Whitelist-based Access Control
An IPsec gateway can use a certificate attribute access control policy, which functions similarly as a whitelist, to authenticate the certificate of the IKE peer. However, this method has the following defects:
- Requires great numbers of workloads and difficult management.
- Does not provide exact match of certificates' common names.
The IPsec whitelist function resolves the preceding defects. You can define an IPsec whitelist and import it into a device. The IPsec whitelist function provides exact match of certificates' common names.
When IKE negotiation is implemented before an IPsec tunnel is created, the system checks whether the IPsec whitelist function is enabled. If the IPsec whitelist function is enabled, the system checks whether the common name of the peer end's certificate is whitelisted.
- If the common name of the peer end's certificate is whitelisted, the peer end passes the authentication, and IKE negotiation is allowed to set up an IPsec tunnel.
- If the common name of the peer end's certificate is not whitelisted, the peer end fails the authentication, and IKE negotiation is not allowed. As a result, the IPsec tunnel fails to be set up.
Whitelist files are typically .xml files in the following formats:
<SerialnumberList>
<Serialnumber>CN-on-Certificate_of-RBS-1</Serialnumber>
<Serialnumber>CN-on-Certificate_of-RBS-2</Serialnumber>
¡
<Serialnumber>CN-on-Certificate_of-RBS-n</Serialnumber>
</SerialnumberList>
The character string listed in <Serialnumber></Serialnumber> is the common name of a peer device's certificate.To allow users to update the whitelist as required, the following functions are available:
- Imports a whitelist. If importing a whitelist fails, the system rolls back to the status where the whitelist is not imported.
- Deletes a whitelist.
- Adds incremental content to a whitelist.
- Queries a whitelist.
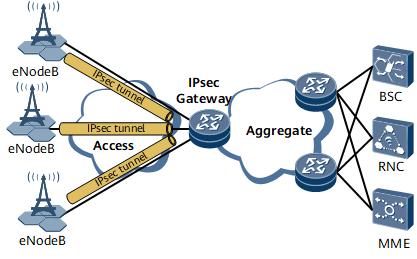
On the network shown in Figure 1, an IPsec tunnel needs to be set up between an eNodeB and an IPsec gateway to ensure secure communications. To prevent an unauthorized device from setting up an IPsec tunnel with the IPsec gateway, configure the IPsec whitelist function on the IPsec gateway so that only whitelisted devices can access the network.