Principles
On an Internet service provider (ISP) network shown in Figure 1, user-side interfaces on a local device receive a great number of packets to be forwarded to the CPU. Some packets attempt to initiate attacks to the CPU.
Attack packets destined for the CPU on a device pose the following threats to the device:
- A great number of packets sent to the CPU are likely to cause a sharp spike in CPU usage. If the CPU is overloaded, device performance deteriorates, and service interruptions may occur.
- Malicious packets allowed to reach the CPU consume resources, which causes a service interruption or even a system crash.
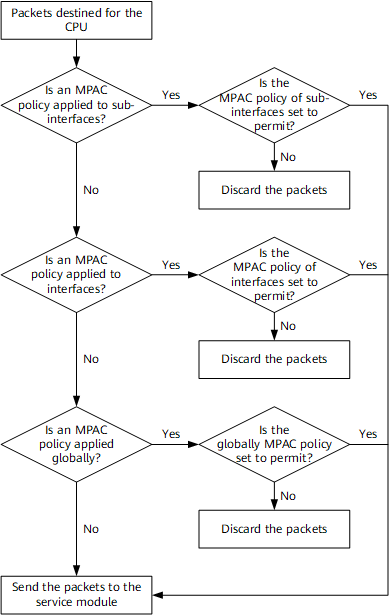
To prevent CPU resource exhaustion and operate a network properly, configure an MPAC policy on sub-interfaces, physical interfaces, and the entire device. The rules in the policy determine whether protocol-specific packets with the specified source and destination addresses can be sent to the service module.
- If packets match a rule and the behavior in the rule is "permit", the packets are sent to the service module for processing.
- If packets match a rule and the behavior in the rule is "deny", the packets are discarded.
- If packets do not match rules in the policy, the packets are sent to the service module for processing.
Figure 2 demonstrates how an MPAC-capable device processes packets. You can define rules in an MPAC policy to meet site-specific requirements.