follows:
- After the initial communication, the peers share their local certificates.
- They authenticate the signature of the peer's local certificate through the public key of the CA certificate saved locally. When issuing a local certificate, the CA adds a signature to the certificate. Thus, the CA public key in the CA certificate can be adopted for authenticating the signature of the peer's local certificate.
- If the signature passes the authentication, the device compares the current time with the validity period on the certificate. If the current time is within the validity period, the authentication succeeds; otherwise, the authentication fails.
- If CRL authentication is enabled (according to the configuration on the device), the device searches for the serial number of the peer's certificate in the CRL. If the serial number is found, the certificate is invalid and thus the authentication fails; otherwise, the certificate passes the authentication.
Once the certificate passes the authentication, the IPsec VPN will be established between DeviceA and DeviceB.