Enhanced IPsec Functions
IPsec Whitelist
- Requires heavy workloads and faces management difficulties.
- Does not support exact match of certificates' common names (CNs).
The IPsec whitelist function can effectively resolve the preceding problems. IPsec whitelists can be defined by users and then imported to a device, and can also support exact match for certificates' CNs.
- If the CN of the peer end's certificate is whitelisted, the peer end passes the check, and IKE negotiation is allowed for IPsec tunnel establishment.
- If the CN of the peer end's certificate is not whitelisted, the peer end fails the check, and IKE negotiation is not allowed. As a result, the IPsec tunnel fails to be set up.
<SerialnumberList>
<Serialnumber>CN-on-Certificate_of-RBS-1</Serialnumber>
<Serialnumber>CN-on-Certificate_of-RBS-2</Serialnumber>
...
<Serialnumber>CN-on-Certificate_of-RBS-n</Serialnumber>
</SerialnumberList>
The character string between <Serialnumber></Serialnumber> is the CN field of the certificate on the device interconnected with the IPsec gateway.- Imports a whitelist. If importing a whitelist fails, the system rolls back to the state where the whitelist is not imported.
- Deletes a whitelist.
- Incrementally adds information to a whitelist.
- Queries a whitelist.
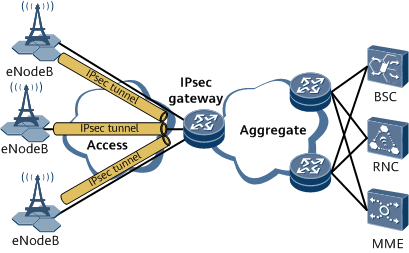
As shown in Figure 1, an IPsec tunnel is established between the eNodeB and IPsec gateway to secure communication. To prevent unauthorized devices from establishing IPsec tunnels with the IPsec gateway, you can configure the whitelist feature on the IPsec gateway in advance to ensure that only devices in the whitelist can access the network.
Automatic IPsec Service Route Generation
When a security policy is used to establish IPsec tunnels, IPsec service route information on the remote end (such as the IP address and interface of the remote end) may not be available. Therefore, static routes cannot be configured manually. In this case, you can enable automatic IPsec service route generation.
When IPsec tunnels are established using a security policy, IPsec service routes will be generated during IPsec negotiation. If you want to configure static routes as IPsec service routes based on your network plan, you need to disable automatic IPsec service route generation.